Question 31
Which of the following tool is used to recover from web application incident?
Question 32
A type of threat intelligent that find out the information about the attacker by misleading them is known as
.
.
Question 33
In which phase of Lockheed Martin's - Cyber Kill Chain Methodology, adversary creates a deliverable malicious payload using an exploit and a backdoor?
Question 34
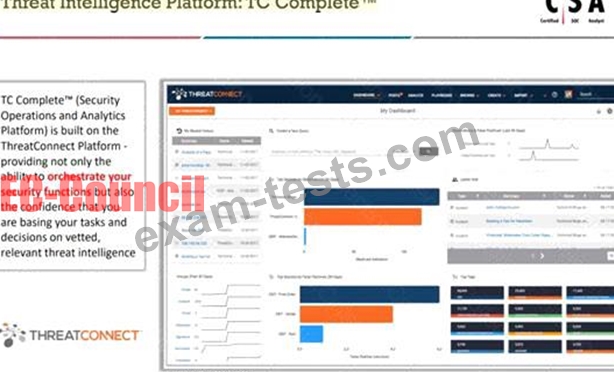
Which of the following is a Threat Intelligence Platform?
Question 35
An organization is implementing and deploying the SIEM with following capabilities.
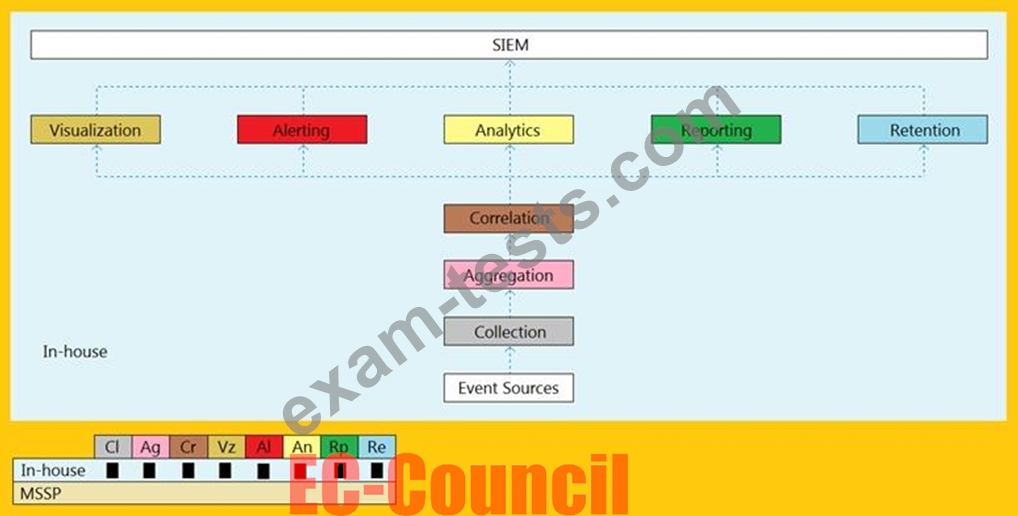
What kind of SIEM deployment architecture the organization is planning to implement?

What kind of SIEM deployment architecture the organization is planning to implement?