Question 11
Which of the following formula is used to calculate the EPS of the organization?
Question 12
Which of the following command is used to enable logging in iptables?
Question 13
What is the correct sequence of SOC Workflow?
Question 14
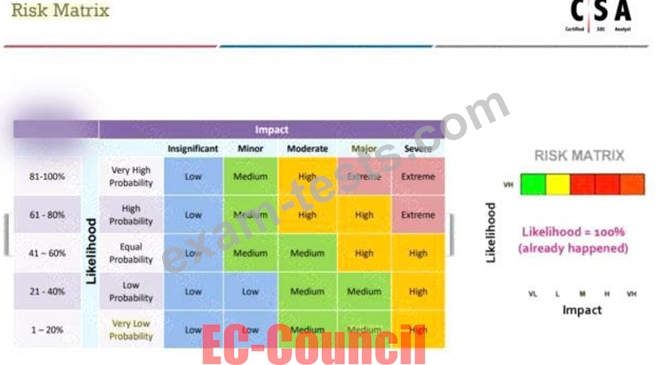
According to the Risk Matrix table, what will be the risk level when the probability of an attack is very low and the impact of that attack is major?
Question 15
Properly applied cyber threat intelligence to the SOC team help them in discovering TTPs.
What does these TTPs refer to?
What does these TTPs refer to?