- Home
- Cisco Certification
- 350-701 Exam
- Cisco.350-701.v2022-10-19.q571 Practice Test
Question 526
What are the two most commonly used authentication factors in multifactor authentication? (Choose two)
Correct Answer: A,D
Explanation Explanation Multi-factor Authentication (MFA) is an authentication method that requires the user to provide two or more verification factors to gain access to a resource. MFA requires means of verification that unauthorized users won't have. Proper multi-factor authentication uses factors from at least two different categories. MFA methods: + Knowledge - usually a password - is the most commonly used tool in MFA solutions. However, despite their simplicity, passwords have become a security problem and slow down productivity. + Physical factors - also called possession factors-use tokens, such as a USB dongle or a portable device, that generate a temporary QR (quick response) code. Mobile phones are commonly used, as they have the advantage of being readily available in most situations. + Inherent - This category includes biometrics like fingerprint, face, and retina scans. As technology advances, it may also include voice ID or other behavioral inputs like keystroke metrics. Because inherent factors are reliably unique, always present, and secure, this category shows promise. + Location-based and time-based - Authentication systems can use GPS coordinates, network parameters, and metadata for the network in use, and device recognition for MFA. Adaptive authentication combines these data points with historical or contextual user data. A time factor in conjunction with a location factor could detect an attacker attempting to authenticate in Europe when the user was last authenticated in California an hour prior, for example. + Time-based one-time password (TOTP) - This is generally used in 2FA but could apply to any MFA method where a second step is introduced dynamically at login upon completing a first step. The wait for a second step-in which temporary passcodes are sent by SMS or email-is usually brief, and the process is easy to use for a wide range of users and devices. This method is currently widely used. + Social media - In this case a user grants permission for a website to use their social media username and password for login. This provide an easy login process, and one generally available to all users. + Risk-based authentication - Sometimes called adaptive multi-factor authentication, this method combines adaptive authentication and algorithms that calculate risk and observe the context of specific login requests. The goal of this method is to reduce redundant logins and provide a more user-friendly workflow. + Push-based 2FA - Push-based 2FA improves on SMS and TOTP 2FA by adding additional layers of security while improving ease of use. It confirms a user's identity with multiple factors of authentication that other methods cannot. Because push-based 2FA sends notifications through data networks like cellular or Wi-Fi, users must have data access on their mobile devices to use the 2FA functionality. Reference: https://www.cisco.com/c/en/us/products/security/what-is-multi-factor-authentication.html The two most popular authentication factors are knowledge and inherent (including biometrics like fingerprint, face, and retina scans. Biometrics is used commonly in mobile devices).
Explanation
Multi-factor Authentication (MFA) is an authentication method that requires the user to provide two or more verification factors to gain access to a resource. MFA requires means of verification that unauthorized users won't have.
Proper multi-factor authentication uses factors from at least two different categories.
MFA methods:
+ Knowledge - usually a password - is the most commonly used tool in MFA solutions. However, despite their simplicity, passwords have become a security problem and slow down productivity.
+ Physical factors - also called possession factors-use tokens, such as a USB dongle or a portable device, that generate a temporary QR (quick response) code. Mobile phones are commonly used, as they have the advantage of being readily available in most situations.
+ Inherent - This category includes biometrics like fingerprint, face, and retina scans. As technology advances, it may also include voice ID or other behavioral inputs like keystroke metrics. Because inherent factors are reliably unique, always present, and secure, this category shows promise.
+ Location-based and time-based - Authentication systems can use GPS coordinates, network parameters, and metadata for the network in use, and device recognition for MFA. Adaptive authentication combines these data points with historical or contextual user data.
A time factor in conjunction with a location factor could detect an attacker attempting to authenticate in Europe when the user was last authenticated in California an hour prior, for example.
+ Time-based one-time password (TOTP) - This is generally used in 2FA but could apply to any MFA method where a second step is introduced dynamically at login upon completing a first step. The wait for a second step-in which temporary passcodes are sent by SMS or email-is usually brief, and the process is easy to use for a wide range of users and devices. This method is currently widely used.
+ Social media - In this case a user grants permission for a website to use their social media username and password for login. This provide an easy login process, and one generally available to all users.
+ Risk-based authentication - Sometimes called adaptive multi-factor authentication, this method combines adaptive authentication and algorithms that calculate risk and observe the context of specific login requests.
The goal of this method is to reduce redundant logins and provide a more user-friendly workflow.
+ Push-based 2FA - Push-based 2FA improves on SMS and TOTP 2FA by adding additional layers of security while improving ease of use. It confirms a user's identity with multiple factors of authentication that other methods cannot. Because push-based 2FA sends notifications through data networks like cellular or Wi-Fi, users must have data access on their mobile devices to use the 2FA functionality.
Reference:
The two most popular authentication factors are knowledge and inherent (including biometrics like fingerprint, Explanation Explanation Multi-factor Authentication (MFA) is an authentication method that requires the user to provide two or more verification factors to gain access to a resource. MFA requires means of verification that unauthorized users won't have. Proper multi-factor authentication uses factors from at least two different categories. MFA methods: + Knowledge - usually a password - is the most commonly used tool in MFA solutions. However, despite their simplicity, passwords have become a security problem and slow down productivity. + Physical factors - also called possession factors-use tokens, such as a USB dongle or a portable device, that generate a temporary QR (quick response) code. Mobile phones are commonly used, as they have the advantage of being readily available in most situations. + Inherent - This category includes biometrics like fingerprint, face, and retina scans. As technology advances, it may also include voice ID or other behavioral inputs like keystroke metrics. Because inherent factors are reliably unique, always present, and secure, this category shows promise. + Location-based and time-based - Authentication systems can use GPS coordinates, network parameters, and metadata for the network in use, and device recognition for MFA. Adaptive authentication combines these data points with historical or contextual user data. A time factor in conjunction with a location factor could detect an attacker attempting to authenticate in Europe when the user was last authenticated in California an hour prior, for example. + Time-based one-time password (TOTP) - This is generally used in 2FA but could apply to any MFA method where a second step is introduced dynamically at login upon completing a first step. The wait for a second step-in which temporary passcodes are sent by SMS or email-is usually brief, and the process is easy to use for a wide range of users and devices. This method is currently widely used. + Social media - In this case a user grants permission for a website to use their social media username and password for login. This provide an easy login process, and one generally available to all users. + Risk-based authentication - Sometimes called adaptive multi-factor authentication, this method combines adaptive authentication and algorithms that calculate risk and observe the context of specific login requests. The goal of this method is to reduce redundant logins and provide a more user-friendly workflow. + Push-based 2FA - Push-based 2FA improves on SMS and TOTP 2FA by adding additional layers of security while improving ease of use. It confirms a user's identity with multiple factors of authentication that other methods cannot. Because push-based 2FA sends notifications through data networks like cellular or Wi-Fi, users must have data access on their mobile devices to use the 2FA functionality. Reference: https://www.cisco.com/c/en/us/products/security/what-is-multi-factor-authentication.html The two most popular authentication factors are knowledge and inherent (including biometrics like fingerprint, face, and retina scans. Biometrics is used commonly in mobile devices).
Explanation
Multi-factor Authentication (MFA) is an authentication method that requires the user to provide two or more verification factors to gain access to a resource. MFA requires means of verification that unauthorized users won't have.
Proper multi-factor authentication uses factors from at least two different categories.
MFA methods:
+ Knowledge - usually a password - is the most commonly used tool in MFA solutions. However, despite their simplicity, passwords have become a security problem and slow down productivity.
+ Physical factors - also called possession factors-use tokens, such as a USB dongle or a portable device, that generate a temporary QR (quick response) code. Mobile phones are commonly used, as they have the advantage of being readily available in most situations.
+ Inherent - This category includes biometrics like fingerprint, face, and retina scans. As technology advances, it may also include voice ID or other behavioral inputs like keystroke metrics. Because inherent factors are reliably unique, always present, and secure, this category shows promise.
+ Location-based and time-based - Authentication systems can use GPS coordinates, network parameters, and metadata for the network in use, and device recognition for MFA. Adaptive authentication combines these data points with historical or contextual user data.
A time factor in conjunction with a location factor could detect an attacker attempting to authenticate in Europe when the user was last authenticated in California an hour prior, for example.
+ Time-based one-time password (TOTP) - This is generally used in 2FA but could apply to any MFA method where a second step is introduced dynamically at login upon completing a first step. The wait for a second step-in which temporary passcodes are sent by SMS or email-is usually brief, and the process is easy to use for a wide range of users and devices. This method is currently widely used.
+ Social media - In this case a user grants permission for a website to use their social media username and password for login. This provide an easy login process, and one generally available to all users.
+ Risk-based authentication - Sometimes called adaptive multi-factor authentication, this method combines adaptive authentication and algorithms that calculate risk and observe the context of specific login requests.
The goal of this method is to reduce redundant logins and provide a more user-friendly workflow.
+ Push-based 2FA - Push-based 2FA improves on SMS and TOTP 2FA by adding additional layers of security while improving ease of use. It confirms a user's identity with multiple factors of authentication that other methods cannot. Because push-based 2FA sends notifications through data networks like cellular or Wi-Fi, users must have data access on their mobile devices to use the 2FA functionality.
Reference:
The two most popular authentication factors are knowledge and inherent (including biometrics like fingerprint, Explanation Explanation Multi-factor Authentication (MFA) is an authentication method that requires the user to provide two or more verification factors to gain access to a resource. MFA requires means of verification that unauthorized users won't have. Proper multi-factor authentication uses factors from at least two different categories. MFA methods: + Knowledge - usually a password - is the most commonly used tool in MFA solutions. However, despite their simplicity, passwords have become a security problem and slow down productivity. + Physical factors - also called possession factors-use tokens, such as a USB dongle or a portable device, that generate a temporary QR (quick response) code. Mobile phones are commonly used, as they have the advantage of being readily available in most situations. + Inherent - This category includes biometrics like fingerprint, face, and retina scans. As technology advances, it may also include voice ID or other behavioral inputs like keystroke metrics. Because inherent factors are reliably unique, always present, and secure, this category shows promise. + Location-based and time-based - Authentication systems can use GPS coordinates, network parameters, and metadata for the network in use, and device recognition for MFA. Adaptive authentication combines these data points with historical or contextual user data. A time factor in conjunction with a location factor could detect an attacker attempting to authenticate in Europe when the user was last authenticated in California an hour prior, for example. + Time-based one-time password (TOTP) - This is generally used in 2FA but could apply to any MFA method where a second step is introduced dynamically at login upon completing a first step. The wait for a second step-in which temporary passcodes are sent by SMS or email-is usually brief, and the process is easy to use for a wide range of users and devices. This method is currently widely used. + Social media - In this case a user grants permission for a website to use their social media username and password for login. This provide an easy login process, and one generally available to all users. + Risk-based authentication - Sometimes called adaptive multi-factor authentication, this method combines adaptive authentication and algorithms that calculate risk and observe the context of specific login requests. The goal of this method is to reduce redundant logins and provide a more user-friendly workflow. + Push-based 2FA - Push-based 2FA improves on SMS and TOTP 2FA by adding additional layers of security while improving ease of use. It confirms a user's identity with multiple factors of authentication that other methods cannot. Because push-based 2FA sends notifications through data networks like cellular or Wi-Fi, users must have data access on their mobile devices to use the 2FA functionality. Reference: https://www.cisco.com/c/en/us/products/security/what-is-multi-factor-authentication.html The two most popular authentication factors are knowledge and inherent (including biometrics like fingerprint, face, and retina scans. Biometrics is used commonly in mobile devices).
Question 527
Which two aspects of the cloud PaaS model are managed by the customer but not the provider? (Choose two.)
Correct Answer: D,E
Explanation
https://apprenda.com/library/paas/iaas-paas-saas-explained-compared/
https://apprenda.com/library/paas/iaas-paas-saas-explained-compared/
Question 528
An administrator is configuring a DHCP server to better secure their environment. They need to be able to ratelimit the traffic and ensure that legitimate requests are not dropped. How would this be accomplished?
Correct Answer: A
To understand DHCP snooping we need to learn about DHCP spoofing attack first.
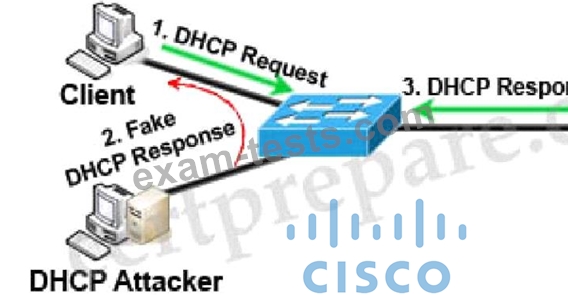
DHCP spoofing is a type of attack in that the attacker listens for DHCP Requests from clients and answers them with fake DHCP Response before the authorized DHCP Response comes to the clients. The fake DHCP Response often gives its IP address as the client default gateway -> all the traffic sent from the client will go through the attacker computer, the attacker becomes a "man-in-the-middle".
The attacker can have some ways to make sure its fake DHCP Response arrives first. In fact, if the attacker is "closer" than the DHCP Server then he doesn't need to do anything. Or he can DoS the DHCP Server so that it can't send the DHCP Response.
DHCP snooping can prevent DHCP spoofing attacks. DHCP snooping is a Cisco Catalyst feature that determines which switch ports can respond to DHCP requests. Ports are identified as trusted and untrusted.
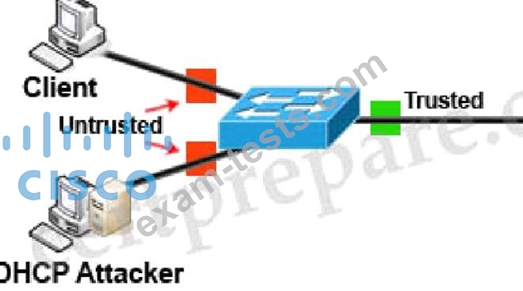
Only ports that connect to an authorized DHCP server are trusted, and allowed to send all types of DHCP messages. All other ports on the switch are untrusted and can send only DHCP requests. If a DHCP response is seen on an untrusted port, the port is shut down.

DHCP spoofing is a type of attack in that the attacker listens for DHCP Requests from clients and answers them with fake DHCP Response before the authorized DHCP Response comes to the clients. The fake DHCP Response often gives its IP address as the client default gateway -> all the traffic sent from the client will go through the attacker computer, the attacker becomes a "man-in-the-middle".
The attacker can have some ways to make sure its fake DHCP Response arrives first. In fact, if the attacker is "closer" than the DHCP Server then he doesn't need to do anything. Or he can DoS the DHCP Server so that it can't send the DHCP Response.
DHCP snooping can prevent DHCP spoofing attacks. DHCP snooping is a Cisco Catalyst feature that determines which switch ports can respond to DHCP requests. Ports are identified as trusted and untrusted.

Only ports that connect to an authorized DHCP server are trusted, and allowed to send all types of DHCP messages. All other ports on the switch are untrusted and can send only DHCP requests. If a DHCP response is seen on an untrusted port, the port is shut down.
Question 529
What does Cisco AMP for Endpoints use to help an organization detect different families of malware?
Correct Answer: A
Explanation Explanation ETHOS is the Cisco file grouping engine. It allows us to group families of files together so if we see variants of a malware, we mark the ETHOS hash as malicious and whole families of malware are instantly detected. Reference: https://docs.amp.cisco.com/AMP%20for%20Endpoints%20User%20Guide.pdf ETHOS = Fuzzy Fingerprinting using static/passive heuristics Explanation ETHOS is the Cisco file grouping engine. It allows us to group families of files together so if we see variants of a malware, we mark the ETHOS hash as malicious and whole families of malware are instantly detected.
Reference:
Explanation Explanation ETHOS is the Cisco file grouping engine. It allows us to group families of files together so if we see variants of a malware, we mark the ETHOS hash as malicious and whole families of malware are instantly detected. Reference: https://docs.amp.cisco.com/AMP%20for%20Endpoints%20User%20Guide.pdf ETHOS = Fuzzy Fingerprinting using static/passive heuristics
Reference:
Explanation Explanation ETHOS is the Cisco file grouping engine. It allows us to group families of files together so if we see variants of a malware, we mark the ETHOS hash as malicious and whole families of malware are instantly detected. Reference: https://docs.amp.cisco.com/AMP%20for%20Endpoints%20User%20Guide.pdf ETHOS = Fuzzy Fingerprinting using static/passive heuristics
Question 530
What can be integrated with Cisco Threat Intelligence Director to provide information about security threats, which allows the SOC to proactively automate responses to those threats?
Correct Answer: C
Cisco Threat Intelligence Director (CTID) can be integrated with existing Threat Intelligence Platforms deployed by your organization to ingest threat intelligence automatically.
Cisco Threat Intelligence Director (CTID) can be integrated with existing Threat Intelligence Platforms deployed by your organization to ingest threat intelligence automatically.
Reference:
Cisco Threat Intelligence Director (CTID) can be integrated with existing Threat Intelligence Platforms deployed by your organization to ingest threat intelligence automatically.
Cisco Threat Intelligence Director (CTID) can be integrated with existing Threat Intelligence Platforms deployed by your organization to ingest threat intelligence automatically.
Reference:
Cisco Threat Intelligence Director (CTID) can be integrated with existing Threat Intelligence Platforms deployed by your organization to ingest threat intelligence automatically.
- Other Version
- 1467Cisco.350-701.v2025-10-04.q562
- 1077Cisco.350-701.v2025-06-19.q238
- 1555Cisco.350-701.v2024-12-18.q472
- 2720Cisco.350-701.v2023-08-01.q405
- 3399Cisco.350-701.v2023-05-04.q372
- 2329Cisco.350-701.v2023-03-16.q218
- 7256Cisco.350-701.v2022-07-08.q453
- 4200Cisco.350-701.v2022-02-02.q204
- 116Cisco.Prepawaypdf.350-701.v2021-12-15.by.ellen.316q.pdf
- Latest Upload
- 126USGBC.LEED-AP-Homes.v2026-01-02.q36
- 115SAP.C-THR94-2505.v2026-01-02.q29
- 135MedicalProfessional.CHFM.v2026-01-01.q37
- 116SAP.C-BCSPM-2502.v2026-01-01.q9
- 118Microsoft.MB-335.v2026-01-01.q142
- 120SAP.C_THR70_2505.v2026-01-01.q55
- 157Salesforce.Financial-Services-Cloud.v2026-01-01.q121
- 183Fortinet.FCSS_SDW_AR-7.4.v2025-12-31.q73
- 163UiPath.UiPath-SAIAv1.v2025-12-30.q89
- 214HP.HPE0-V25.v2025-12-29.q138
[×]
Download PDF File
Enter your email address to download Cisco.350-701.v2022-10-19.q571 Practice Test

