Question 46
Which of the following characteristics differentiate a rainbow table attack from a brute force attack?
(Select two.)
(Select two.)
Question 47
A security technician would like to obscure sensitive data within a file so that it can be transferred without causing suspicion. Which of the following technologies would BEST be suited to accomplish this?
Question 48
A botnet has hit a popular website with a massive number of GRE-encapsulated packets to perform a DDoS attack News outlets discover a certain type of refrigerator was exploited and used to send outbound packets to the website that crashed.
To which of the following categories does the refrigerator belong?
To which of the following categories does the refrigerator belong?
Question 49
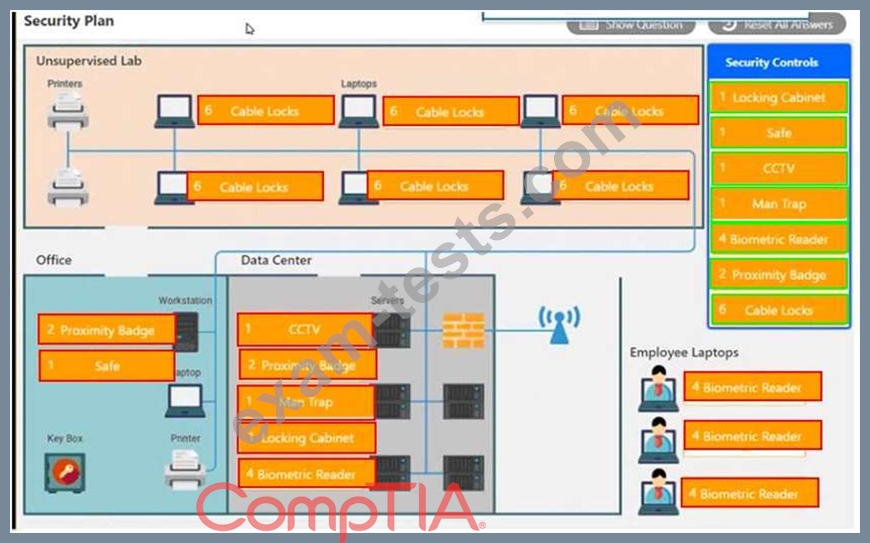
You have been tasked with designing a security plan for your company. Drag and drop the appropriate security controls on the floor plan.
Instructions: All objects must be used and all place holders must be filled. Order does not matter. When you have completed the simulation, please select the Done button to submit.
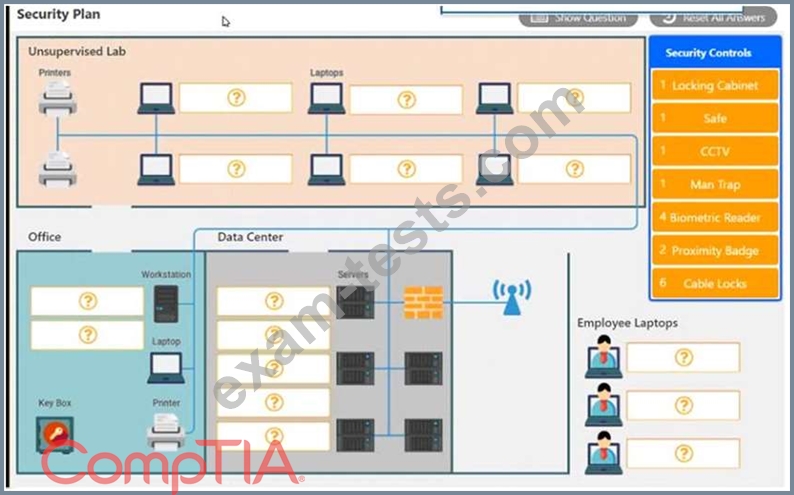
Instructions: All objects must be used and all place holders must be filled. Order does not matter. When you have completed the simulation, please select the Done button to submit.

Question 50
A member of the human resources department is searching for candidate resumes and encounters the following error message when attempting to access popular job search websites:
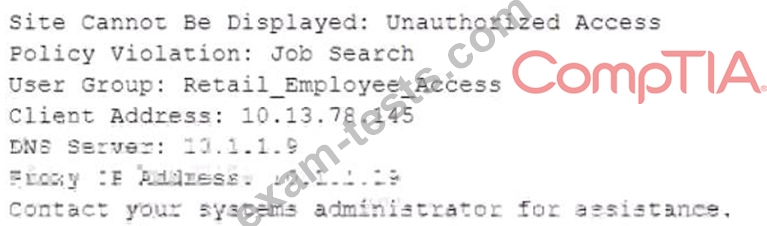
Which of the following would resolve this issue without compromising the company's security policies?

Which of the following would resolve this issue without compromising the company's security policies?