Question 201
A security assessment determines DES and 3DES are still being used on recently deployed production servers. Which of the following did the assessment identify?
Question 202
An attacker has successfully exfiltrated several non-salted password hashes from an online system. Given the logs below:

Which of the following BEST describes the type of password attack the attacker is performing?

Which of the following BEST describes the type of password attack the attacker is performing?
Question 203
A company is launching a new internet platform for its clients. The company does not want to implement its own authorization solution but instead wants to rely on the authorization provided by another platform.
Which of the following is the BEST approach to implement the desired solution?
Which of the following is the BEST approach to implement the desired solution?
Question 204
A security analyst has been asked to investigate a situation after the SOC started to receive alerts from the SIEM. The analyst first looks at the domain controller and finds the following events:
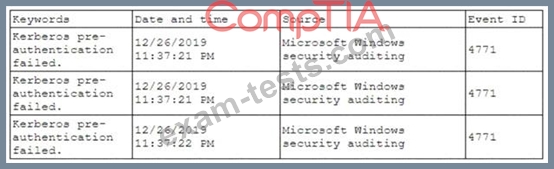
To better understand what is going on, the analyst runs a command and receives the following output:
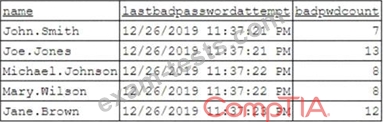
Based on the analyst's findings, which of the following attacks is being executed?

To better understand what is going on, the analyst runs a command and receives the following output:

Based on the analyst's findings, which of the following attacks is being executed?
Question 205
Which of the following is the BEST reason to maintain a functional and effective asset management policy that aids in ensuring the security of an organization?

