Question 121
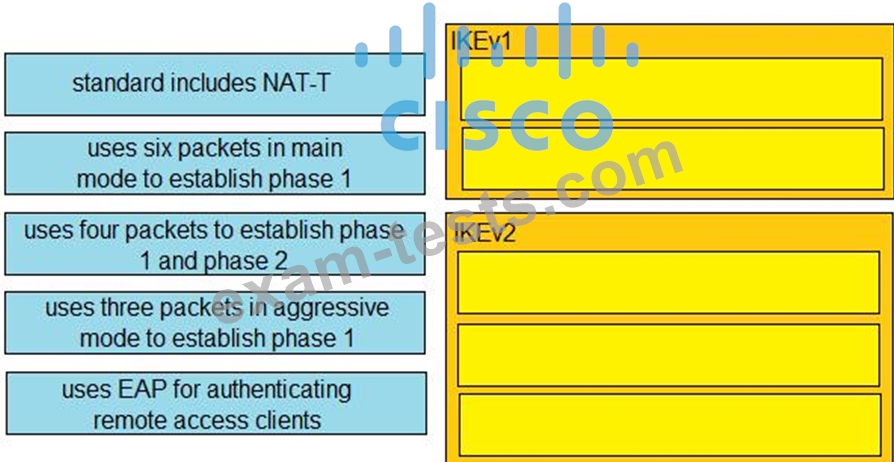
Drag and drop the descriptions from the left onto the correct protocol versions on the right.

Question 122
An engineer needs behavioral analysis to detect malicious activity on the hosts, and is configuring the organization's public cloud to send telemetry using the cloud provider's mechanisms to a security device.
Which mechanism should the engineer configure to accomplish this goal?
Which mechanism should the engineer configure to accomplish this goal?
Question 123
Refer to the exhibit.
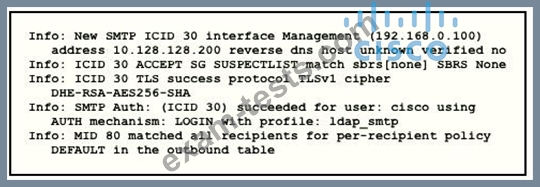
Which type of authentication is in use?

Which type of authentication is in use?
Question 124
For Cisco IOS PKI, which two types of Servers are used as a distribution point for CRLs?
Question 125
A network engineer is deciding whether to use stateful or stateless failover when configuring two ASAs for high availability. What is the connection status in both cases?


