Question 241
A security engineer needs to create a network segment that can be used for servers that require connections from untrusted networks When of the following should the engineer implement?
Question 242
A security analyst needs to find real-time data on the latest malware and IoCs. Which of the following would BEST describes the solution the analyst should pursue?
Question 243
Joe. a security analyst, recently performed a network discovery to fully understand his organization's electronic footprint from a "public" perspective. Joe ran a set of commands and received the following output:
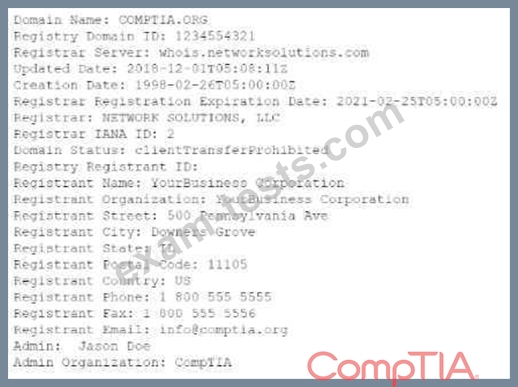
Which of the following can be determined about the organization's public presence and security posture? (Select TWO).

Which of the following can be determined about the organization's public presence and security posture? (Select TWO).
Question 244
A security analyst is preparing a threat for an upcoming internal penetration test. The analyst needs to identify a method for determining the tactics, techniques, and procedures of a threat against the organization's network. Which of the following will the analyst MOST likely use to accomplish the objective?
Question 245
A security analyst notices several attacks are being blocked by the NIPS but does not see anything on the boundary firewall logs. The attack seems to have been thwarted Which of the following resiliency techniques was applied to the network to prevent this attack?

