Question 81
An enterprise is trying to secure a specific web-based application by forcing the use of multifactor authentication. Currently, the enterprise cannot change the application's sign-in page to include an extra field. However, the web-based application supports SAML. Which of the following would BEST secure the application?
Question 82
Given the following output from a local PC:
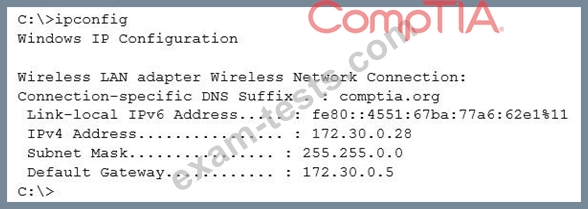
Which of the following ACLs on a stateful host-based firewall would allow the PC to serve an intranet website?

Which of the following ACLs on a stateful host-based firewall would allow the PC to serve an intranet website?
Question 83
A company is developing requirements for a customized OS build that will be used in an embedded environment. The company procured hardware that is capable of reducing the likelihood of successful buffer overruns while executables are processing. Which of the following capabilities must be included for the OS to take advantage of this critical hardware-based countermeasure?
Question 84
A security analyst is reviewing the following company requirements prior to selecting the appropriate technical control configuration and parameter:
RTO:2 days
RPO:36 hours
MTTR:24 hours
MTBF:60 days
Which of the following solutions will address the RPO requirements?
RTO:2 days
RPO:36 hours
MTTR:24 hours
MTBF:60 days
Which of the following solutions will address the RPO requirements?
Question 85
A security analyst is attempting to break into a client's secure network. The analyst was not given prior information about the client, except for a block of public IP addresses that are currently in use. After network enumeration, the analyst's NEXT step is to perform:
Premium Bundle
Newest CAS-003 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing CAS-003 Exam! BraindumpsPass.com now offer the updated CAS-003 exam dumps, the BraindumpsPass.com CAS-003 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com CAS-003 pdf dumps with Exam Engine here:

