Question 86
A user reports constant lag and performance issues with the wireless network when working at a local coffee shop. A security analyst walks the user through an installation of Wireshark and get a five-minute pcap to analyze. The analyst observes the following output:

Which of the following attacks does the analyst MOST likely see in this packet capture?

Which of the following attacks does the analyst MOST likely see in this packet capture?
Question 87
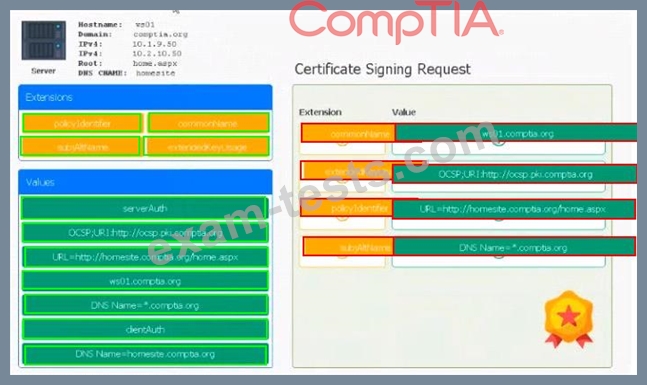
Leveraging the information supplied below, complete the CSR for the server to set up TLS (HTTPS)
* Hostname: ws01
* Domain: comptia.org
* IPv4: 10.1.9.50
* IPV4: 10.2.10.50
* Root: home.aspx
* DNS CNAME:homesite.
Instructions:
Drag the various data points to the correct locations within the CSR. Extension criteria belong in the let hand column and values belong in the corresponding row in the right hand column.
* Hostname: ws01
* Domain: comptia.org
* IPv4: 10.1.9.50
* IPV4: 10.2.10.50
* Root: home.aspx
* DNS CNAME:homesite.
Instructions:
Drag the various data points to the correct locations within the CSR. Extension criteria belong in the let hand column and values belong in the corresponding row in the right hand column.

Question 88
A security engineer is setting up passwordless authentication for the first time.
INSTRUCTIONS
Use the minimum set of commands to set this up and verify that it works. Commands cannot be reused.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.

INSTRUCTIONS
Use the minimum set of commands to set this up and verify that it works. Commands cannot be reused.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.

Question 89
Which of the following provides a calculated value for known vulnerabilities so organizations can prioritize mitigation steps?
Question 90
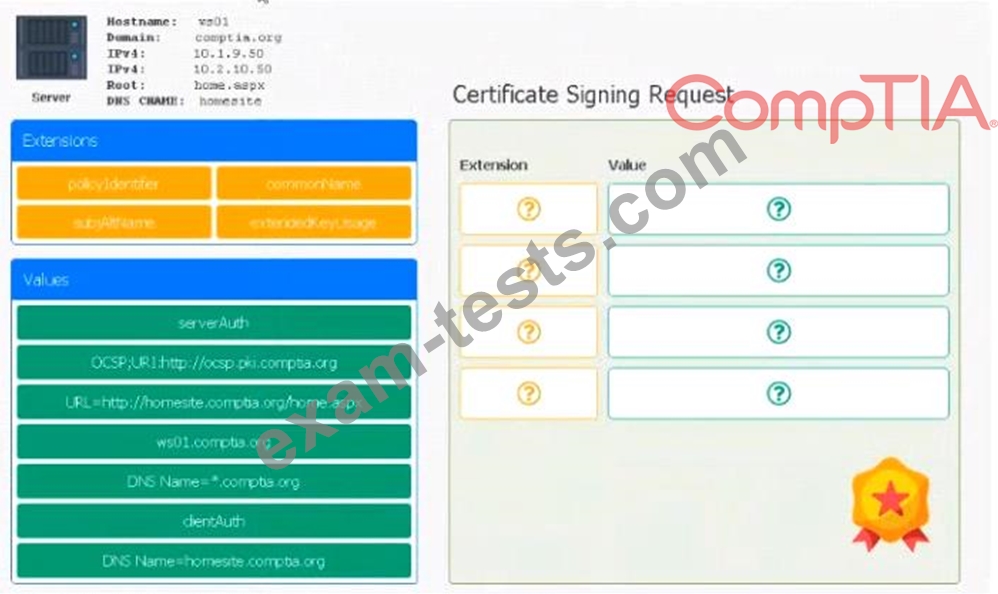
Leveraging the information supplied below, complete the CSR for the server to set up TLS (HTTPS)
* Hostname: ws01
* Domain: comptia.org
* IPv4: 10.1.9.50
* IPV4: 10.2.10.50
* Root: home.aspx
* DNS CNAME:homesite.
Instructions:
Drag the various data points to the correct locations within the CSR. Extension criteria belong in the let hand column and values belong in the corresponding row in the right hand column.

* Hostname: ws01
* Domain: comptia.org
* IPv4: 10.1.9.50
* IPV4: 10.2.10.50
* Root: home.aspx
* DNS CNAME:homesite.
Instructions:
Drag the various data points to the correct locations within the CSR. Extension criteria belong in the let hand column and values belong in the corresponding row in the right hand column.

Premium Bundle
Newest SY0-601 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing SY0-601 Exam! BraindumpsPass.com now offer the updated SY0-601 exam dumps, the BraindumpsPass.com SY0-601 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com SY0-601 pdf dumps with Exam Engine here: