Question 81
Which product allows Cisco FMC to push security intelligence observable to its sensors from other products?
Question 82
An engineer needs behavioral analysis to detect malicious activity on the hosts, and is configuring the organization's public cloud to send telemetry using the cloud provider's mechanisms to a security device. Which mechanism should the engineer configure to accomplish this goal?
Question 83
Drag and drop the Firepower Next Generation Intrustion Prevention System detectors from the left onto the correct definitions on the right.


Question 84
Refer to the exhibit.
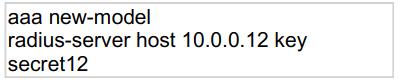
Which statement about the authentication protocol used in the configuration is true?

Which statement about the authentication protocol used in the configuration is true?
Question 85
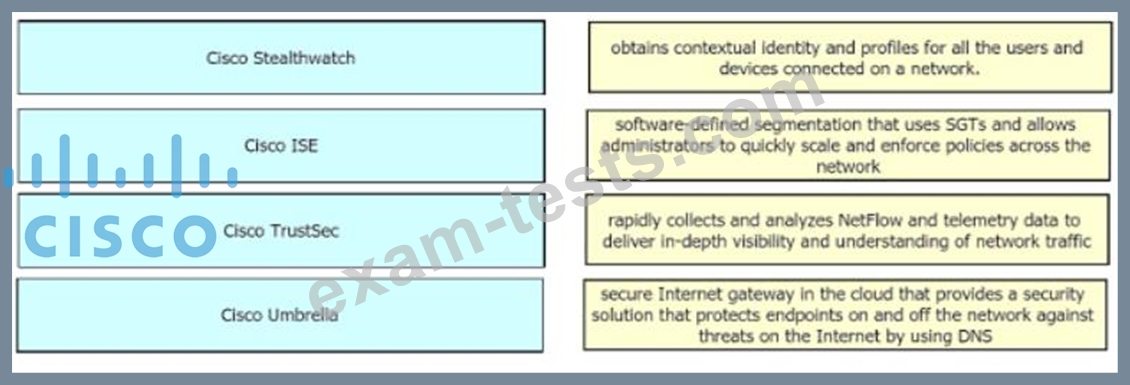
Drag and drop the solutions from the left onto the solution's benefits on the right.