Question 66
Which of the following is an example of transference of risk?
Question 67
A penetration tester is fuzzing an application to identify where the EIP of the stack is located on memory. Which of the following attacks is the penetration tester planning to execute?
Question 68
A security architect is required to deploy to conference rooms some workstations that will allow sensitive data to be displayed on large screens. Due to the nature of the data, it cannot be stored in the conference rooms. The fiieshare is located in a local data center. Which of the following should the security architect recommend to BEST meet the requirement?
Question 69
A security analyst is receiving numerous alerts reporting that the response time of an internet-facing application has been degraded However, the internal network performance was not degraded. Which of the following MOST likely explains this behavior?
Question 70
A security analyst is investigating some users who are being redirected to a fake website that resembles www.comptia.org. The following output was found on the naming server of the organization:
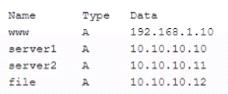
Which of the following attacks has taken place?

Which of the following attacks has taken place?

