Question 41
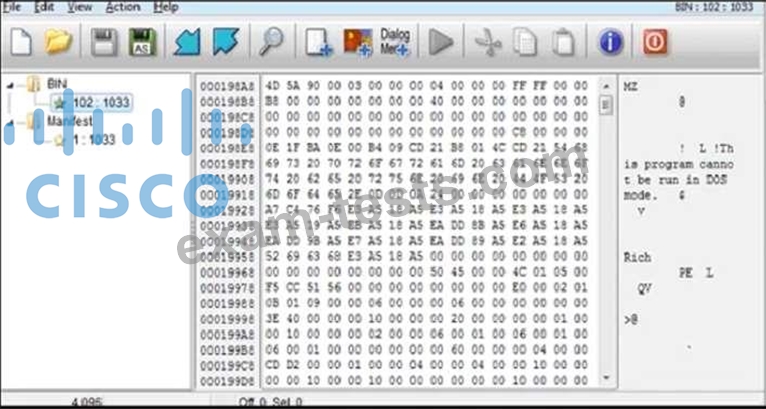
Refer to the exhibit. An engineer is reverse engineering a suspicious file by examining its resources. What does this file indicate?
Question 42
A threat actor used a phishing email to deliver a file with an embedded macro. The file was opened, and a remote code execution attack occurred in a company's infrastructure. Which steps should an engineer take at the recovery stage?
Question 43
A malware outbreak is detected by the SIEM and is confirmed as a true positive. The incident response team follows the playbook to mitigate the threat. What is the first action for the incident response team?
Question 44
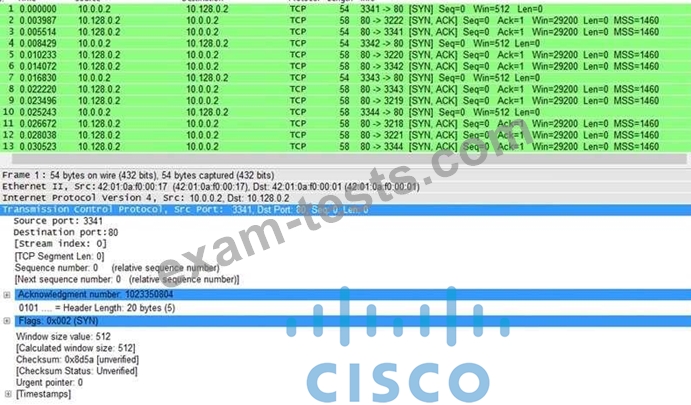
Refer to the exhibit. What is the threat in this Wireshark traffic capture?
Question 45
Refer to the exhibit.
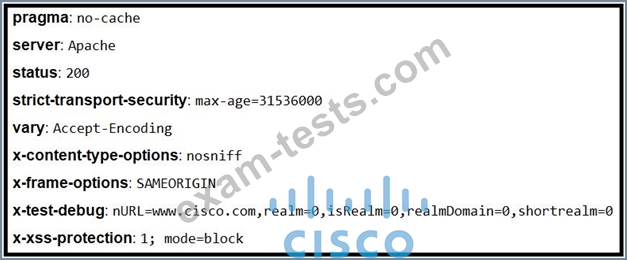
Where is the MIME type that should be followed indicated?

Where is the MIME type that should be followed indicated?

