Question 21
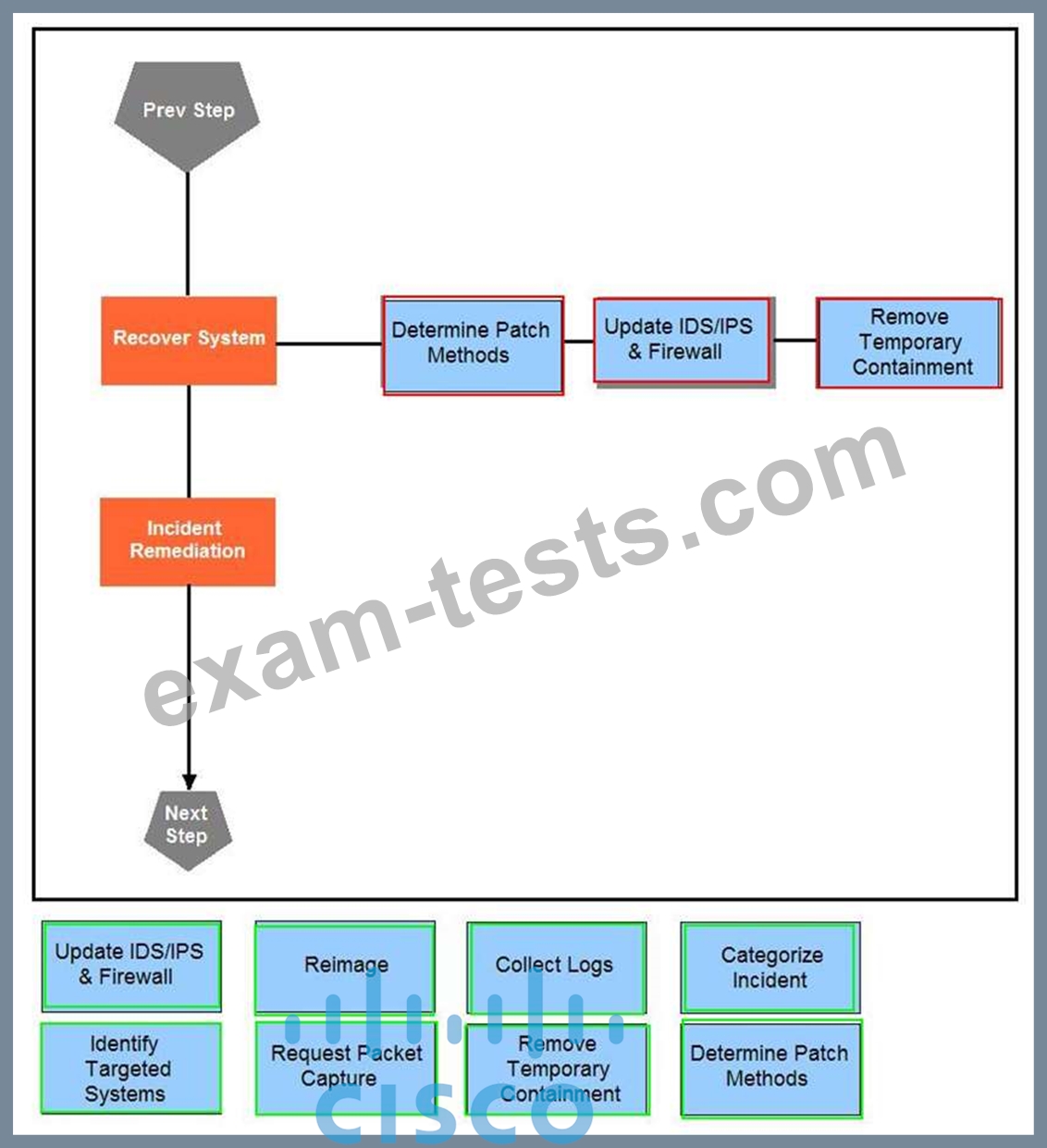
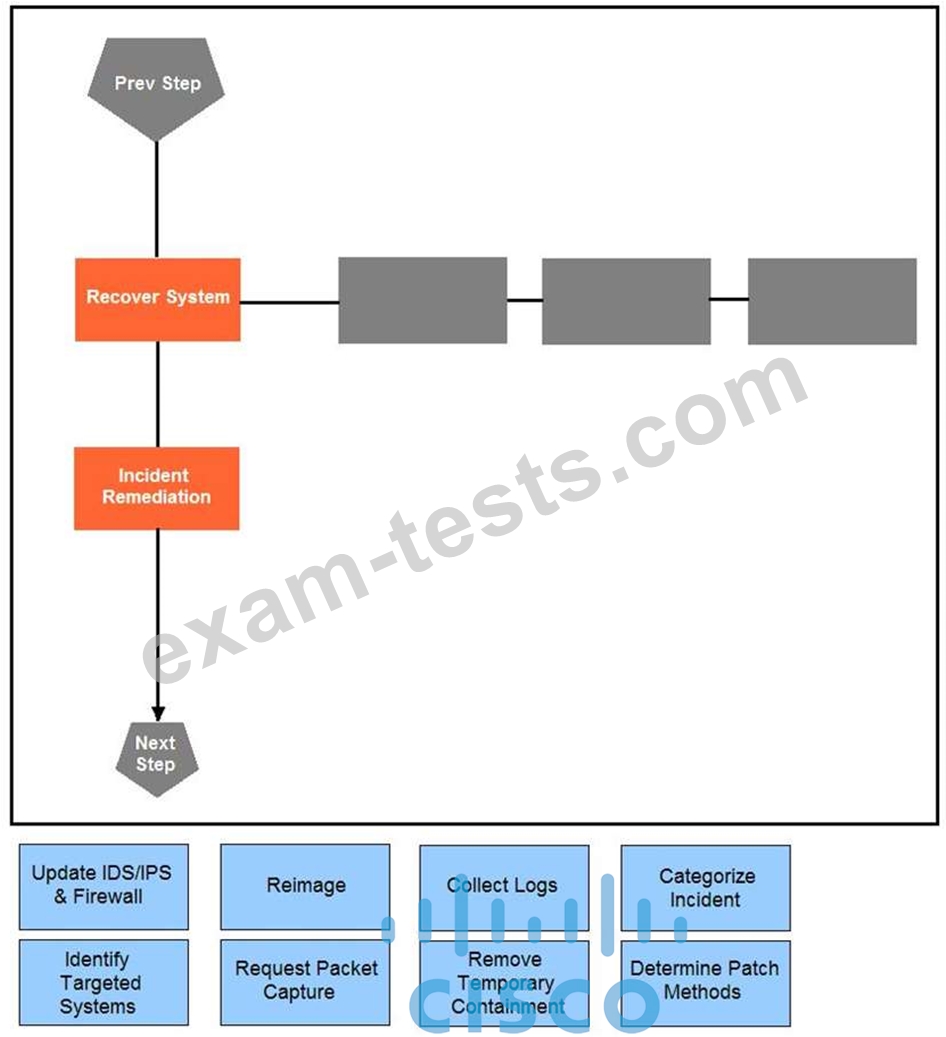
Drag and drop the actions below the image onto the boxes in the image for the actions that should be taken during this playbook step. Not all options are used.

Question 22
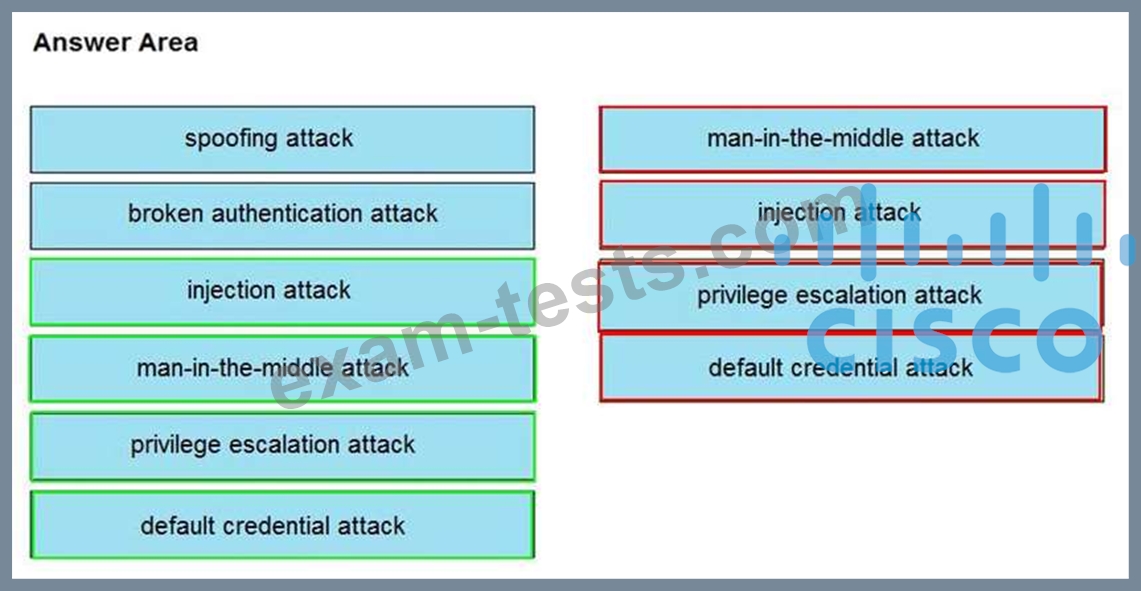
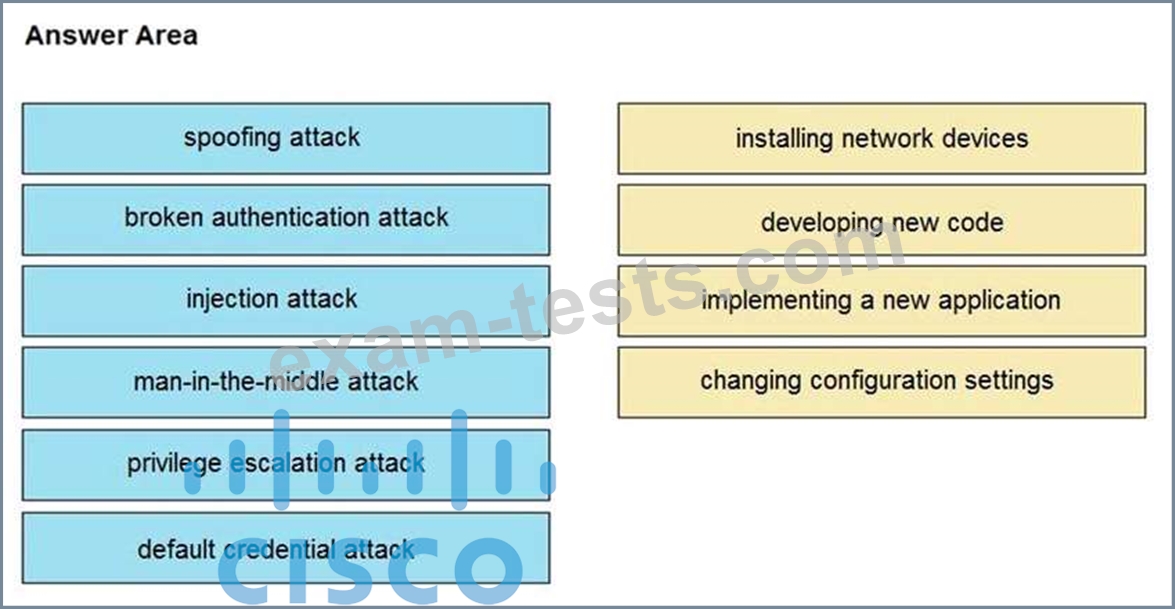
Drag and drop the threat from the left onto the scenario that introduces the threat on the right. Not all options are used.

Question 23
Refer to the exhibit.
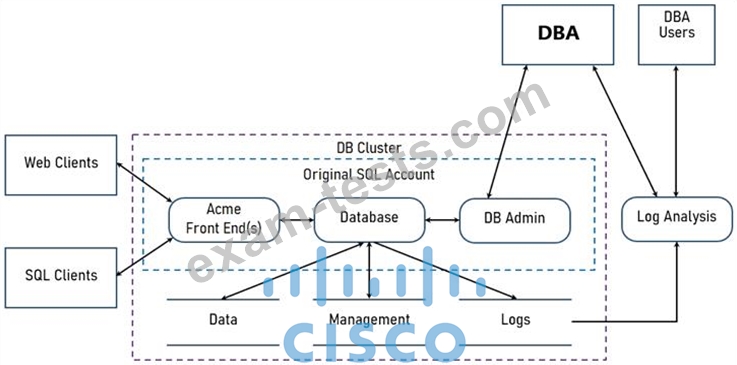
Two types of clients are accessing the front ends and the core database that manages transactions, access control, and atomicity. What is the threat model for the SQL database?

Two types of clients are accessing the front ends and the core database that manages transactions, access control, and atomicity. What is the threat model for the SQL database?
Question 24
An organization installed a new application server for IP phones. An automated process fetched user credentials from the Active Directory server, and the application will have access to on-premises and cloud services. Which security threat should be mitigated first?
Question 25
What is the purpose of hardening systems?