Question 6
Which of the following network attacks takes advantage of weaknesses in the fragment reassembly functionality of the TCP/IP protocol stack?
Question 7
While reviewing the result of scanning run against a target network you come across the following:
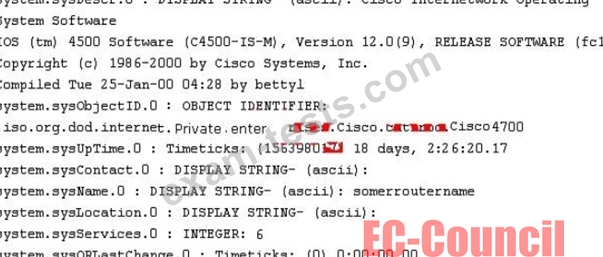
Which among the following can be used to get this output?

Which among the following can be used to get this output?
Question 8
Look at the following output. What did the hacker accomplish?


Question 9
Which of the following viruses tries to hide from anti-virus programs by actively altering and corrupting the chosen service call interruptions when they are being run?
Question 10
Security Policy is a definition of what it means to be secure for a system, organization or other entity. For
Information Technologies, there are sub-policies like Computer Security Policy, Information Protection
Policy, Information Security Policy, network Security Policy, Physical Security Policy, Remote Access
Policy, and User Account Policy.
What is the main theme of the sub-policies for Information Technologies?
Information Technologies, there are sub-policies like Computer Security Policy, Information Protection
Policy, Information Security Policy, network Security Policy, Physical Security Policy, Remote Access
Policy, and User Account Policy.
What is the main theme of the sub-policies for Information Technologies?

