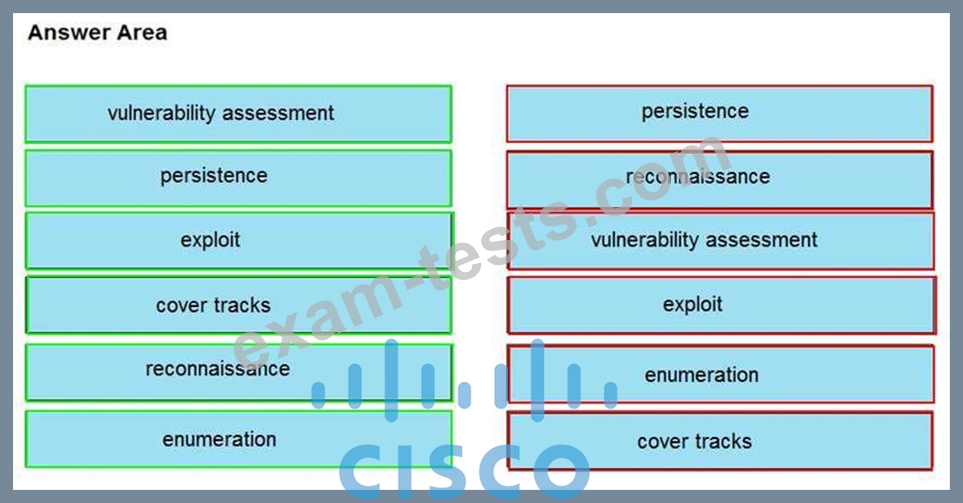
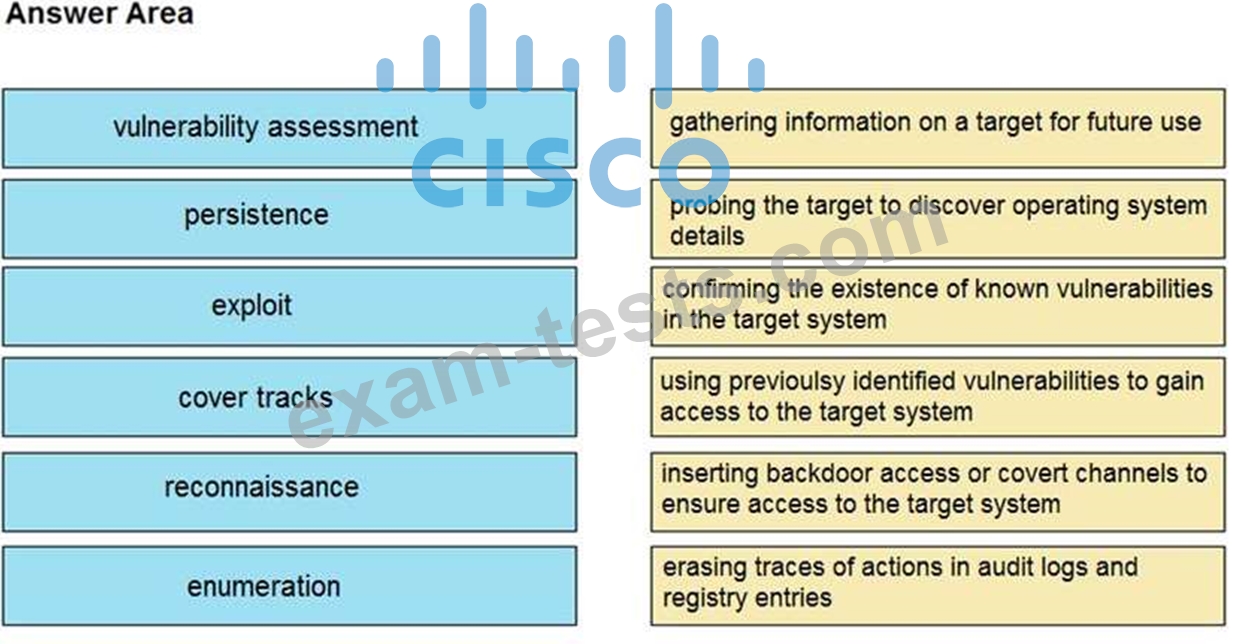
Question 36
Drag and drop the phases to evaluate the security posture of an asset from the left onto the activity that happens during the phases on the right.

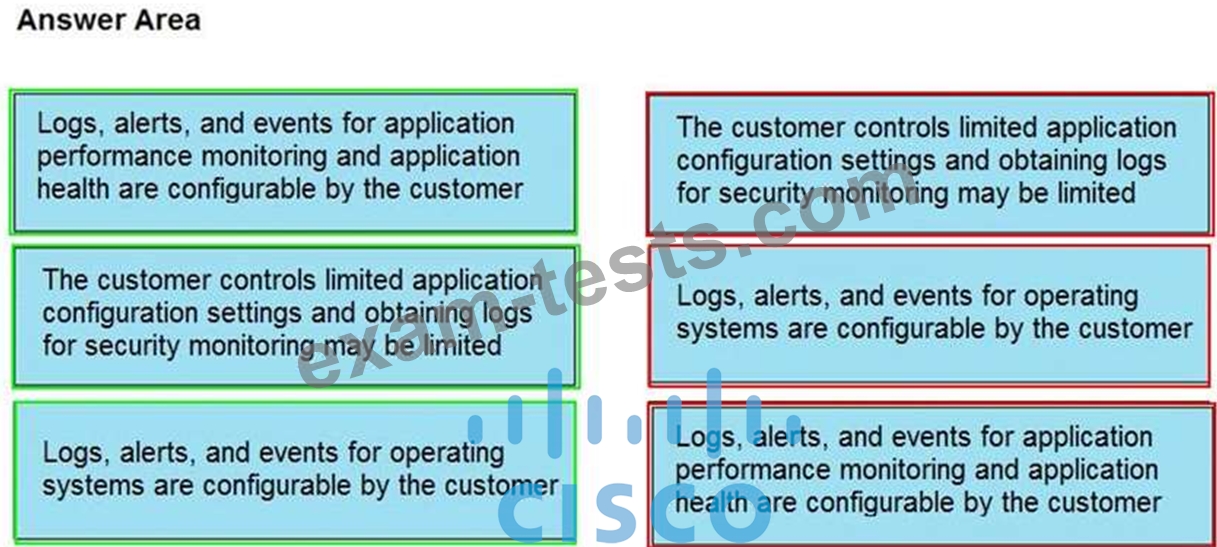
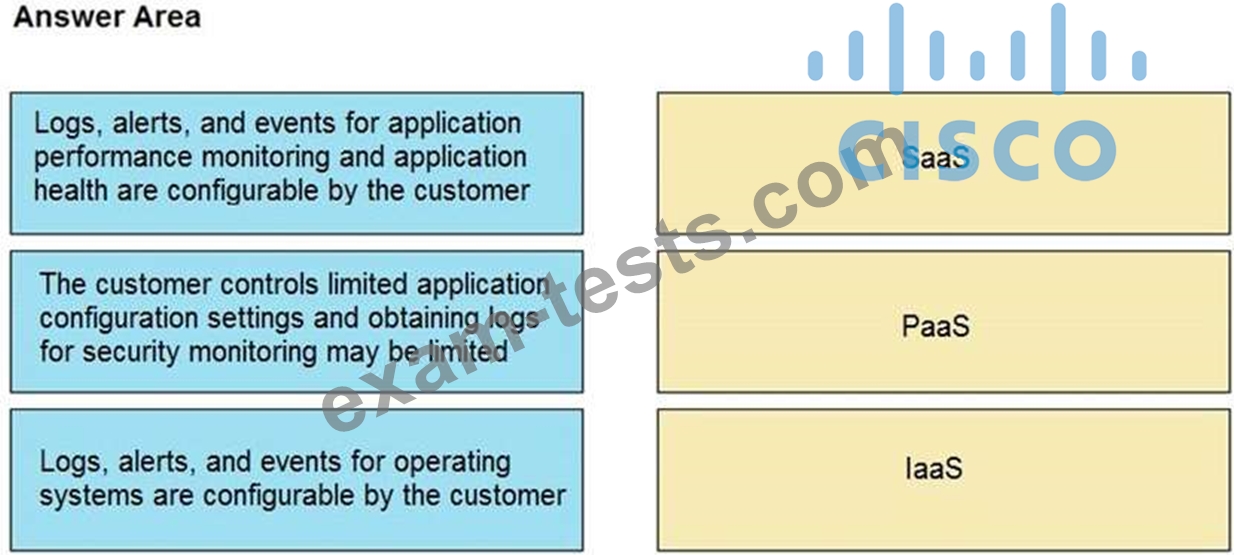
Question 37
Drag and drop the telemetry-related considerations from the left onto their cloud service models on the right.

Question 38
An organization suffered a security breach in which the attacker exploited a Netlogon Remote Protocol vulnerability for further privilege escalation. Which two actions should the incident response team take to prevent this type of attack from reoccurring? (Choose two.)
Question 39
A SOC analyst detected a ransomware outbreak in the organization coming from a malicious email attachment. Affected parties are notified, and the incident response team is assigned to the case. According to the NIST incident response handbook, what is the next step in handling the incident?
Question 40
Where do threat intelligence tools search for data to identify potential malicious IP addresses, domain names, and URLs?
Premium Bundle
Newest 350-201 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing 350-201 Exam! BraindumpsPass.com now offer the updated 350-201 exam dumps, the BraindumpsPass.com 350-201 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com 350-201 pdf dumps with Exam Engine here: