Question 11
An analyst receives multiple alerts for beaconing activity for a host on the network, After analyzing the activity, the analyst observes the following activity:
* A user enters comptia.org into a web browser.
* The website that appears is not the comptia.org site.
* The website is a malicious site from the attacker.
* Users in a different office are not having this issue.
Which of the following types of attacks was observed?
* A user enters comptia.org into a web browser.
* The website that appears is not the comptia.org site.
* The website is a malicious site from the attacker.
* Users in a different office are not having this issue.
Which of the following types of attacks was observed?
Question 12
The Chief Compliance Officer from a bank has approved a background check policy for all new hires Which of the following is the policy MOST likely protecting against?
Question 13
Which of the following components can be used to consolidate and forward inbound Internet traffic to multiple cloud environments though a single firewall?
Question 14
A security incident has been resolved Which of the following BEST describes the importance of the final phase of the incident response plan?
Question 15
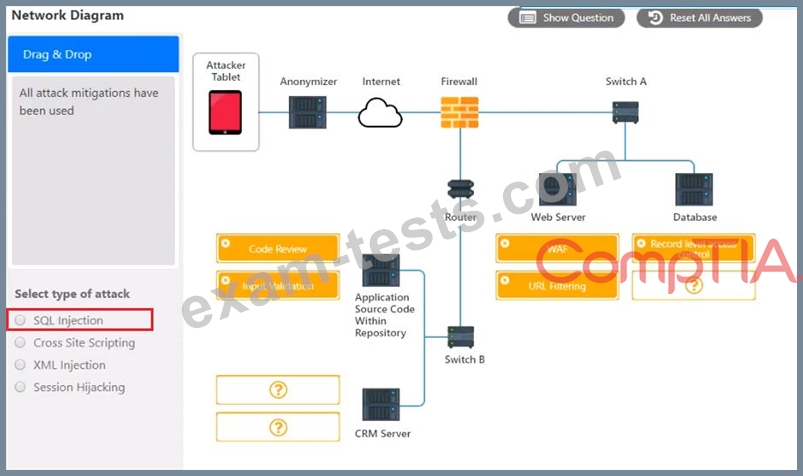
DRAG DROP
An attack has occurred against a company.
INSTRUCTIONS
You have been tasked to do the following:
Identify the type of attack that is occurring on the network by clicking on the attacker's tablet and reviewing the output. (Answer Area 1).
Identify which compensating controls should be implemented on the assets, in order to reduce the effectiveness of future attacks by dragging them to the correct server.
(Answer area 2) All objects will be used, but not all placeholders may be filled. Objects may only be used once.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
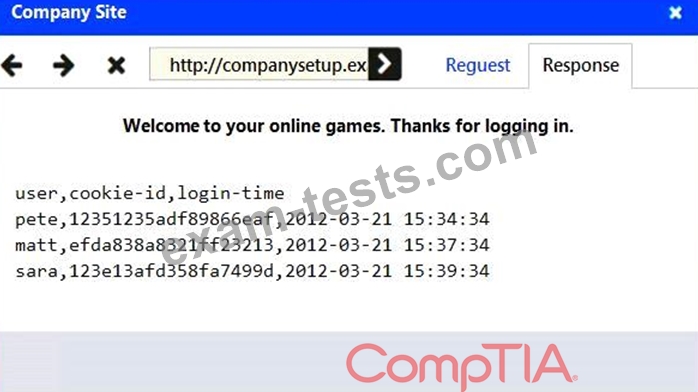
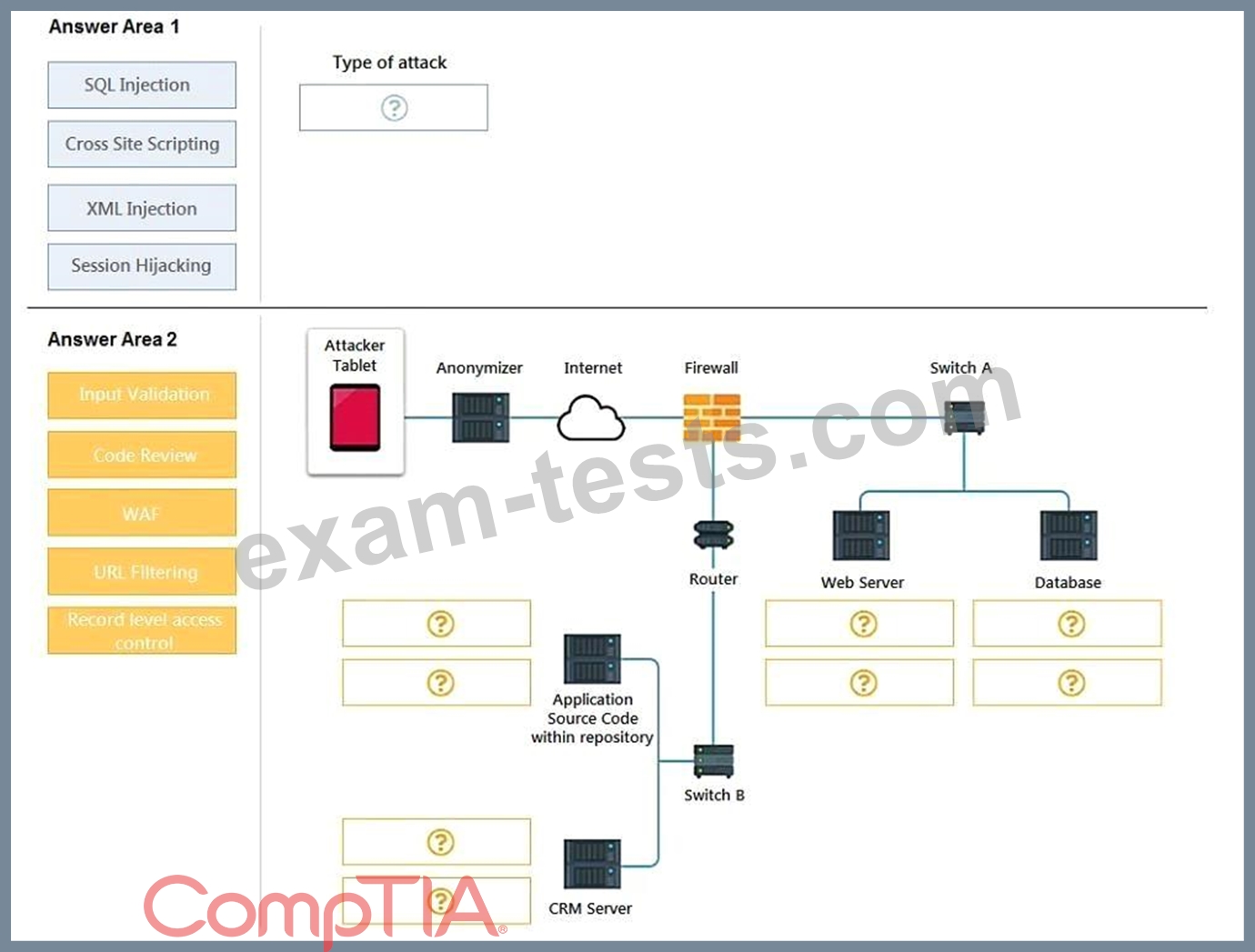
An attack has occurred against a company.
INSTRUCTIONS
You have been tasked to do the following:
Identify the type of attack that is occurring on the network by clicking on the attacker's tablet and reviewing the output. (Answer Area 1).
Identify which compensating controls should be implemented on the assets, in order to reduce the effectiveness of future attacks by dragging them to the correct server.
(Answer area 2) All objects will be used, but not all placeholders may be filled. Objects may only be used once.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.