Question 26
A security administrator discovers that an attack has been completed against a node on the corporate network.
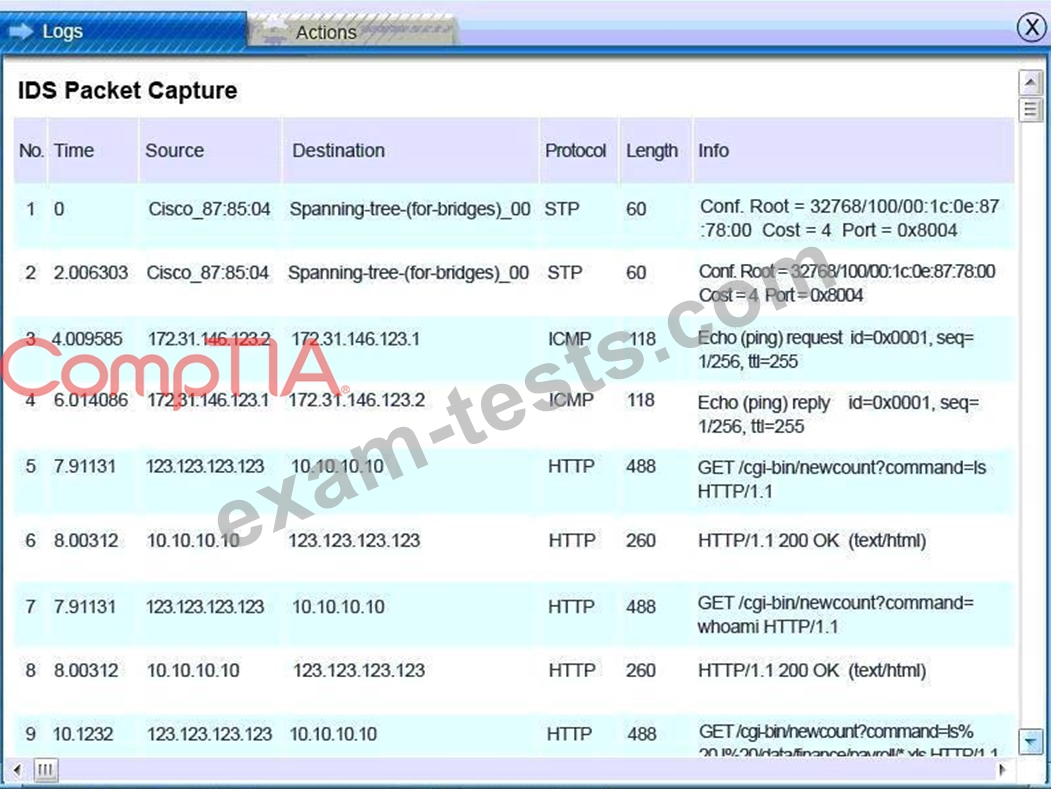
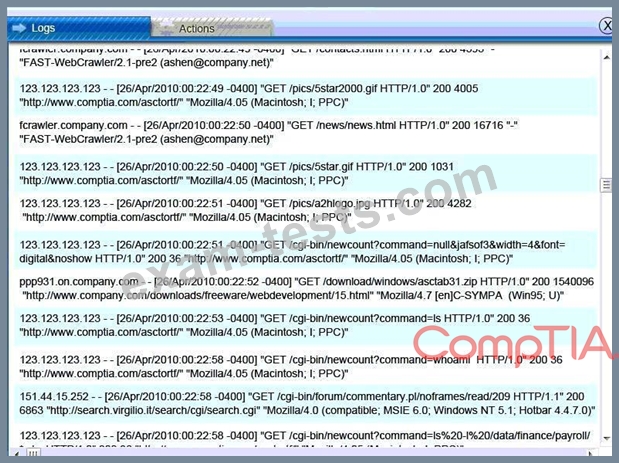
All available logs were collected and stored.
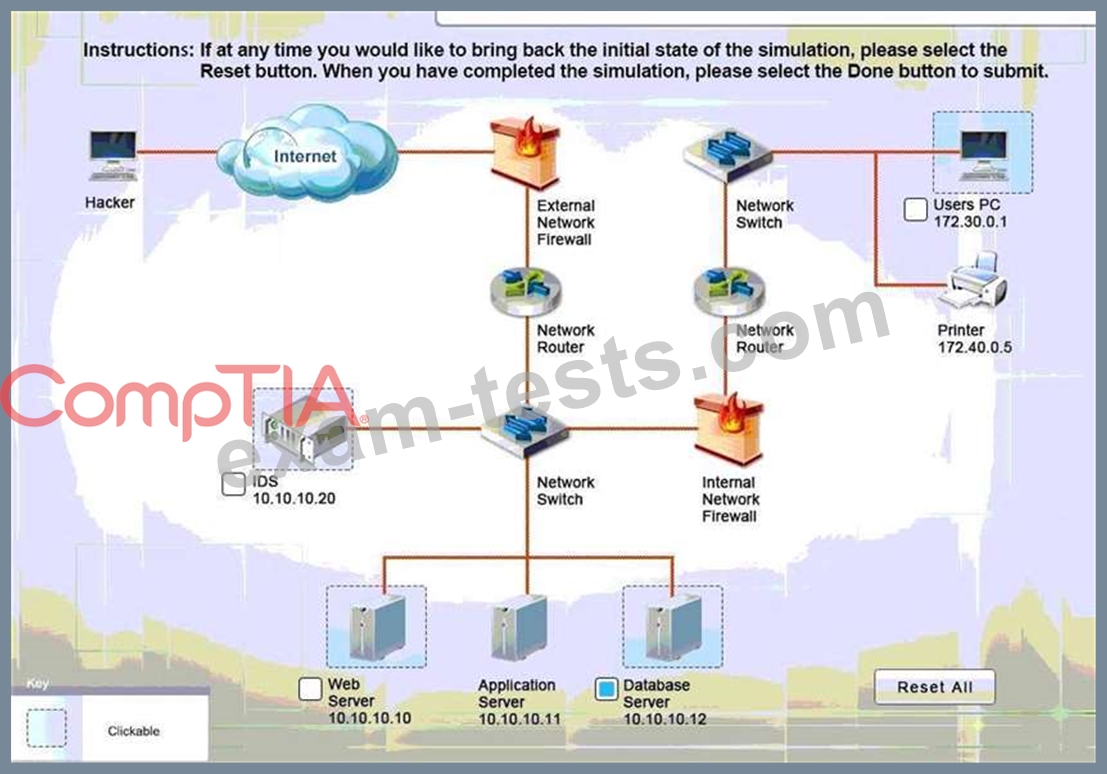
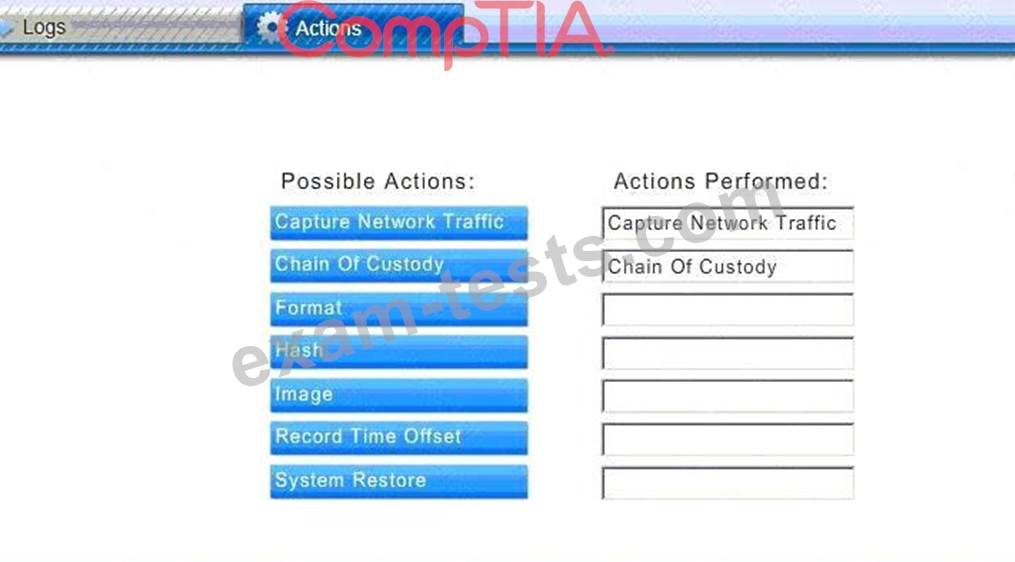
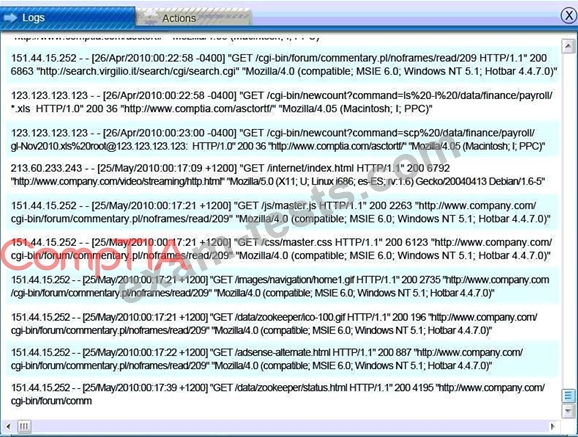
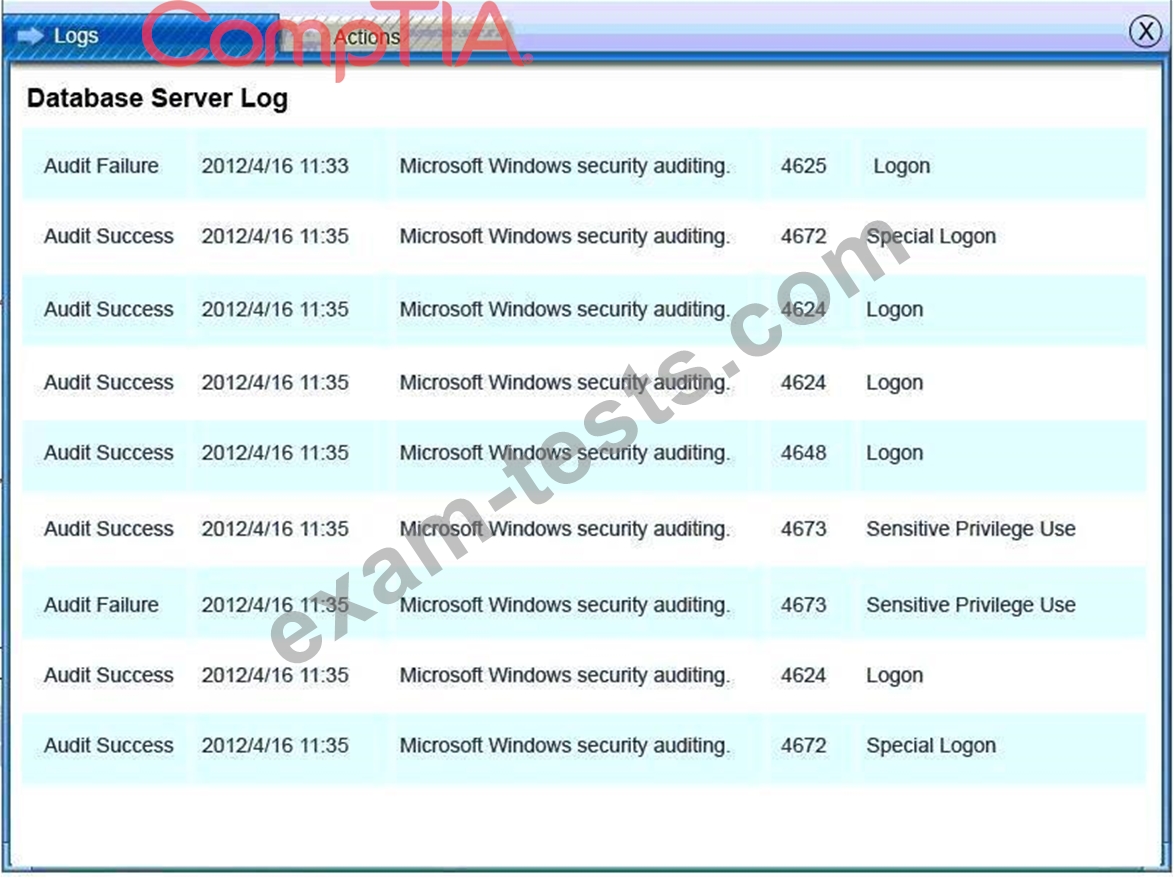
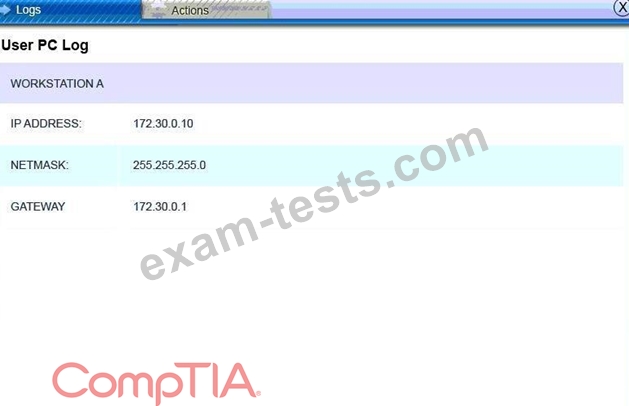
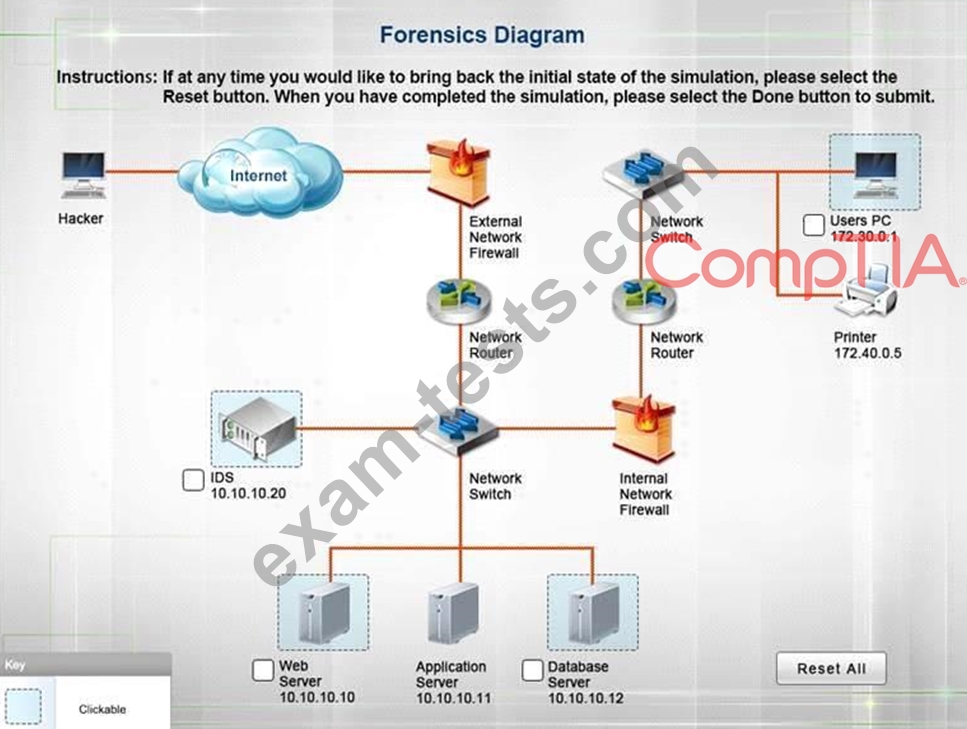
You must review all network logs to discover the scope of the attack, check the box of the node(s) that have been compromised and drag and drop the appropriate actions to complete the incident response on the network. The environment is a critical production environment; perform the LEAST disruptive actions on the network, while still performing the appropriate incid3nt responses.
Instructions: The web server, database server, IDS, and User PC are clickable. Check the box of the node(s) that have been compromised and drag and drop the appropriate actions to complete the incident response on the network. Not all actions may be used, and order is not important. If at any time you would like to bring back the initial state of the simulation, please select the Reset button. When you have completed the simulation, please select the Done button to submit. Once the simulation is submitted, please select the Next button to continue.
All available logs were collected and stored.
You must review all network logs to discover the scope of the attack, check the box of the node(s) that have been compromised and drag and drop the appropriate actions to complete the incident response on the network. The environment is a critical production environment; perform the LEAST disruptive actions on the network, while still performing the appropriate incid3nt responses.
Instructions: The web server, database server, IDS, and User PC are clickable. Check the box of the node(s) that have been compromised and drag and drop the appropriate actions to complete the incident response on the network. Not all actions may be used, and order is not important. If at any time you would like to bring back the initial state of the simulation, please select the Reset button. When you have completed the simulation, please select the Done button to submit. Once the simulation is submitted, please select the Next button to continue.

Question 27
During a data breach cleanup, it is discovered that not all of the sites involved have the necessary data wiping tools. The necessary tools are quickly distributed to the required technicians, but when should this problem BEST be revisited?
Question 28
Which of the following involves the use of targeted and highly crafted custom attacks against a population of users who may have access to a particular service or program?
Question 29
Ann, a new employee, received an email an unknown source indicating she needed to click on the provided link to update her company's profile. Once Ann clicked the link a command prompt appeared with the following output.
C:\ users\Ann\Documents\File1.pgp
C:\ users\Ann\Documents\AdvertisingReport.pgp
C:\ users\Ann\Documents\FinancialReport.pgp
Which of the following types of malware was executed?
C:\ users\Ann\Documents\File1.pgp
C:\ users\Ann\Documents\AdvertisingReport.pgp
C:\ users\Ann\Documents\FinancialReport.pgp
Which of the following types of malware was executed?
Question 30
Which of the following are considered to be "something you do"? (Choose two.)
Premium Bundle
Newest SYO-501 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing SYO-501 Exam! BraindumpsPass.com now offer the updated SYO-501 exam dumps, the BraindumpsPass.com SYO-501 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com SYO-501 pdf dumps with Exam Engine here: