Question 31
A security administrator checks the table of a network switch, which shows the following output:

Which of the following is happening to this switch?

Which of the following is happening to this switch?
Question 32
A security engineer obtained the following output from a threat intelligence source that recently performed an attack on the company's server:

Which of the following BEST describes this kind of attack?

Which of the following BEST describes this kind of attack?
Question 33
An organization has implemented a two-step verification process to protect user access to data that 6 stored in the could. Each employee now uses an email address of mobile number a code to access the data.
Which of the following authentication methods did the organization implement?
Which of the following authentication methods did the organization implement?
Question 34
A security analyst receives a SIEM alert that someone logged in to the appadmin test account, which is only used for the early detection of attacks. The security analyst then reviews the following application log:
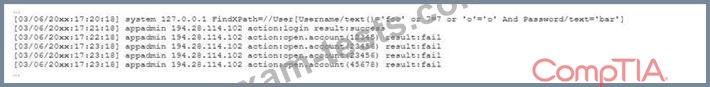
Which of the following can the security analyst conclude?

Which of the following can the security analyst conclude?
Question 35
A cloud service provider has created an environment where customers can connect existing local networks to the cloud for additional computing resources and block internal HR applications from reaching the cloud. Which of the following cloud models is being used?
Premium Bundle
Newest SY0-601 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing SY0-601 Exam! BraindumpsPass.com now offer the updated SY0-601 exam dumps, the BraindumpsPass.com SY0-601 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com SY0-601 pdf dumps with Exam Engine here:

