Question 61
A network analyst is investigating compromised corporate information. The analyst leads to a theory that network traffic was intercepted before being transmitted to the internet. The following output was captured on an internal host:

Based on the IoCS, which of the following was the MOST likely attack used to compromise the network communication?

Based on the IoCS, which of the following was the MOST likely attack used to compromise the network communication?
Question 62
A security engineer needs to implement an MDM solution that complies with the corporate mobile device policy. The policy states that in order for mobile users to access corporate resources on their devices the following requirements must be met:
* Mobile device OSs must be patched up to the latest release
* A screen lock must be enabled (passcode or biometric)
* Corporate data must be removed if the device is reported lost or stolen Which of the following controls should the security engineer configure? (Select TWO)
* Mobile device OSs must be patched up to the latest release
* A screen lock must be enabled (passcode or biometric)
* Corporate data must be removed if the device is reported lost or stolen Which of the following controls should the security engineer configure? (Select TWO)
Question 63
An organization is developing a plan in the event of a complete loss of critical systems and dat
a. Which of the following plans is the organization MOST likely developing?
a. Which of the following plans is the organization MOST likely developing?
Question 64
A recent audit cited a risk involving numerous low-criticality vulnerabilities created by a web application using a third-party library. The development staff state there are still customers using the application even though it is end of life and it would be a substantial burden to update the application for compatibility with more secure libraries. Which of the following would be the MOST prudent course of action?
Question 65
A forensics investigator is examining a number of unauthorized payments that were reported on the
00mpany's website. Some unusual log entries show users received an email for an unwanted mailing list and clicked on a link to attempt to unsubscribe. One of the users reported the email to the phishing team, and the forwarded email revealed the link to be:
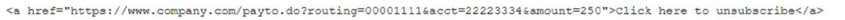
Which of the following will the forensics investigator MOST likely determine has occurred?
00mpany's website. Some unusual log entries show users received an email for an unwanted mailing list and clicked on a link to attempt to unsubscribe. One of the users reported the email to the phishing team, and the forwarded email revealed the link to be:
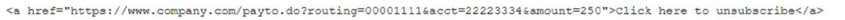
Which of the following will the forensics investigator MOST likely determine has occurred?
Premium Bundle
Newest SY0-601 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing SY0-601 Exam! BraindumpsPass.com now offer the updated SY0-601 exam dumps, the BraindumpsPass.com SY0-601 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com SY0-601 pdf dumps with Exam Engine here:

