Question 116
Which parameter is required when configuring a Netflow exporter on a Cisco Router?
Question 117
How does Cisco Umbrella archive logs to an enterprise owned storage?
Question 118
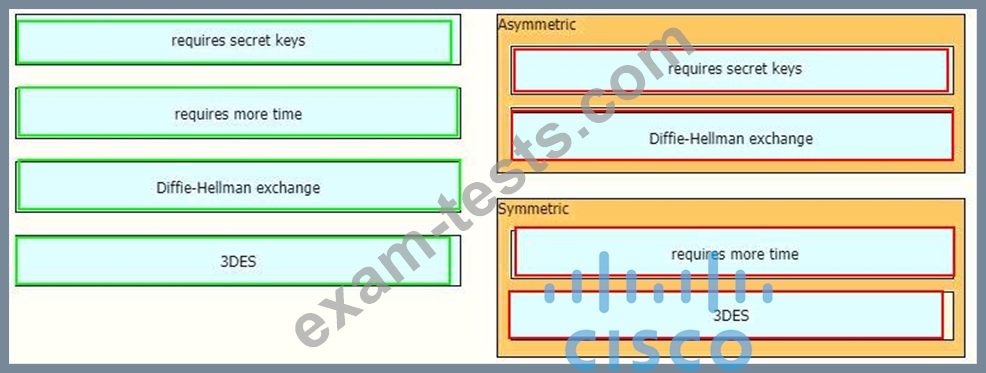
Drag and drop the descriptions from the left onto the encryption algorithms on the right.

Question 119
An attacker needs to perform reconnaissance on a target system to help gain access to it. The system has weak passwords, no encryption on the VPN links, and software bugs on the system's applications. Which vulnerability allows the attacker to see the passwords being transmitted in clear text?
Question 120
What are two workloaded security models? (Choose two)