Question 46
Company XYZ finds itself using more cloud-based business tools, and password management is becoming onerous. Security is important to the company; as a result, password replication and shared accounts are not acceptable. Which of the following implementations addresses the distributed login with centralized authentication and has wide compatibility among SaaS vendors?
Question 47
The Chief Executive Officer (CEO) of a large prestigious enterprise has decided to reduce business costs by outsourcing to a third party company in another country. Functions to be outsourced include: business analysts, testing, software development and back office functions that deal with the processing of customer data. The Chief Risk Officer (CRO) is concerned about the outsourcing plans. Which of the following risks are MOST likely to occur if adequate controls are not implemented?
Question 48
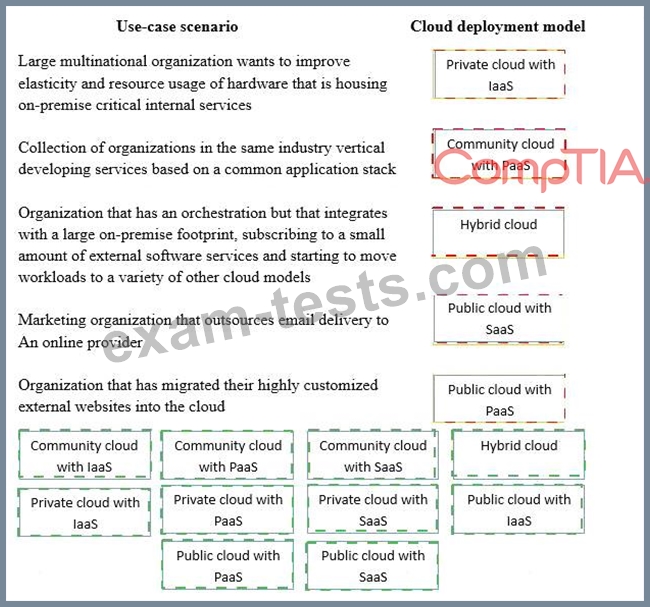
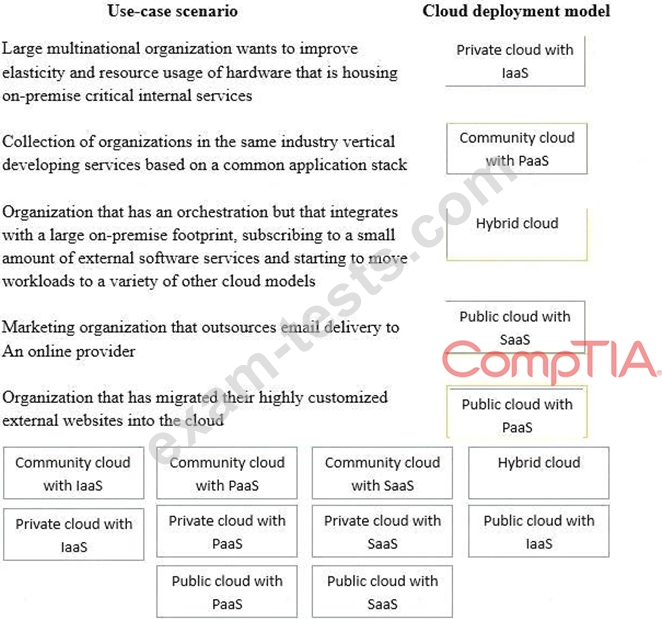
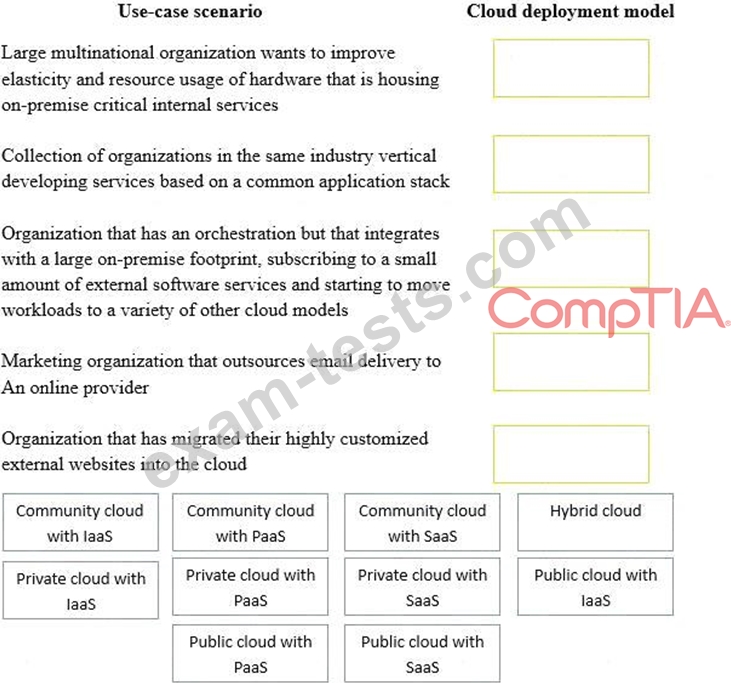
Drag and drop the cloud deployment model to the associated use-case scenario. Options may be used only once or not at all.

Question 49
A company wants to perform analysis of a tool that is suspected to contain a malicious payload.
A forensic analyst is given the following snippet:
^32^[34fda19(fd^43gfd/home/user/lib/module.so.343jk^rfw(342fds43g
Which of the following did the analyst use to determine the location of the malicious payload?
A forensic analyst is given the following snippet:
^32^[34fda19(fd^43gfd/home/user/lib/module.so.343jk^rfw(342fds43g
Which of the following did the analyst use to determine the location of the malicious payload?
Question 50
A security technician receives a copy of a report that was originally sent to the board of directors by the Chief Information Security Officer (CISO).
The report outlines the following KPI/KRI data for the last 12 months:
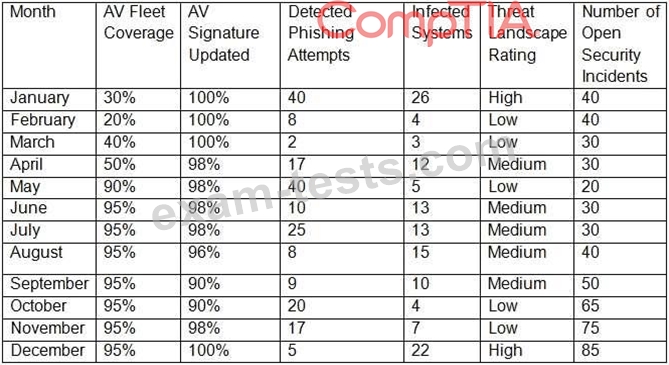
Which of the following BEST describes what could be interpreted from the above data?
The report outlines the following KPI/KRI data for the last 12 months:

Which of the following BEST describes what could be interpreted from the above data?