Question 86
Which steps are required to activate Malware Prevention on the NSX Application Platform?
Question 87
Which two statements are true about IDS Signatures? (Choose two.)
Question 88
A company security policy requires all users to log Into applications using a centralized authentication system.
Which two authentication, authorization, and accounting (AAA) systems are available when Integrating NSX with VMware Identity Manager? (Choose two.)
Which two authentication, authorization, and accounting (AAA) systems are available when Integrating NSX with VMware Identity Manager? (Choose two.)
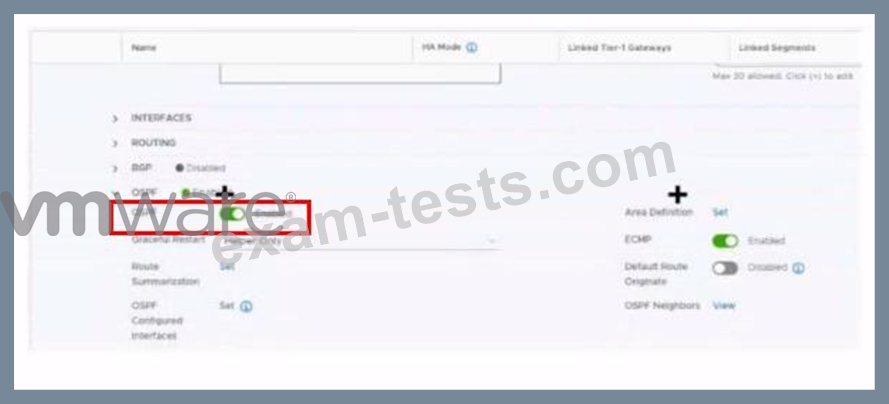
Question 89
Refer to the exhibit.
Which two items must be configured to enable OSPF for the Tler-0 Gateway in the Image? Mark your answers by clicking twice on the image.
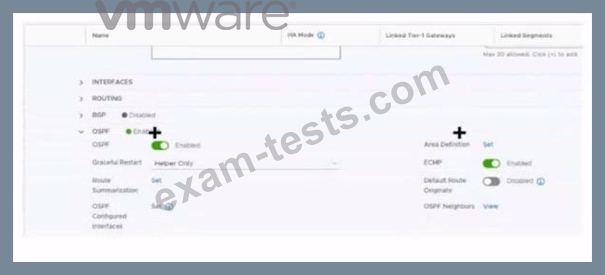
Which two items must be configured to enable OSPF for the Tler-0 Gateway in the Image? Mark your answers by clicking twice on the image.

Question 90
Which three of the following describe the Border Gateway Routing Protocol (BGP) configuration on a Tier-0 Gateway? (Choose three.)