Question 36
Refer to the exhibit.
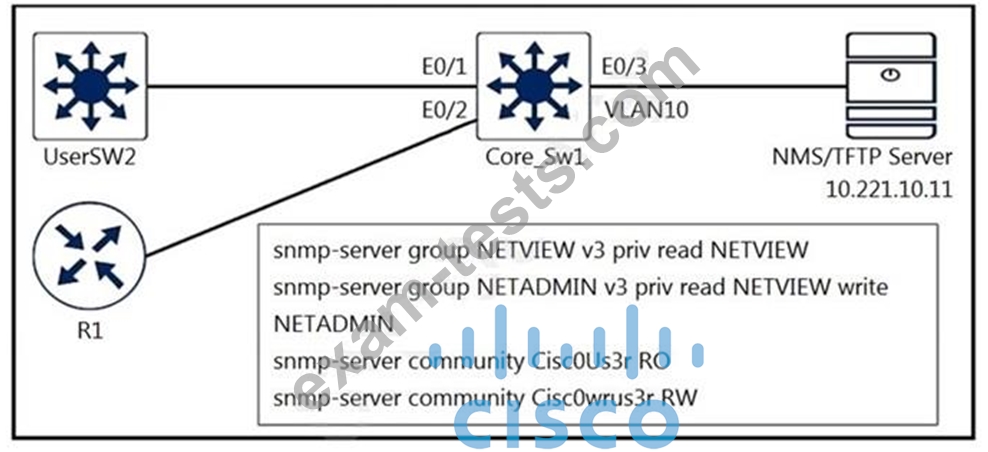
A junior engineer configured SNMP to network devices. Malicious users have uploaded different configurations to the network devices using SNMP and TFTP servers.
Which configuration prevents changes from unauthorized NMS and TFTP servers?

A junior engineer configured SNMP to network devices. Malicious users have uploaded different configurations to the network devices using SNMP and TFTP servers.
Which configuration prevents changes from unauthorized NMS and TFTP servers?
Question 37
Refer to the exhibit.

An engineer is troubleshooting BGP on a device but discovers that the clock on the device does not correspond to the time stamp of the log entries Which action ensures consistency between the two times?

An engineer is troubleshooting BGP on a device but discovers that the clock on the device does not correspond to the time stamp of the log entries Which action ensures consistency between the two times?
Question 38
Refer to the exhibit.
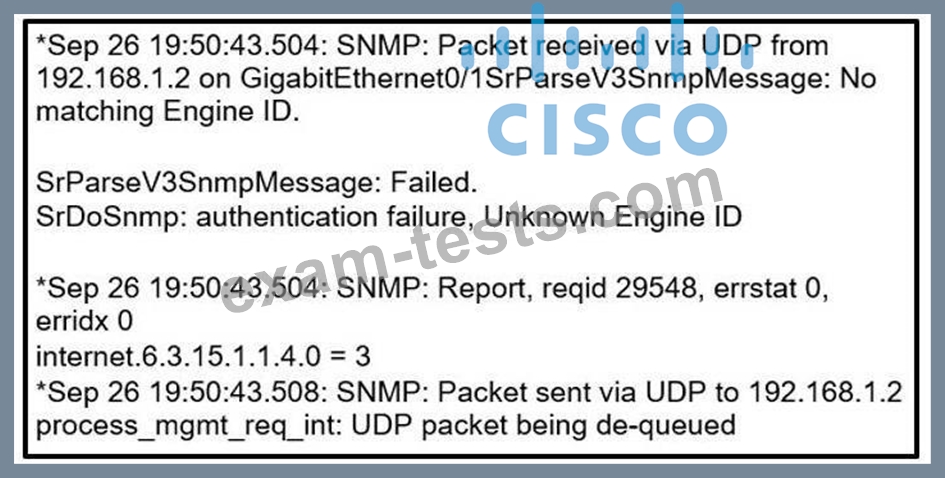
Which two commands provide the administrator with the information needed to resolve the issue? (Choose two.)

Which two commands provide the administrator with the information needed to resolve the issue? (Choose two.)
Question 39
Refer to the exhibit.

Which action resolves the failed authentication attempt to the router?

Which action resolves the failed authentication attempt to the router?
Question 40
Refer to the exhibit.

R6 should reach R1 via R5>R2>R1. Which action resolves the issue?

R6 should reach R1 via R5>R2>R1. Which action resolves the issue?

