Question 16
Rinni, SOC analyst, while monitoring IDS logs detected events shown in the figure below.
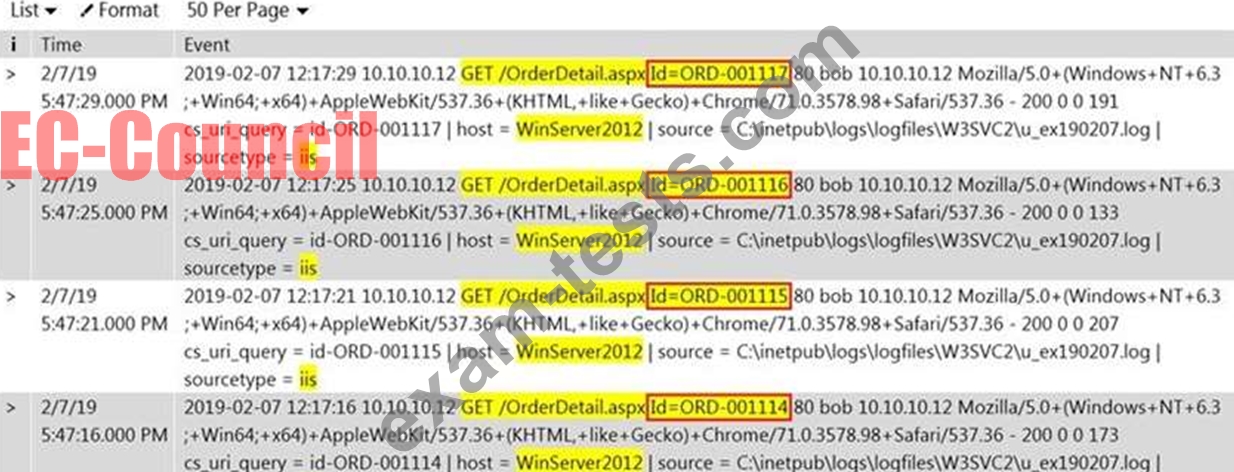
What does this event log indicate?

What does this event log indicate?
Question 17
Which of the following is a correct flow of the stages in an incident handling and response (IH&R) process?
Question 18
Robin, a SOC engineer in a multinational company, is planning to implement a SIEM. He realized that his organization is capable of performing only Correlation, Analytics, Reporting, Retention, Alerting, and Visualization required for the SIEM implementation and has to take collection and aggregation services from a Managed Security Services Provider (MSSP).
What kind of SIEM is Robin planning to implement?
What kind of SIEM is Robin planning to implement?
Question 19
Which attack works like a dictionary attack, but adds some numbers and symbols to the words from the dictionary and tries to crack the password?
Question 20
If the SIEM generates the following four alerts at the same time:
I.Firewall blocking traffic from getting into the network alerts
II.SQL injection attempt alerts
III.Data deletion attempt alerts
IV.Brute-force attempt alerts
Which alert should be given least priority as per effective alert triaging?
I.Firewall blocking traffic from getting into the network alerts
II.SQL injection attempt alerts
III.Data deletion attempt alerts
IV.Brute-force attempt alerts
Which alert should be given least priority as per effective alert triaging?



