Question 156
A request has been approved for a vendor to access a new internal server using only HTTPS and SSH to manage the back-end system for the portal. Internal users just need HTTP and HTTPS access to all internal web servers. All other external access to the new server and its subnet is not allowed. The security manager must ensure proper access is configured.
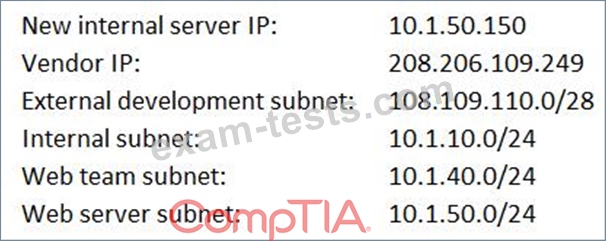
Below is a snippet from the firewall related to that server (access is provided in a top-down model):
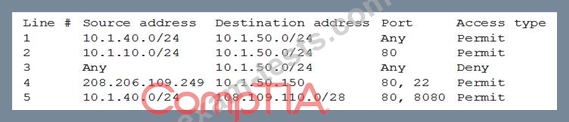
Which of the following lines should be configured to allow the proper access? (Choose two.)

Below is a snippet from the firewall related to that server (access is provided in a top-down model):

Which of the following lines should be configured to allow the proper access? (Choose two.)
Question 157
An incident responder wants to capture volatile memory comprehensively from a running machine for forensic purposes. The machine is running a very recent release of the Linux OS.
Which of the following technical approaches would be the MOST feasible way to accomplish this capture?
Which of the following technical approaches would be the MOST feasible way to accomplish this capture?
Question 158
A government contractor was the victim of a malicious attack that resulted in the theft of sensitive information. An analyst's subsequent investigation of sensitive systems led to the following discoveries:
There was no indication of the data owner's or user's accounts being compromised.
No database activity outside of previous baselines was discovered.
All workstations and servers were fully patched for all known vulnerabilities at the time of the attack.
It was likely not an insider threat, as all employees passed polygraph tests.
Given this scenario, which of the following is the MOST likely attack that occurred?
There was no indication of the data owner's or user's accounts being compromised.
No database activity outside of previous baselines was discovered.
All workstations and servers were fully patched for all known vulnerabilities at the time of the attack.
It was likely not an insider threat, as all employees passed polygraph tests.
Given this scenario, which of the following is the MOST likely attack that occurred?
Question 159
A security engineer reviews the table below:
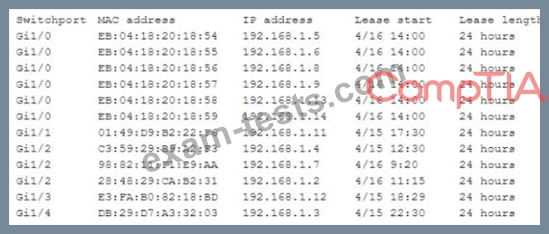
The engineer realizes there is an active attack occurring on the network. Which of the following would BEST reduce the risk of this attack reoccurring m the future?

The engineer realizes there is an active attack occurring on the network. Which of the following would BEST reduce the risk of this attack reoccurring m the future?
Question 160
A Chief Information Security Officer (CISO) is running a test to evaluate the security of the corporate network and attached devices. Which of the following components should be executed by an outside vendor?

