Question 31
An organization has activated an incident response plan due to a malware outbreak on its network The organization has brought in a forensics team that has identified an internet-facing Windows server as the likely point of initial compromise The malware family that was detected is known to be distributed by manually logging on to servers and running the malicious code Which of the following actions would be BEST to prevent reinfection from the initial infection vector?
Question 32
Certain users are reporting their accounts are being used to send unauthorized emails and conduct suspicious activities After further investigation, a security analyst notices the following
* All users share workstations throughout the day
* Endpoint protection was disabled on several workstations throughout the network.
* Travel times on logins from the affected users are impossible
* Sensitive data is being uploaded to external sites
* All usee account passwords were forced lo be reset and the issue continued Which of the following attacks is being used to compromise the user accounts?
* All users share workstations throughout the day
* Endpoint protection was disabled on several workstations throughout the network.
* Travel times on logins from the affected users are impossible
* Sensitive data is being uploaded to external sites
* All usee account passwords were forced lo be reset and the issue continued Which of the following attacks is being used to compromise the user accounts?
Question 33
A security analyst is designing the appropnate controls to limit unauthorized access to a physical site The analyst has a directive to utilize the lowest possible budget Which of the following would BEST meet the requirements?
Question 34
Which of the following should an organization consider implementing In the event executives need to speak to the media after a publicized data breach?
Question 35
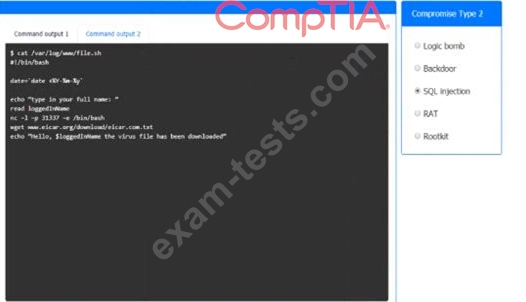
An incident has occurred in the production environment.
Analyze the command outputs and identify the type of compromise.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
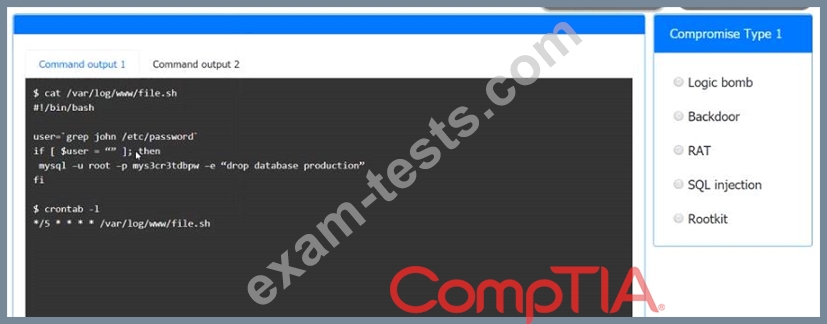
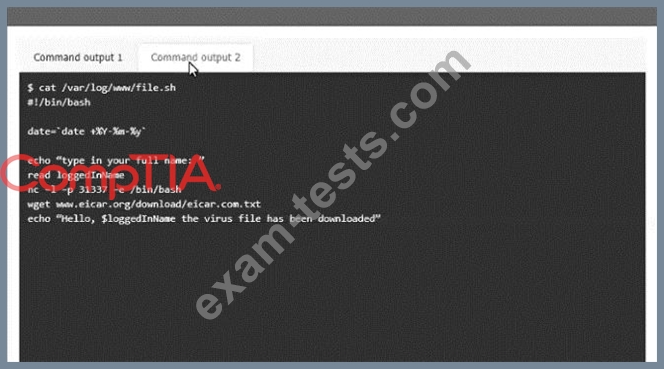
Analyze the command outputs and identify the type of compromise.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.