Question 31
Drag and Drop the IPv6 First-Hop Security features from the left onto the definitions on the right.


Question 32
In which two ways does the IPv6 First-Hop Security Binding Table operate? (Choose two.)
Question 33
Refer to the exhibit.
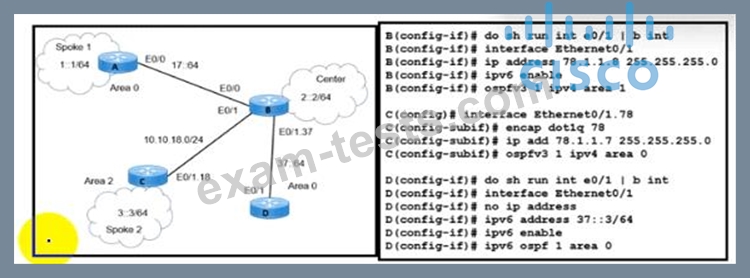
Refer to the exhibit. A network engineer receives a report that Spoke 1 users can perform bank transactions with the server located at the Center site, but Spoke 2 users cannot. Which action resolves the issue?

Refer to the exhibit. A network engineer receives a report that Spoke 1 users can perform bank transactions with the server located at the Center site, but Spoke 2 users cannot. Which action resolves the issue?
Question 34
Refer to Exhibit.

Which two configurations allow clients to get dynamic ip addresses assigned?

Which two configurations allow clients to get dynamic ip addresses assigned?
Question 35
Refer to the exhibit.
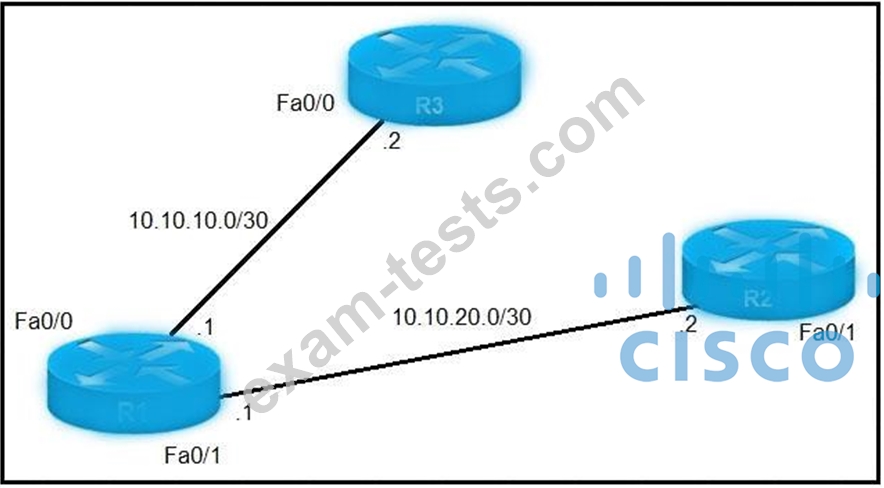
An IP SLA was configured on router R1 that allows the default route to be modified in the event that Fa0/0 loses reachability with the router R3 Fa0/0 interface. The route has changed to flow through router R2. Which debug command is used to troubleshoot this issue?

An IP SLA was configured on router R1 that allows the default route to be modified in the event that Fa0/0 loses reachability with the router R3 Fa0/0 interface. The route has changed to flow through router R2. Which debug command is used to troubleshoot this issue?


