Question 11
Which of the following scenarios describes a possible business email compromise attack?
Question 12
A security administrator recently reset local passwords and the following values were recorded in the system:
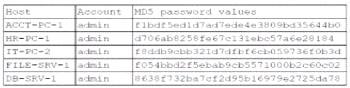
Which of the following in the security administrator most likely protecting against?

Which of the following in the security administrator most likely protecting against?
Question 13
Which of the following incident response activities ensures evidence is properly handied?
Question 14
A user is requesting Telnet access to manage a remote development web server. Insecure protocols are not allowed for use within any environment. Which of the following should be configured to allow remote access to this server?
Question 15
Users at a company are reporting they are unable to access the URL for a new retail website because it is flagged as gambling and is being blocked.
Which of the following changes would allow users to access the site?
Which of the following changes would allow users to access the site?

