Question 16
Refer to the exhibit.
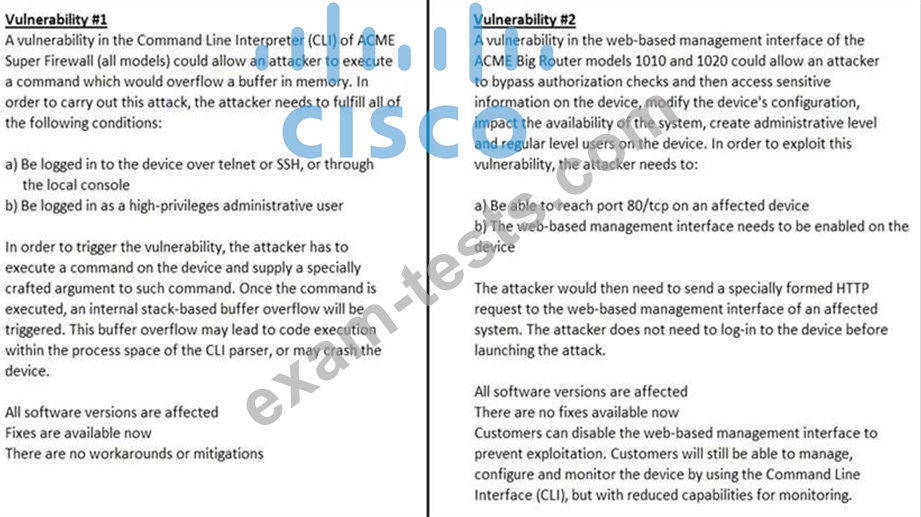
How must these advisories be prioritized for handling?

How must these advisories be prioritized for handling?
Question 17
A European-based advertisement company collects tracking information from partner websites and stores it on a local server to provide tailored ads. Which standard must the company follow to safeguard the resting data?
Question 18
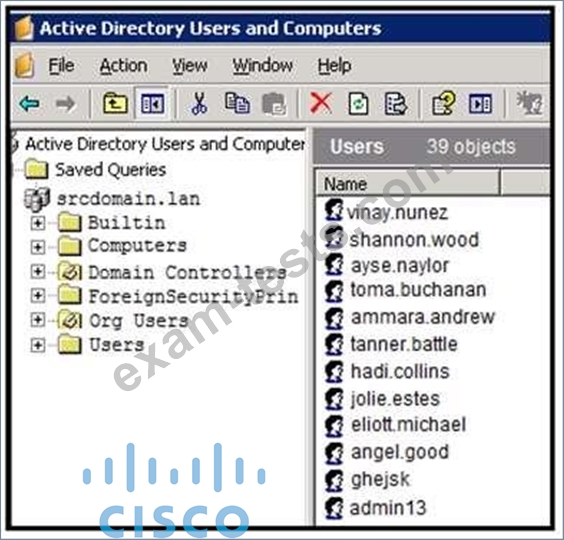
Refer to the exhibit. An engineer is investigating a case with suspicious usernames within the active directory.
After the engineer investigates and cross-correlates events from other sources, it appears that the 2 users are privileged, and their creation date matches suspicious network traffic that was initiated from the internal network 2 days prior. Which type of compromise is occurring?
Question 19
An engineer notices that every Sunday night, there is a two-hour period with a large load of network activity. Upon further investigation, the engineer finds that the activity is from locations around the globe outside the organization's service are a. What are the next steps the engineer must take?
Question 20
An API developer is improving an application code to prevent DDoS attacks. The solution needs to accommodate instances of a large number of API requests coming for legitimate purposes from trustworthy services. Which solution should be implemented?
Premium Bundle
Newest 350-201 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing 350-201 Exam! BraindumpsPass.com now offer the updated 350-201 exam dumps, the BraindumpsPass.com 350-201 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com 350-201 pdf dumps with Exam Engine here:

