Question 161
The Chief Executive Officer (CEO) of a small startup company has an urgent need for a security policy and assessment to address governance, risk management, and compliance. The company has a resource-constrained IT department, but has no information security staff. The CEO has asked for this to be completed in three months.
Which of the following would be the MOST cost-effective solution to meet the company's needs?
Which of the following would be the MOST cost-effective solution to meet the company's needs?
Question 162
A security analyst is investigating a series of suspicious emails by employees to the security team. The email appear to come from a current business partner and do not contain images or URLs. No images or URLs were stripped from the message by the security tools the company uses instead, the emails only include the following in plain text.

Which of the following should the security analyst perform?

Which of the following should the security analyst perform?
Question 163
A security engineer is assisting a developer with input validation, and they are studying the following code block:
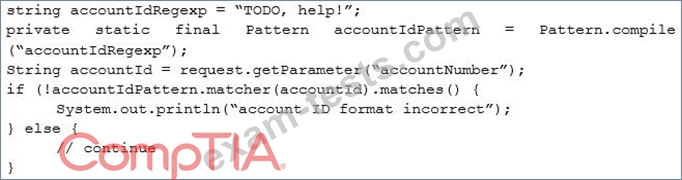
The security engineer wants to ensure strong input validation is in place for customer-provided account identifiers. These identifiers are ten-digit numbers. The developer wants to ensure input validation is fast because a large number of people use the system.
Which of the following would be the BEST advice for the security engineer to give to the developer?

The security engineer wants to ensure strong input validation is in place for customer-provided account identifiers. These identifiers are ten-digit numbers. The developer wants to ensure input validation is fast because a large number of people use the system.
Which of the following would be the BEST advice for the security engineer to give to the developer?
Question 164
A company is purchasing an application that will be used to manage all IT assets as well as provide an incident and problem management solution for IT activity The company narrows the search to two products. Application A and Application B; which meet all of its requirements. Application A is the most cost-effective product, but it is also the riskiest so the company purchases Application B.
Which of the following types of strategies did the company use when determining risk appetite?
Which of the following types of strategies did the company use when determining risk appetite?
Question 165
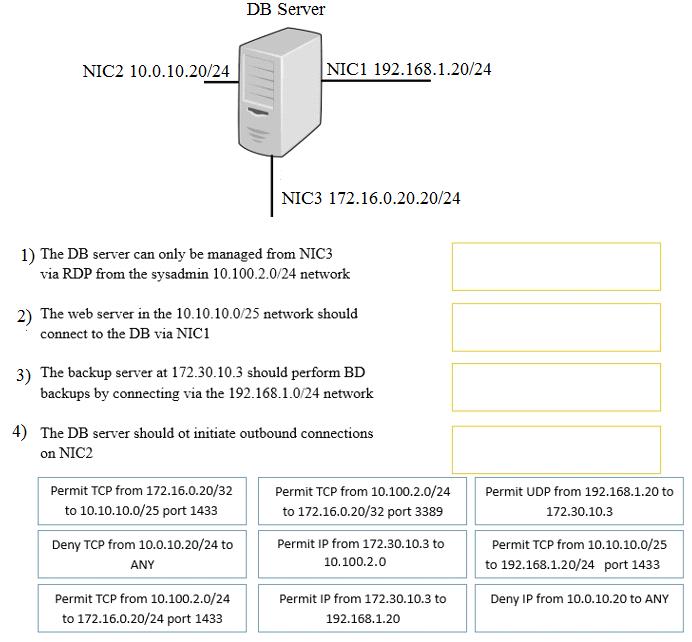
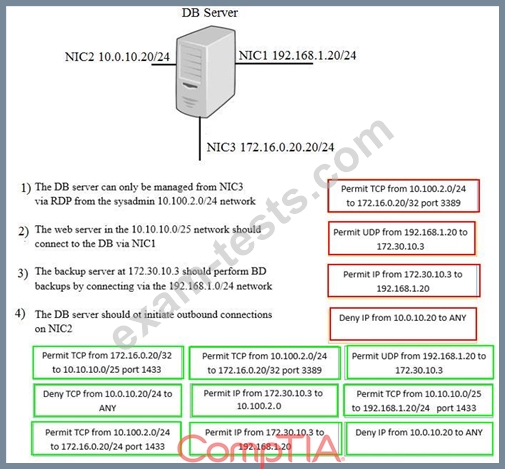
A security administrator must configure the database server shown below to comply with the four requirements listed. Drag and drop the appropriate ACL that should be configured on the database server to its corresponding requirement. Answer options may be used once or not at all.