Question 11
Refer to the exhibit.
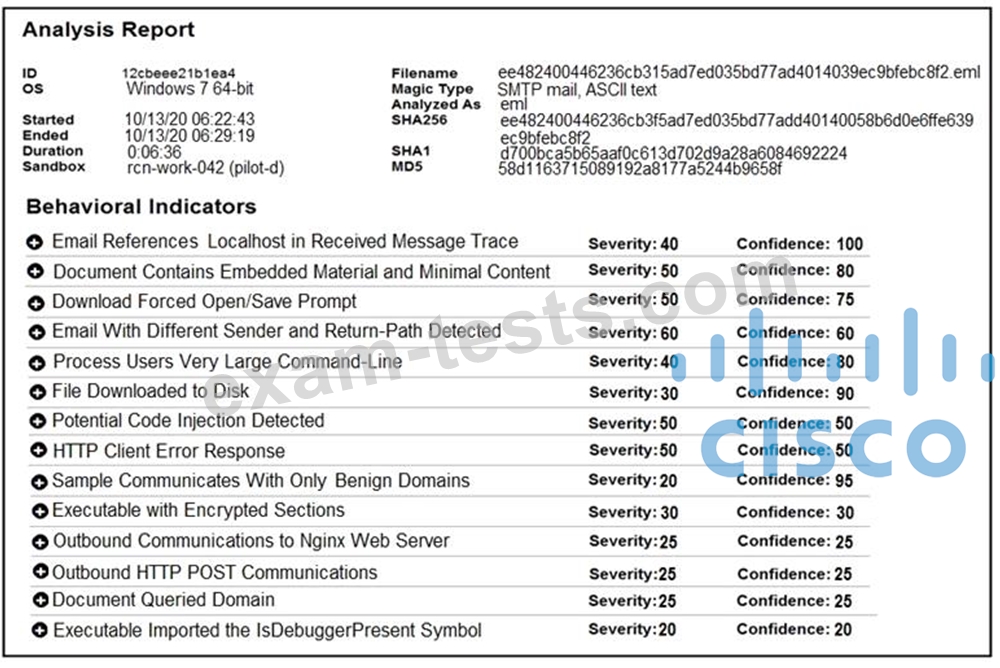
Cisco Advanced Malware Protection installed on an end-user desktop automatically submitted a low prevalence file to the Threat Grid analysis engine. What should be concluded from this report?

Cisco Advanced Malware Protection installed on an end-user desktop automatically submitted a low prevalence file to the Threat Grid analysis engine. What should be concluded from this report?
Question 12
An engineer receives an incident ticket with hundreds of intrusion alerts that require investigation. An analysis of the incident log shows that the alerts are from trusted IP addresses and internal devices. The final incident report stated that these alerts were false positives and that no intrusions were detected. What action should be taken to harden the network?
Question 13
Refer to the exhibit.
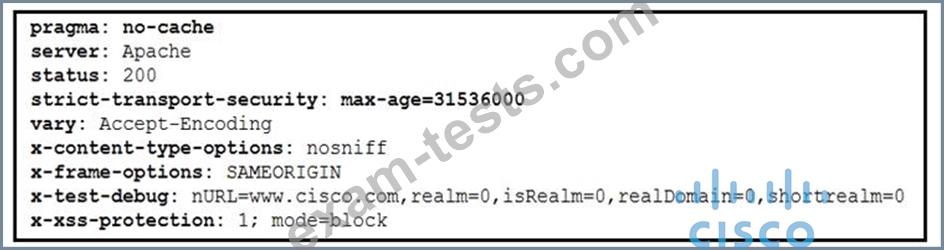
Where are the browser page rendering permissions displayed?

Where are the browser page rendering permissions displayed?
Question 14
An employee abused PowerShell commands and script interpreters, which lead to an indicator of compromise (IOC) trigger. The IOC event shows that a known malicious file has been executed, and there is an increased likelihood of a breach. Which indicator generated this IOC event?
Question 15
Refer to the exhibit.
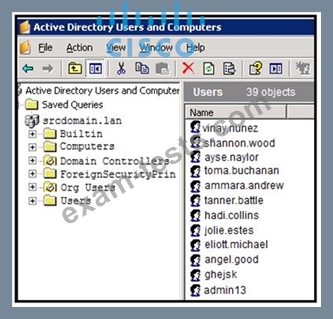
An engineer is investigating a case with suspicious usernames within the active directory. After the engineer investigates and cross-correlates events from other sources, it appears that the 2 users are privileged, and their creation date matches suspicious network traffic that was initiated from the internal network 2 days prior. Which type of compromise is occurring?

An engineer is investigating a case with suspicious usernames within the active directory. After the engineer investigates and cross-correlates events from other sources, it appears that the 2 users are privileged, and their creation date matches suspicious network traffic that was initiated from the internal network 2 days prior. Which type of compromise is occurring?
Premium Bundle
Newest 350-201 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing 350-201 Exam! BraindumpsPass.com now offer the updated 350-201 exam dumps, the BraindumpsPass.com 350-201 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com 350-201 pdf dumps with Exam Engine here:

