Question 546
A hacker initiated a social engineering attack and stole username and passwords of some users within a company. Which product should be used as a solution to this problem?
Question 547
An administrator configures a new destination list in Cisco Umbrella so that the organization can block specific domains for its devices. What should be done to ensure that all subdomains of domain.com are blocked?
Question 548
Which Dos attack uses fragmented packets to crash a target machine?
Question 549
Which two endpoint measures are used to minimize the chances of falling victim to phishing and social engineering attacks? (Choose two.)
Question 550
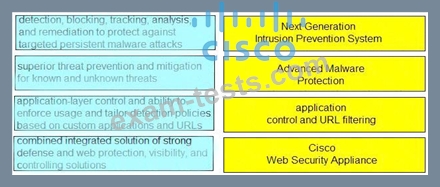
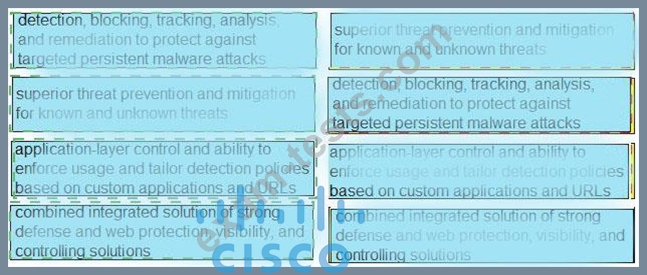
Drag and drop the capabilities from the left onto the correct technologies on the right.