Question 536
Which technology reduces data loss by identifying sensitive information stored in public computing environments?
Question 537
After a recent breach, an organization determined that phishing was used to gain initial access to the network before regaining persistence. The information gained from the phishing attack was a result of users visiting known malicious websites. What must be done in order to prevent this from happening in the future?
Question 538
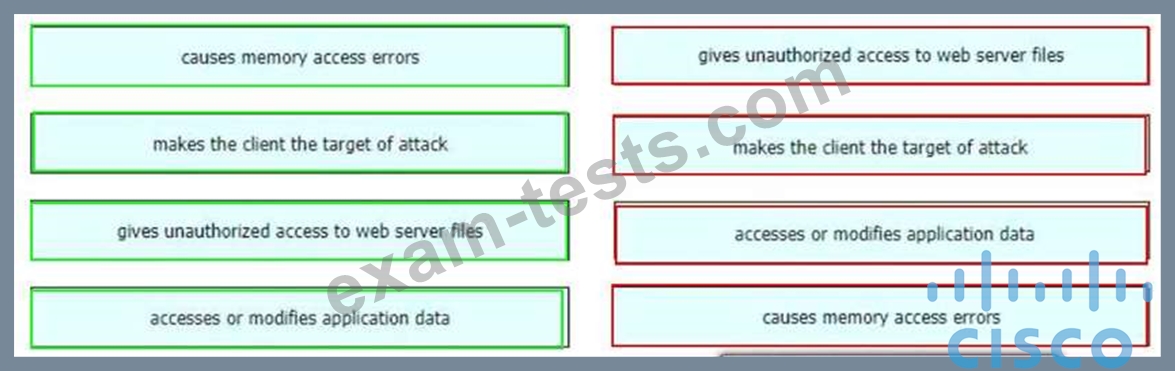
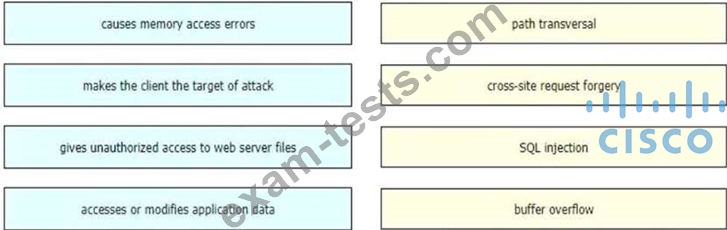
Drag and drop the exploits from the left onto the type of security vulnerability on the right.

Question 539
An engineer is adding a Cisco DUO solution to the current TACACS+ deployment using Cisco ISE. The engineer wants to authenticate users using their account when they log into network devices. Which action accomplishes this task?
Question 540
Which DevSecOps implementation process gives a weekly or daily update instead of monthly or quarterly in the applications?