- Home
- Cisco Certification
- 350-701 Exam
- Cisco.350-701.v2025-10-04.q562 Practice Test
Question 506
A network engineer is configuring DMVPN and entered the crypto is akmp key cisc0380739941 address 0.0.0.0 command on host A The tunnel is not being established to host B.
What action is needed to authenticate the VPN?
What action is needed to authenticate the VPN?
Correct Answer: C
Question 507
Which two activities can be done using Cisco DNA Center? (Choose two)
Correct Answer: B,E
Cisco DNA Center has four general sections aligned to IT workflows: Design: Design your network for consistent configurations by device and by site. Physical maps and logical topologies help provide quick visual reference. The direct import feature brings in existing maps, images, and topologies directly from Cisco Prime Infrastructure and the Cisco Application Policy Infrastructure Controller Enterprise Module (APIC-EM), making upgrades easy and quick. Device configurations by site can be consolidated in a "golden image" that can be used to automatically provision new network devices. These new devices can either be pre-staged by associating the device details and mapping to a site. Or they can be claimed upon connection and mapped to the site. Policy: Translate business intent into network policies and apply those policies, such as access control, traffic routing, and quality of service, consistently over the entire wired and wireless infrastructure. Policy-based access control and network segmentation is a critical function of the Cisco Software-Defined Access (SDAccess) solution built from Cisco DNA Center and Cisco Identity Services Engine (ISE). Cisco AI Network Analytics and Cisco Group-Based Policy Analytics running in the Cisco DNA Center identify endpoints, group similar endpoints, and determine group communication behavior. Cisco DNA Center then facilitates creating policies that determine the form of communication allowed between and within members of each group. ISE then activates the underlying infrastructure and segments the network creating a virtual overlay to follow these policies consistently. Such segmenting implements zero-trust security in the workplace, reduces risk, contains threats, and helps verify regulatory compliance by giving endpoints just the right level of access they need. Provision: Once you have created policies in Cisco DNA Center, provisioning is a simple drag-and-drop task. The profiles (called scalable group tags or "SGTs") in the Cisco DNA Center inventory list are assigned a policy, and this policy will always follow the identity. The process is completely automated and zero-touch. New devices added to the network are assigned to an SGT based on identity-greatly facilitating remote office setups. Assurance: Cisco DNA Assurance, using AI/ML, enables every point on the network to become a sensor, sending continuous streaming telemetry on application performance and user connectivity in real time. The clean and simple dashboard shows detailed network health and flags issues. Then, guided remediation automates resolution to keep your network performing at its optimal with less mundane troubleshooting work. The outcome is a consistent experience and proactive optimization of your network, with less time spent on troubleshooting tasks. Reference: https://www.cisco.com/c/en/us/products/collateral/cloud-systems-management/dna-center/nb-06- dna-center-so-cte-en.html Design: Design your network for consistent configurations by device and by site. Physical maps and logical topologies help provide quick visual reference. The direct import feature brings in existing maps, images, and topologies directly from Cisco Prime Infrastructure and the Cisco Application Policy Infrastructure Controller Enterprise Module (APIC-EM), making upgrades easy and quick. Device configurations by site can be consolidated in a "golden image" that can be used to automatically provision new network devices. These new devices can either be pre-staged by associating the device details and mapping to a site. Or they can be claimed upon connection and mapped to the site.
Policy: Translate business intent into network policies and apply those policies, such as access control, traffic routing, and quality of service, consistently over the entire wired and wireless infrastructure. Policy-based access control and network segmentation is a critical function of the Cisco Software-Defined Access (SDAccess) solution built from Cisco DNA Center and Cisco Identity Services Engine (ISE). Cisco AI Network Analytics and Cisco Group-Based Policy Analytics running in the Cisco DNA Center identify endpoints, group similar endpoints, and determine group communication behavior. Cisco DNA Center then facilitates creating policies that determine the form of communication allowed between and within members of each group. ISE then activates the underlying infrastructure and segments the network creating a virtual overlay to follow these policies consistently. Such segmenting implements zero-trust security in the workplace, reduces risk, contains threats, and helps verify regulatory compliance by giving endpoints just the right level of access they need.
Provision: Once you have created policies in Cisco DNA Center, provisioning is a simple drag-and-drop task.
The profiles (called scalable group tags or "SGTs") in the Cisco DNA Center inventory list are assigned a policy, and this policy will always follow the identity. The process is completely automated and zero-touch. New devices added to the network are assigned to an SGT based on identity-greatly facilitating remote office setups.
Assurance: Cisco DNA Assurance, using AI/ML, enables every point on the network to become a sensor, sending continuous streaming telemetry on application performance and user connectivity in real time. The clean and simple dashboard shows detailed network health and flags issues. Then, guided remediation automates resolution to keep your network performing at its optimal with less mundane troubleshooting work.
The outcome is a consistent experience and proactive optimization of your network, with less time spent on troubleshooting tasks.
Cisco DNA Center has four general sections aligned to IT workflows: Design: Design your network for consistent configurations by device and by site. Physical maps and logical topologies help provide quick visual reference. The direct import feature brings in existing maps, images, and topologies directly from Cisco Prime Infrastructure and the Cisco Application Policy Infrastructure Controller Enterprise Module (APIC-EM), making upgrades easy and quick. Device configurations by site can be consolidated in a "golden image" that can be used to automatically provision new network devices. These new devices can either be pre-staged by associating the device details and mapping to a site. Or they can be claimed upon connection and mapped to the site. Policy: Translate business intent into network policies and apply those policies, such as access control, traffic routing, and quality of service, consistently over the entire wired and wireless infrastructure. Policy-based access control and network segmentation is a critical function of the Cisco Software-Defined Access (SDAccess) solution built from Cisco DNA Center and Cisco Identity Services Engine (ISE). Cisco AI Network Analytics and Cisco Group-Based Policy Analytics running in the Cisco DNA Center identify endpoints, group similar endpoints, and determine group communication behavior. Cisco DNA Center then facilitates creating policies that determine the form of communication allowed between and within members of each group. ISE then activates the underlying infrastructure and segments the network creating a virtual overlay to follow these policies consistently. Such segmenting implements zero-trust security in the workplace, reduces risk, contains threats, and helps verify regulatory compliance by giving endpoints just the right level of access they need. Provision: Once you have created policies in Cisco DNA Center, provisioning is a simple drag-and-drop task. The profiles (called scalable group tags or "SGTs") in the Cisco DNA Center inventory list are assigned a policy, and this policy will always follow the identity. The process is completely automated and zero-touch. New devices added to the network are assigned to an SGT based on identity-greatly facilitating remote office setups. Assurance: Cisco DNA Assurance, using AI/ML, enables every point on the network to become a sensor, sending continuous streaming telemetry on application performance and user connectivity in real time. The clean and simple dashboard shows detailed network health and flags issues. Then, guided remediation automates resolution to keep your network performing at its optimal with less mundane troubleshooting work. The outcome is a consistent experience and proactive optimization of your network, with less time spent on troubleshooting tasks. Reference: https://www.cisco.com/c/en/us/products/collateral/cloud-systems-management/dna-center/nb-06- dna-center-so-cte-en.html
Policy: Translate business intent into network policies and apply those policies, such as access control, traffic routing, and quality of service, consistently over the entire wired and wireless infrastructure. Policy-based access control and network segmentation is a critical function of the Cisco Software-Defined Access (SDAccess) solution built from Cisco DNA Center and Cisco Identity Services Engine (ISE). Cisco AI Network Analytics and Cisco Group-Based Policy Analytics running in the Cisco DNA Center identify endpoints, group similar endpoints, and determine group communication behavior. Cisco DNA Center then facilitates creating policies that determine the form of communication allowed between and within members of each group. ISE then activates the underlying infrastructure and segments the network creating a virtual overlay to follow these policies consistently. Such segmenting implements zero-trust security in the workplace, reduces risk, contains threats, and helps verify regulatory compliance by giving endpoints just the right level of access they need.
Provision: Once you have created policies in Cisco DNA Center, provisioning is a simple drag-and-drop task.
The profiles (called scalable group tags or "SGTs") in the Cisco DNA Center inventory list are assigned a policy, and this policy will always follow the identity. The process is completely automated and zero-touch. New devices added to the network are assigned to an SGT based on identity-greatly facilitating remote office setups.
Assurance: Cisco DNA Assurance, using AI/ML, enables every point on the network to become a sensor, sending continuous streaming telemetry on application performance and user connectivity in real time. The clean and simple dashboard shows detailed network health and flags issues. Then, guided remediation automates resolution to keep your network performing at its optimal with less mundane troubleshooting work.
The outcome is a consistent experience and proactive optimization of your network, with less time spent on troubleshooting tasks.
Cisco DNA Center has four general sections aligned to IT workflows: Design: Design your network for consistent configurations by device and by site. Physical maps and logical topologies help provide quick visual reference. The direct import feature brings in existing maps, images, and topologies directly from Cisco Prime Infrastructure and the Cisco Application Policy Infrastructure Controller Enterprise Module (APIC-EM), making upgrades easy and quick. Device configurations by site can be consolidated in a "golden image" that can be used to automatically provision new network devices. These new devices can either be pre-staged by associating the device details and mapping to a site. Or they can be claimed upon connection and mapped to the site. Policy: Translate business intent into network policies and apply those policies, such as access control, traffic routing, and quality of service, consistently over the entire wired and wireless infrastructure. Policy-based access control and network segmentation is a critical function of the Cisco Software-Defined Access (SDAccess) solution built from Cisco DNA Center and Cisco Identity Services Engine (ISE). Cisco AI Network Analytics and Cisco Group-Based Policy Analytics running in the Cisco DNA Center identify endpoints, group similar endpoints, and determine group communication behavior. Cisco DNA Center then facilitates creating policies that determine the form of communication allowed between and within members of each group. ISE then activates the underlying infrastructure and segments the network creating a virtual overlay to follow these policies consistently. Such segmenting implements zero-trust security in the workplace, reduces risk, contains threats, and helps verify regulatory compliance by giving endpoints just the right level of access they need. Provision: Once you have created policies in Cisco DNA Center, provisioning is a simple drag-and-drop task. The profiles (called scalable group tags or "SGTs") in the Cisco DNA Center inventory list are assigned a policy, and this policy will always follow the identity. The process is completely automated and zero-touch. New devices added to the network are assigned to an SGT based on identity-greatly facilitating remote office setups. Assurance: Cisco DNA Assurance, using AI/ML, enables every point on the network to become a sensor, sending continuous streaming telemetry on application performance and user connectivity in real time. The clean and simple dashboard shows detailed network health and flags issues. Then, guided remediation automates resolution to keep your network performing at its optimal with less mundane troubleshooting work. The outcome is a consistent experience and proactive optimization of your network, with less time spent on troubleshooting tasks. Reference: https://www.cisco.com/c/en/us/products/collateral/cloud-systems-management/dna-center/nb-06- dna-center-so-cte-en.html
Question 508
Which threat intelligence standard contains malware hashes?
Correct Answer: D
The threat intelligence standard that contains malware hashes is trusted automated exchange of indicator information (TAXII). TAXII is a protocol that enables the exchange of cyber threat information in a standardized and automated manner. It supports various types of threat intelligence, such as indicators of compromise (IOCs), observables, incidents, tactics, techniques, and procedures (TTPs), and campaigns.
Malware hashes are one example of IOCs that can be shared using TAXII. Malware hashes are cryptographic signatures that uniquely identify malicious files or programs. They can be used to detect and block malware infections on endpoints or networks. TAXII uses STIX (structured threat information expression) as the data format for representing threat intelligence. STIX is a language that defines a common vocabulary and structure for describing cyber threat information. STIX allows threat intelligence producers and consumers to share information in a consistent and interoperable way. STIX defines various objects and properties that can be used to represent different aspects of cyber threat information, such as indicators, observables, incidents, TTPs, campaigns, threat actors, courses of action, and relationships. Malware hashes can be expressed as observables in STIX, which are concrete items or events that are observable in the operational domain.
Observables can have various types, such as file, process, registry key, URL, IP address, domain name, etc.
Each observable type has a set of attributes that describe its properties. For example, a file observable can have attributes such as name, size, type, hashes, magic number, etc. A hash attribute can have a type (such as MD5, SHA1, SHA256, etc.) and a value (such as the hexadecimal representation of the hash). A file observable can have one or more hash attributes to represent different hashing algorithms applied to the same file. For example, a file observable can have both MD5 and SHA256 hashes to increase the confidence and accuracy of identifying the file.
The other options are incorrect because they are not threat intelligence standards that contain malware hashes.
Option A is incorrect because advanced persistent threat (APT) is not a standard, but a term that describes a stealthy and sophisticated cyberattack that aims to compromise and maintain access to a target network or system over a long period of time. Option B is incorrect because open command and control (OpenC2) is not a standard that contains malware hashes, but a language that enables the command and control of cyber defense components, such as sensors, actuators, and orchestrators. Option C is incorrect because structured threat information expression (STIX) is not a standard that contains malware hashes, but a data format that represents threat intelligence. STIX uses TAXII as the transport protocol for exchanging threat intelligence, including malware hashes. References:
* TAXII
* STIX
* Malware Hashes
Malware hashes are one example of IOCs that can be shared using TAXII. Malware hashes are cryptographic signatures that uniquely identify malicious files or programs. They can be used to detect and block malware infections on endpoints or networks. TAXII uses STIX (structured threat information expression) as the data format for representing threat intelligence. STIX is a language that defines a common vocabulary and structure for describing cyber threat information. STIX allows threat intelligence producers and consumers to share information in a consistent and interoperable way. STIX defines various objects and properties that can be used to represent different aspects of cyber threat information, such as indicators, observables, incidents, TTPs, campaigns, threat actors, courses of action, and relationships. Malware hashes can be expressed as observables in STIX, which are concrete items or events that are observable in the operational domain.
Observables can have various types, such as file, process, registry key, URL, IP address, domain name, etc.
Each observable type has a set of attributes that describe its properties. For example, a file observable can have attributes such as name, size, type, hashes, magic number, etc. A hash attribute can have a type (such as MD5, SHA1, SHA256, etc.) and a value (such as the hexadecimal representation of the hash). A file observable can have one or more hash attributes to represent different hashing algorithms applied to the same file. For example, a file observable can have both MD5 and SHA256 hashes to increase the confidence and accuracy of identifying the file.
The other options are incorrect because they are not threat intelligence standards that contain malware hashes.
Option A is incorrect because advanced persistent threat (APT) is not a standard, but a term that describes a stealthy and sophisticated cyberattack that aims to compromise and maintain access to a target network or system over a long period of time. Option B is incorrect because open command and control (OpenC2) is not a standard that contains malware hashes, but a language that enables the command and control of cyber defense components, such as sensors, actuators, and orchestrators. Option C is incorrect because structured threat information expression (STIX) is not a standard that contains malware hashes, but a data format that represents threat intelligence. STIX uses TAXII as the transport protocol for exchanging threat intelligence, including malware hashes. References:
* TAXII
* STIX
* Malware Hashes
Question 509
Drag and drop the Firepower Next Generation Intrusion Prevention System detectors from the left onto the correct definitions on the right.
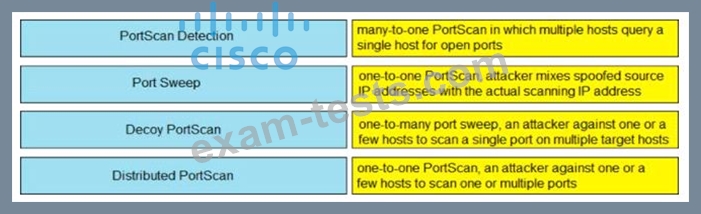

Correct Answer:
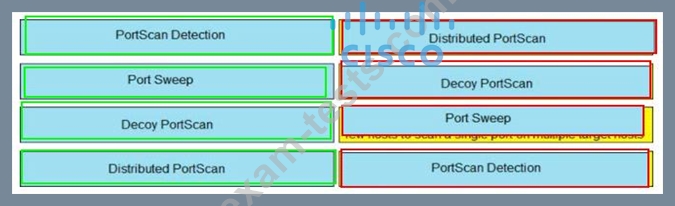
Question 510
What is the purpose of the Cisco Endpoint loC feature?
Correct Answer: C
https://www.cisco.com/c/dam/en_us/about/doing_business/legal/service_descriptions/docs/Cisco_Secure_Managed_Endpoint.pdf
- Other Version
- 1077Cisco.350-701.v2025-06-19.q238
- 1556Cisco.350-701.v2024-12-18.q472
- 2721Cisco.350-701.v2023-08-01.q405
- 3409Cisco.350-701.v2023-05-04.q372
- 2329Cisco.350-701.v2023-03-16.q218
- 7311Cisco.350-701.v2022-10-19.q571
- 7259Cisco.350-701.v2022-07-08.q453
- 4200Cisco.350-701.v2022-02-02.q204
- 116Cisco.Prepawaypdf.350-701.v2021-12-15.by.ellen.316q.pdf
- Latest Upload
- 126USGBC.LEED-AP-Homes.v2026-01-02.q36
- 115SAP.C-THR94-2505.v2026-01-02.q29
- 135MedicalProfessional.CHFM.v2026-01-01.q37
- 116SAP.C-BCSPM-2502.v2026-01-01.q9
- 118Microsoft.MB-335.v2026-01-01.q142
- 120SAP.C_THR70_2505.v2026-01-01.q55
- 157Salesforce.Financial-Services-Cloud.v2026-01-01.q121
- 183Fortinet.FCSS_SDW_AR-7.4.v2025-12-31.q73
- 163UiPath.UiPath-SAIAv1.v2025-12-30.q89
- 215HP.HPE0-V25.v2025-12-29.q138
[×]
Download PDF File
Enter your email address to download Cisco.350-701.v2025-10-04.q562 Practice Test

