Question 81
An attack relies on an end user visiting a website the end user would typically visit, however, the site is compromised and uses vulnerabilities in the end users browser to deploy malicious software. Which of the blowing types of attack does this describe?
Question 82
A security administrator is trying to determine whether a server is vulnerable to a range of attacks. After using a tool, the administrator obtains the following output:

Which of the following attacks was successfully implemented based on the output?

Which of the following attacks was successfully implemented based on the output?
Question 83
Several large orders of merchandise were recently purchased on an e-commerce company's website. The totals for each of the transactions were negative values, resulting in credits on the customers' accounts. Which of the following should be implemented to prevent similar situations in the future?
Question 84
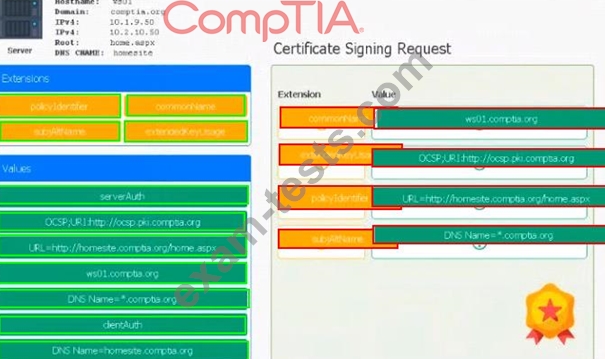
Leveraging the information supplied below, complete the CSR for the server to set up TLS (HTTPS)
* Hostname: ws01
* Domain: comptia.org
* IPv4: 10.1.9.50
* IPV4: 10.2.10.50
* Root: home.aspx
* DNS CNAME:homesite.
Instructions:
Drag the various data points to the correct locations within the CSR. Extension criteria belong in the let hand column and values belong in the corresponding row in the right hand column.
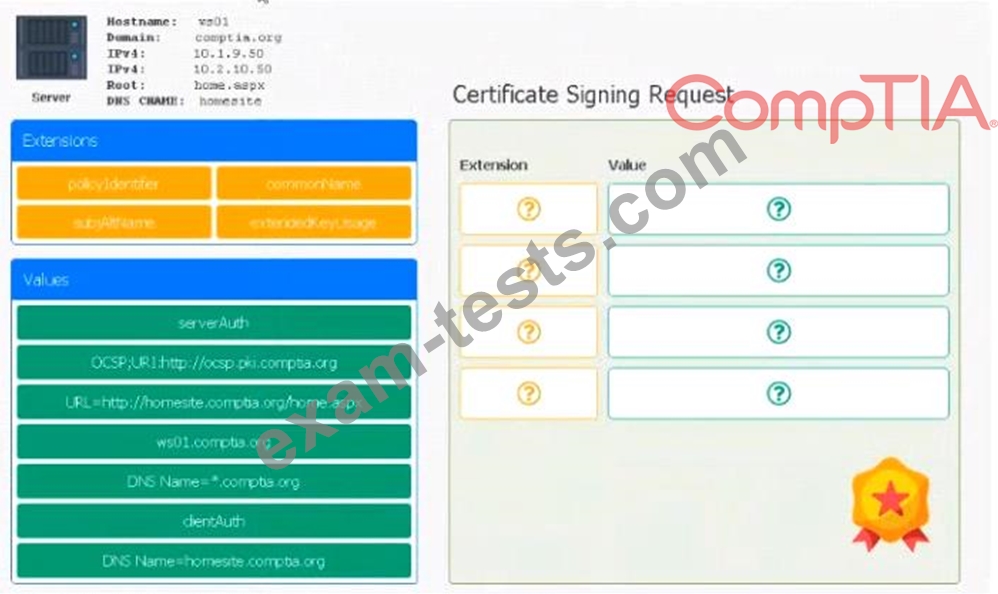
* Hostname: ws01
* Domain: comptia.org
* IPv4: 10.1.9.50
* IPV4: 10.2.10.50
* Root: home.aspx
* DNS CNAME:homesite.
Instructions:
Drag the various data points to the correct locations within the CSR. Extension criteria belong in the let hand column and values belong in the corresponding row in the right hand column.

Question 85
Which of the following BEST describes a security exploit for which a vendor patch is not readily available?
Premium Bundle
Newest SY0-601 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing SY0-601 Exam! BraindumpsPass.com now offer the updated SY0-601 exam dumps, the BraindumpsPass.com SY0-601 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com SY0-601 pdf dumps with Exam Engine here: