Question 16
A forensics investigator is examining a number of unauthorized payments the were reported on the company's website. Some unusual log entries show users received an email for an unwanted mailing list and clicked on a link to attempt to unsubscribe. One of the users reported the email to the phishing team, and the forwarded email revealed the link to be:
<a href-"https://www.company.com/payto.do?routing=00001111&accc=22223334&amount-250">Click here to unsubscribe</a> Which of the following will the forensics investigator MOST likely determine has occurred?
<a href-"https://www.company.com/payto.do?routing=00001111&accc=22223334&amount-250">Click here to unsubscribe</a> Which of the following will the forensics investigator MOST likely determine has occurred?
Question 17
A systems administrator reports degraded performance on a virtual server. The administrator increases the virtual memory allocation which improves conditions, but performance degrades again after a few days. The administrator runs an anarysis tool and sees the following output:
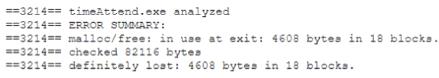
The administrator terminates the timeAttend.exe observes system performance over the next few days, and notices that the system performance does not degrade Which of the following issues is MOST likely occurring?

The administrator terminates the timeAttend.exe observes system performance over the next few days, and notices that the system performance does not degrade Which of the following issues is MOST likely occurring?
Question 18
An engineer recently deployed a group of 100 web servers in a cloud environment. Per the security policy, all web-server ports except 443 should be disabled. Which of the following can be used to accomplish this task?
Question 19
The Chief Information Security Officer (CISO) has requested that a third-party vendor provide supporting documents that show proper controls are in place to protect customer dat a. Which of the following would be BEST for the third-party vendor to provide to the CISO?
Question 20
A DBA reports that several production server hard drives were wiped over the weekend. The DBA also reports that several Linux servers were unavailable due to system files being deleted unexpectedly. A security analyst verified that software was configured to delete data deliberately from those servers. No backdoors to any servers were found. Which of the following attacks was MOST likely used to cause the data toss?

