Question 56
Refer to the exhibit.
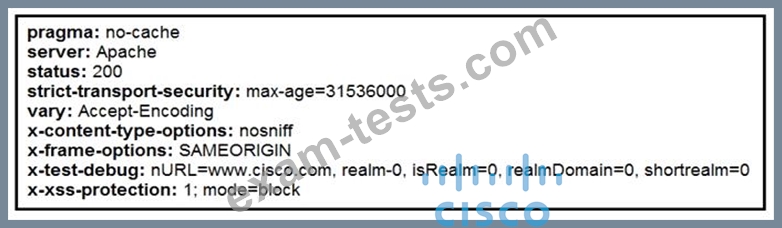
Where does it signify that a page will be stopped from loading when a scripting attack is detected?

Where does it signify that a page will be stopped from loading when a scripting attack is detected?
Question 57
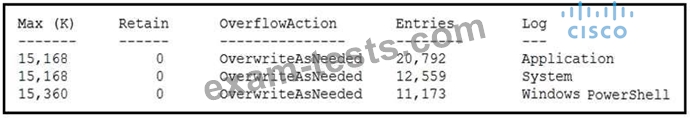
Refer to the exhibit. An employee is a victim of a social engineering phone call and installs remote access software to allow an "MS Support" technician to check his machine for malware. The employee becomes suspicious after the remote technician requests payment in the form of gift cards. The employee has copies of multiple, unencrypted database files, over 400 MB each, on his system and is worried that the scammer copied the files off but has no proof of it. The remote technician was connected sometime between 2:00 pm and 3:00 pm over https. What should be determined regarding data loss between the employee's laptop and the remote technician's system?
Question 58
Refer to the exhibit.
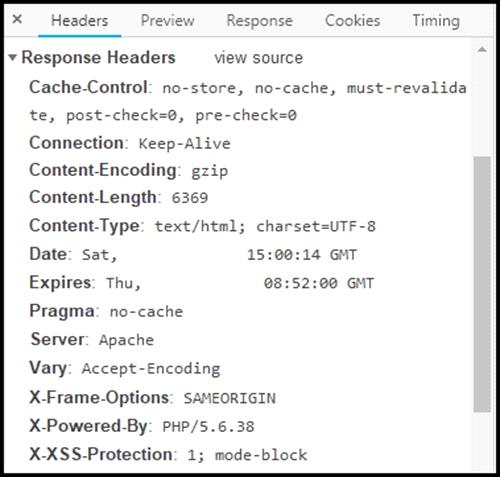
Where are the browser page rendering permissions displayed?

Where are the browser page rendering permissions displayed?
Question 59
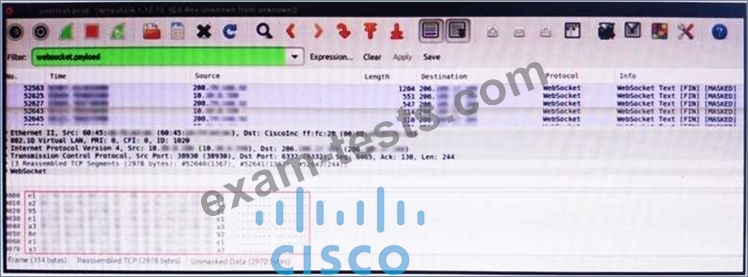
Refer to the exhibit. An engineer is analyzing this Vlan0392-int12-239.pcap file in Wireshark after detecting a suspicious network activity. The origin header for the direct IP connections in the packets was initiated by a google chrome extension on a WebSocket protocol. The engineer checked message payloads to determine what information was being sent off-site but the payloads are obfuscated and unreadable. What does this STIX indicate?
Question 60
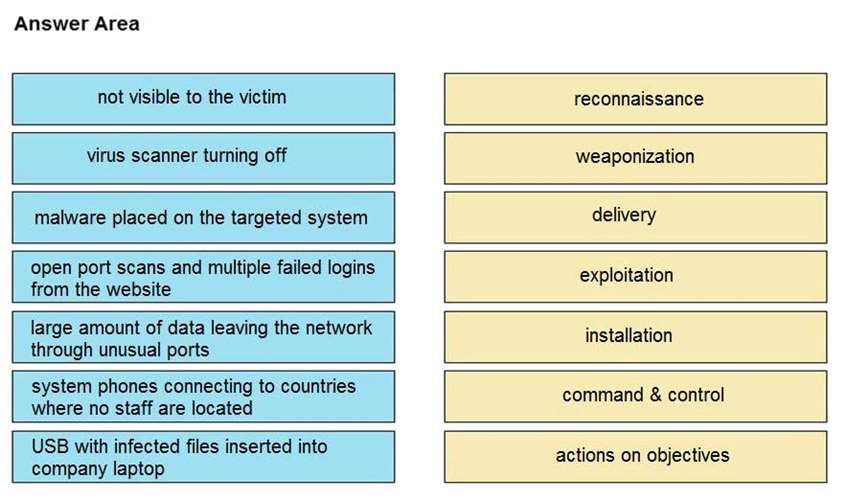
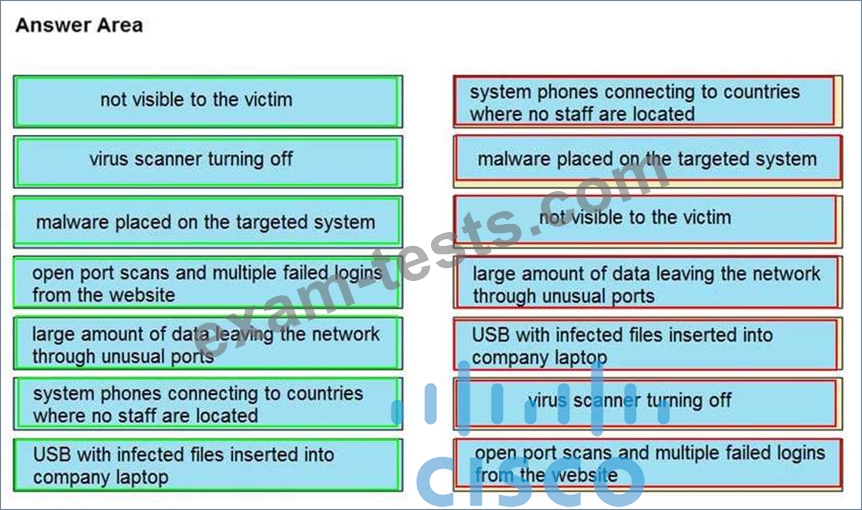
Drag and drop the type of attacks from the left onto the cyber kill chain stages at which the attacks are seen on the right.