Question 176
A security analyst is reviewing the following pseudo-output snippet after running the command less /tmp/file,tmp.
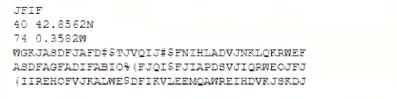
The information above was obtained from a public-facing website and used to identify military assets. Which of the following should be implemented to reduce the risk of a similar compromise?

The information above was obtained from a public-facing website and used to identify military assets. Which of the following should be implemented to reduce the risk of a similar compromise?
Question 177
The SOC has noticed an unusual volume of traffic coming from an open WiFi guest network that appears correlated with a broader network slowdown The network team is unavailable to capture traffic but logs from network services are available
* No users have authenticated recently through the guest network's captive portal
* DDoS mitigation systems are not alerting
* DNS resolver logs show some very long domain names
Which of the following is the BEST step for a security analyst to take next?
* No users have authenticated recently through the guest network's captive portal
* DDoS mitigation systems are not alerting
* DNS resolver logs show some very long domain names
Which of the following is the BEST step for a security analyst to take next?
Question 178
A company recently experienced a period of rapid growth, and it now needs to move to a more scalable cloud-based solution Historically. salespeople have maintained separate systems for information on competing customers to prevent the inadvertent disclosure of one customer's information to another customer Which of the following would be the BEST method to provide secure data separation?
Question 179
The director of sales asked the development team for some small changes to increase the usability of an application used by the sales team. Prior security reviews of the code showed no significant vulnerabilities, and since the changes were small, they were given a peer review and then pushed to the live environment. Subsequent vulnerability scans now show numerous flaws that were not present in the previous versions of the code. Which of the following is an SDLC best practice that should have been followed?
Question 180
An organization implemented a secure boot on its most critical application servers which produce content and capability for other consuming servers A recent incident, however led the organization to implement a centralized attestation service for these critical servers. Which of the following MOST likely explains the nature of the incident that caused the organization to implement this remediation?

