Question 96
A company is outsourcing to an MSSP that performs managed detection and response services. The MSSP requires a server to be placed inside the network as a log aggregate and allows remote access to MSSP analyst. Critical devices send logs to the log aggregator, where data is stored for 12 months locally before being archived to a multitenant cloud. The data is then sent from the log aggregate to a public IP address in the MSSP datacenter for analysis.
A security engineer is concerned about the security of the solution and notes the following.
* The critical devise send cleartext logs to the aggregator.
* The log aggregator utilize full disk encryption.
* The log aggregator sends to the analysis server via port 80.
* MSSP analysis utilize an SSL VPN with MFA to access the log aggregator remotely.
* The data is compressed and encrypted prior to being achieved in the cloud.
Which of the following should be the engineer's GREATEST concern?
A security engineer is concerned about the security of the solution and notes the following.
* The critical devise send cleartext logs to the aggregator.
* The log aggregator utilize full disk encryption.
* The log aggregator sends to the analysis server via port 80.
* MSSP analysis utilize an SSL VPN with MFA to access the log aggregator remotely.
* The data is compressed and encrypted prior to being achieved in the cloud.
Which of the following should be the engineer's GREATEST concern?
Question 97
A security analyst is reading the results of a successful exploit that was recently conducted by third-party penetration testers. The testers reverse engineered a privileged executable. In the report, the planning and execution of the exploit is detailed using logs and outputs from the test However, the attack vector of the exploit is missing, making it harder to recommend remediation's. Given the following output:
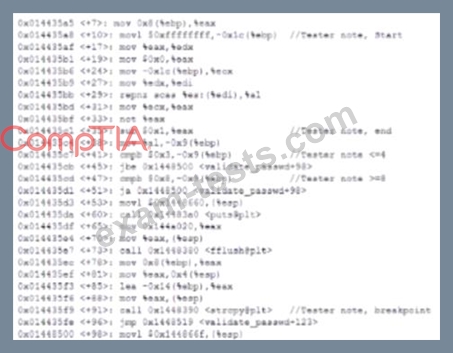
The penetration testers MOST likely took advantage of:

The penetration testers MOST likely took advantage of:
Question 98
An application development company implements object reuse to reduce life-cycle costs for the company and its clients Despite the overall cost savings, which of the following BEST describes a security risk to customers inherent within this model?
Question 99
During an audit, it was determined from a sample that four out of 20 former employees were still accessing their email accounts An information security analyst is reviewing the access to determine if the audit was valid Which of the following would assist with the validation and provide the necessary documentation to audit?
Question 100
A Chief Information Security Officer (CISO) is working with a consultant to perform a gap assessment prior to an upcoming audit. It is determined during the assessment that the organization lacks controls to effectively assess regulatory compliance by third-party service providers. Which of the following should be revised to address this gap?

