Question 6
A tax organization is working on a solution to validate the online submission of documents The solution should be earned on a portable USB device that should be inserted on any computer that is transmitting a transaction securely. Which of the following is the BEST certificate for these requirements?
Question 7
During a recent incident an external attacker was able to exploit an SMB vulnerability over the internet. Which of the following action items should a security analyst perform FIRST to prevent this from occurring again?
Question 8
An engineer wants to inspect traffic to a cluster of web servers in a cloud environment. Which of the following solutions should the engineer implement?
Question 9
During an incident response, an analyst applied rules to all inbound traffic on the border firewall and implemented ACLs on each critical server Following an investigation, the company realizes it is still vulnerable because outbound traffic is not restricted and the adversary is able lo maintain a presence in the network. In which of the following stages of the Cyber Kill Chain is the adversary currently operating?
Question 10
Security analysts are conducting an investigation of an attack that occurred inside the organization's network. An attacker was able to connect network traffic between workstation throughout the network. The analysts review the following logs:
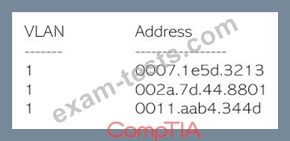
The layer 2 address table has hundred of entries similar to the ones above. Which of the following attacks has MOST likely occurred?

The layer 2 address table has hundred of entries similar to the ones above. Which of the following attacks has MOST likely occurred?
Premium Bundle
Newest SY0-601 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing SY0-601 Exam! BraindumpsPass.com now offer the updated SY0-601 exam dumps, the BraindumpsPass.com SY0-601 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com SY0-601 pdf dumps with Exam Engine here:

