Question 16
In which of the following risk management strategies would cybersecurity insurance be used?
Question 17
A malware attack has corrupted 30TB of company data across all file servers A systems administrator Identifies the malware and contains the Issue, but the data Is unrecoverable. The administrator Is not concerned about the data loss because the company has a system in place that will allow users to access the data that was backed up last night. Which of the following resiliency techniques did the administrator MOST likely use to prevent impacts to business operations after an attack?
Question 18
Which of the following is the MOST relevant security check to be performed before embedding third-parry libraries in developed code?
Question 19
Phone number, address, and date of birth be provided to confirm Joe's identity before sending him the prize. Which of the following BEST describes this type of email?
Question 20
A company is setting up a web server on the Internet that will utilize both encrypted and unencrypted web-browsing protocols. A security engineer runs a port scan against the server from the Internet and sees the following output:
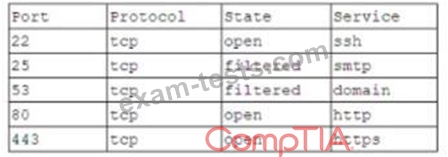
Which of the following steps would be best for the security engineer to take NEXT?

Which of the following steps would be best for the security engineer to take NEXT?
Premium Bundle
Newest SY0-601 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing SY0-601 Exam! BraindumpsPass.com now offer the updated SY0-601 exam dumps, the BraindumpsPass.com SY0-601 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com SY0-601 pdf dumps with Exam Engine here:

