Question 31
An organization is in the process ofintegrating its operational technology and information technology areas. As part of the integration, some of the cultural aspects it would like to see include more efficient use of resources during change windows, better protection of critical infrastructure, and the ability to respond to incidents. The following observations have been identified:
* The ICS supplier has specified that any software installed will result in lack of support.
* There is no documented trust boundary defined between the SCADA and corporate networks.
* Operational technology staff have to manage the SCADA equipment via the engineering workstation.
* There is a lack of understanding of what is within the SCADA network.
Which of the following capabilities would BEST improve the security position?
* The ICS supplier has specified that any software installed will result in lack of support.
* There is no documented trust boundary defined between the SCADA and corporate networks.
* Operational technology staff have to manage the SCADA equipment via the engineering workstation.
* There is a lack of understanding of what is within the SCADA network.
Which of the following capabilities would BEST improve the security position?
Question 32
A security administrator wants to implement controls to harden company-owned mobile devices. Company policy specifies the following requirements:
* Mandatory access control must be enforced by the OS.
* Devices must only use the mobile carrier data transport.
Which of the following controls should the security administrator implement? (Choose three.)
* Mandatory access control must be enforced by the OS.
* Devices must only use the mobile carrier data transport.
Which of the following controls should the security administrator implement? (Choose three.)
Question 33
An engineer is evaluating the control profile to assign to a system containing PII, financial, and proprietary data.
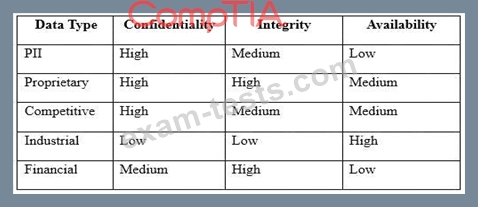
Based on the data classification table above, which of the following BEST describes the overall classification?

Based on the data classification table above, which of the following BEST describes the overall classification?
Question 34
An organization is in the process of integrating its operational technology and information technology areas.
As part of the integration, some of the cultural aspects it would like to see include more efficient use of resources during change windows, better protection of critical infrastructure, and the ability to respond to incidents. The following observations have been identified:
* The ICS supplier has specified that any software installed will result in lack of support.
* There is no documented trust boundary defined between the SCADA and corporate networks.
* Operational technology staff have to manage the SCADA equipment via the engineering workstation.
* There is a lack of understanding of what is within the SCADA network.
Which of the following capabilities would BEST improve the security position?
As part of the integration, some of the cultural aspects it would like to see include more efficient use of resources during change windows, better protection of critical infrastructure, and the ability to respond to incidents. The following observations have been identified:
* The ICS supplier has specified that any software installed will result in lack of support.
* There is no documented trust boundary defined between the SCADA and corporate networks.
* Operational technology staff have to manage the SCADA equipment via the engineering workstation.
* There is a lack of understanding of what is within the SCADA network.
Which of the following capabilities would BEST improve the security position?
Question 35
Two competing companies experienced similar attacks on their networks from various threat actors. To
improve response times, the companies wish to share some threat intelligence about the sources and
methods of attack. Which of the following business documents would be BEST to document this
engagement?
improve response times, the companies wish to share some threat intelligence about the sources and
methods of attack. Which of the following business documents would be BEST to document this
engagement?
Premium Bundle
Newest CAS-003 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing CAS-003 Exam! BraindumpsPass.com now offer the updated CAS-003 exam dumps, the BraindumpsPass.com CAS-003 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com CAS-003 pdf dumps with Exam Engine here:

