Question 81
A user enters a password to log in to a workstation and is then prompted to enter an authentication code. Which of the following MFA factors or attributes are being utilized in the authentication process? (Select TWO).
Question 82
A user reports constant lag and performance issues with the wireless network when working at a local coffee shop. A security analyst walks the user through an installation of Wireshark and get a five-minute pcap to analyze. The analyst observes the following output:

Which of the following attacks does the analyst MOST likely see in this packet capture?

Which of the following attacks does the analyst MOST likely see in this packet capture?
Question 83
A security analyst is reviewing the following attack log output:
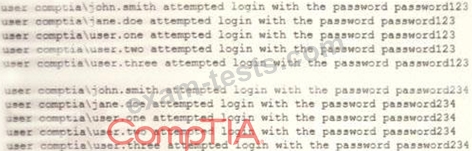
Which of the following types of attacks does this MOST likely represent?

Which of the following types of attacks does this MOST likely represent?
Question 84
A security analyst is running a vulnerability scan to check for missing patches during a suspected security rodent.
During which of the following phases of the response process is this activity MOST likely occurring?
During which of the following phases of the response process is this activity MOST likely occurring?
Question 85
A security analyst is investigation an incident that was first reported as an issue connecting to network shares and the internet, While reviewing logs and tool output, the analyst sees the following:

Which of the following attacks has occurred?

Which of the following attacks has occurred?
Premium Bundle
Newest SY0-601 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing SY0-601 Exam! BraindumpsPass.com now offer the updated SY0-601 exam dumps, the BraindumpsPass.com SY0-601 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com SY0-601 pdf dumps with Exam Engine here:

