Question 61
A company in the financial sector receives a substantial number of customer transaction requests via email. While doing a root-cause analysis conceding a security breach, the CIRT correlates an unusual spike in port 80 traffic from the IP address of a desktop used by a customer relations employee who has access to several of the compromised accounts. Subsequent antivirus scans of the device do not return an findings, but the CIRT finds undocumented services running on the device. Which of the following controls would reduce the discovery time for similar in the future.
Question 62
A company is planning to undergo a P2V project to improve resource utilisation redundancy, and failover across its two datacenters A consultant has provided a private cloud design that uses a specific Type 1 hypervisor based on Linux. The security manager is concerned about the integrity of the hypervisor Which of the following should the consultant suggest to address the security manager's concerns?
Question 63
A product owner is reviewing the output of a web-application penetration test and has identified an application that is presenting sensitive information in cleartext on a page. Which of the following code snippets would be BEST to use to remediate the vulnerability?
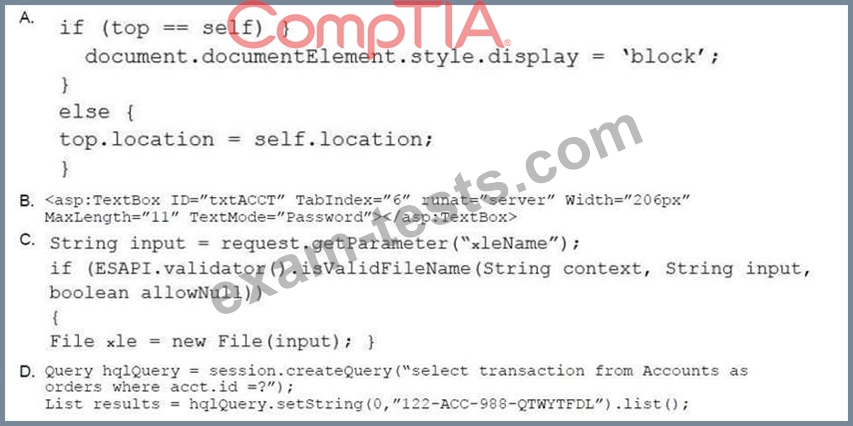

Question 64
A penetration test is being scoped for a set of web services with API endpoints. The APIs will be hosted on existing web application servers. Some of the new APIs will be available to unauthenticated users, but some will only be available to authenticated users. Which of the following tools or activities would the penetration tester MOST likely use or do during the engagement? (Select TWO.)
Question 65
Developers are working on anew feature to add to a social media platform. Thew new feature involves
users uploading pictures of what they are currently doing. The data privacy officer (DPO) is concerned
about various types of abuse that might occur due to this new feature. The DPO state the new feature
cannot be released without addressing the physical safety concerns of the platform's users. Which of the
following controls would BEST address the DPO's concerns?
users uploading pictures of what they are currently doing. The data privacy officer (DPO) is concerned
about various types of abuse that might occur due to this new feature. The DPO state the new feature
cannot be released without addressing the physical safety concerns of the platform's users. Which of the
following controls would BEST address the DPO's concerns?
Premium Bundle
Newest CAS-003 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing CAS-003 Exam! BraindumpsPass.com now offer the updated CAS-003 exam dumps, the BraindumpsPass.com CAS-003 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com CAS-003 pdf dumps with Exam Engine here:

