Question 126
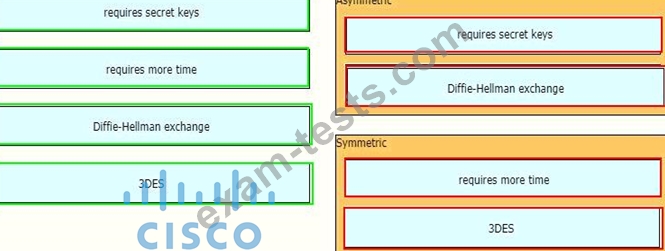
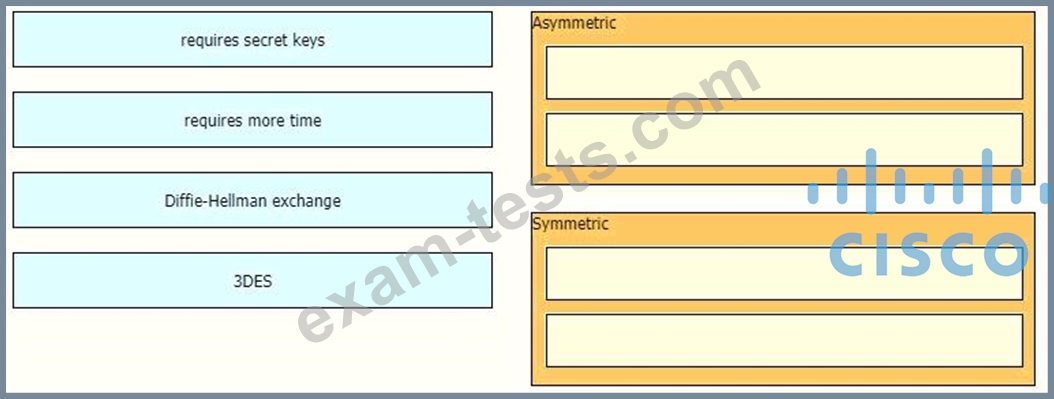
Drag and drop the descriptions from the left onto the encryption algorithms on the right.

Question 127
What is a characteristic of a bridge group in ASA Firewall transparent mode'?
Question 128
Refer to the exhibit.
import requests
client_id = '<Client id>'
api_key = '<API Key>'
url = 'https://api.amp.cisco.com/v1/computers'
response = requests.get(url, auth=(client_id, api_key))
response_json = response.json()
for computer in response_json['data']
hostname = computer['hostname']
print(hostname)
What will happen when the Python script is executed?
import requests
client_id = '<Client id>'
api_key = '<API Key>'
url = 'https://api.amp.cisco.com/v1/computers'
response = requests.get(url, auth=(client_id, api_key))
response_json = response.json()
for computer in response_json['data']
hostname = computer['hostname']
print(hostname)
What will happen when the Python script is executed?
Question 129
What is a language format designed to exchange threat intelligence that can be transported over the TAXII protocol?
Question 130
Which PKI enrollment method allows the user to separate authentication and enrollment actions and also provides an option to specify HTTP/TFTP commands to perform file retrieval from the server?