Question 216
A security analyst has received several reports of an issue on an internal web application. Users stale they are having to provide their credential twice lo log in. The analyst checks with the application team and notes this is not an expected behavior. After looking at several loos the analyst decades to run some commands on the gateway and obtains the following output Internet address
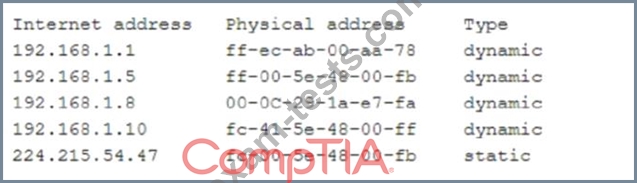
Which of the following BEST describes the attack the company is experiencing?

Which of the following BEST describes the attack the company is experiencing?
Question 217
A network engineer notices the VPN concentrator overloaded and crashes on days when there are a lot of remote workers. Senior management has placed greater importance on the availability of VPN resources for the remote workers than the security of the end users' traffic.
Which of the following would be BEST to solve this issue?
Which of the following would be BEST to solve this issue?
Question 218
A security analyst is reviewing the following command-line output:
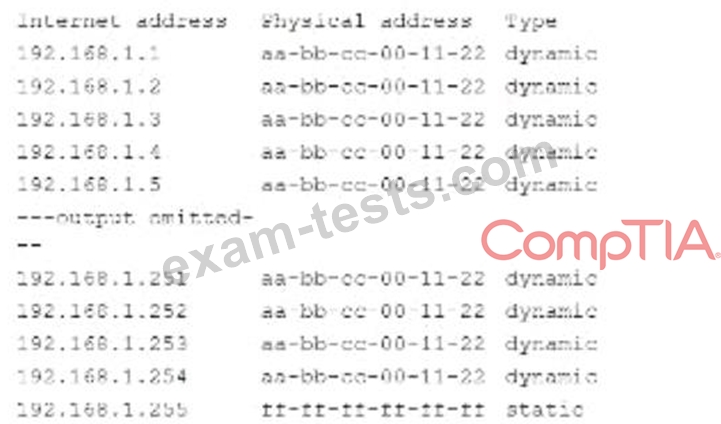
Which of the following Is the analyst observing?

Which of the following Is the analyst observing?
Question 219
A recent security assessment revealed that an actor exploited a vulnerable workstation within an organization and has persisted on the network for several months.
The organization realizes the need to reassess its security strategy for mitigating risks within the perimeter.
Which of the following solutions would BEST support the organization's strategy?
The organization realizes the need to reassess its security strategy for mitigating risks within the perimeter.
Which of the following solutions would BEST support the organization's strategy?
Question 220
Which of the following would BEST identify and remediate a data-loss event in an enterprise using third-party, web-based services and file-sharing platforms?

