Question 76
A security manager is looking into the following vendor proposal for a cloud-based SIEM solution. The intention is that the cost of the SIEM solution will be justified by having reduced the number of incidents and therefore saving on the amount spent investigating incidents.
Proposal:
External cloud-based software as a service subscription costing $5,000 per month. Expected to reduce the number of current incidents per annum by 50%.
The company currently has ten security incidents per annum at an average cost of $10,000 per incident. Which of the following is the ROI for this proposal after three years?
Proposal:
External cloud-based software as a service subscription costing $5,000 per month. Expected to reduce the number of current incidents per annum by 50%.
The company currently has ten security incidents per annum at an average cost of $10,000 per incident. Which of the following is the ROI for this proposal after three years?
Question 77
A company has decided to move an ERP application to a public cloud vendor. The company wants to replicate some of its global policies from on premises to cloud. The policies include data encryption, token management, and limited user access to the ERP application. The Chief Information Officer (CIO) is mainly concerned about privileged accounts that might be compromised and used to alter data in the ERP application. Which of the following is the BEST option to meet the requirements?
Question 78
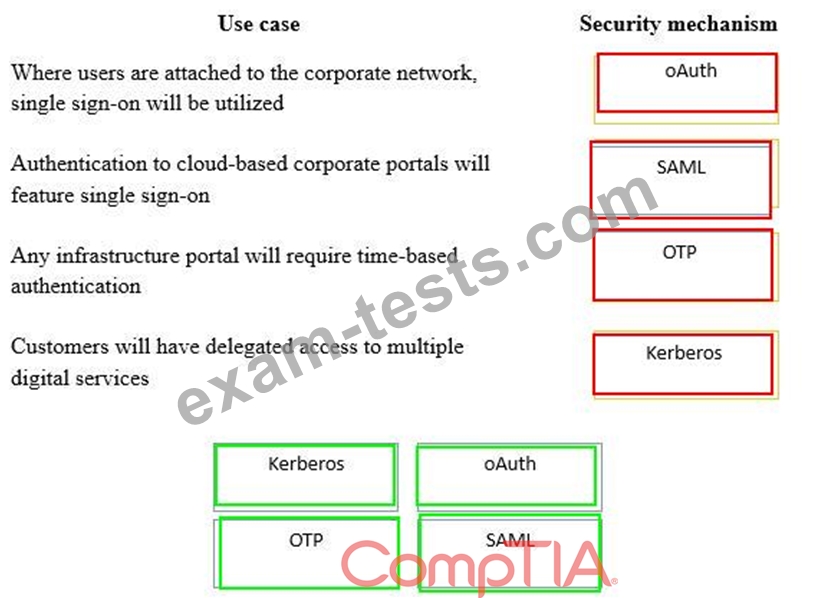
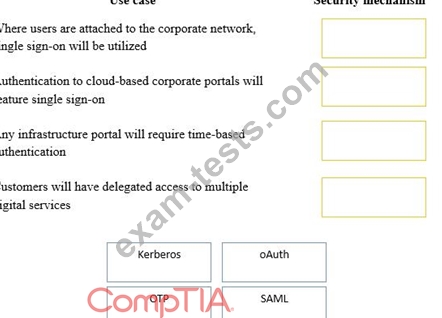
A security consultant is considering authentication options for a financial institution. The following authentication options are available. Drag and drop the security mechanism to the appropriate use case. Options may be used once.

Question 79
A security manager looked at various logs while investigating a recent security breach in the data center from an external source. Each log below was collected from various security devices compiled from a report through the company's security information and event management server.
Logs:
Log 1:
Feb 5 23:55:37.743: %SEC-6-IPACCESSLOGS: list 10 denied 10.2.5.81 3 packets Log 2:
HTTP://www.company.com/index.php?user=aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa Log 3:
Security Error Alert
Event ID 50: The RDP protocol component X.224 detected an error in the protocol stream and has disconnected the client Log 4:
Encoder oe = new OracleEncoder ();
String query = "Select user_id FROM user_data WHERE user_name = ' "
+ oe.encode ( req.getParameter("userID") ) + " ' and user_password = ' "
+ oe.encode ( req.getParameter("pwd") ) +" ' ";
Vulnerabilities
Buffer overflow
SQL injection
ACL
XSS
Which of the following logs and vulnerabilities would MOST likely be related to the security breach? (Select TWO).
Logs:
Log 1:
Feb 5 23:55:37.743: %SEC-6-IPACCESSLOGS: list 10 denied 10.2.5.81 3 packets Log 2:
HTTP://www.company.com/index.php?user=aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa Log 3:
Security Error Alert
Event ID 50: The RDP protocol component X.224 detected an error in the protocol stream and has disconnected the client Log 4:
Encoder oe = new OracleEncoder ();
String query = "Select user_id FROM user_data WHERE user_name = ' "
+ oe.encode ( req.getParameter("userID") ) + " ' and user_password = ' "
+ oe.encode ( req.getParameter("pwd") ) +" ' ";
Vulnerabilities
Buffer overflow
SQL injection
ACL
XSS
Which of the following logs and vulnerabilities would MOST likely be related to the security breach? (Select TWO).
Question 80
The risk subcommittee of a corporate board typically maintains a master register of the most prominent risks to the company. A centralized holistic view of risk is particularly important to the corporate Chief Information Security Officer (CISO) because:
Premium Bundle
Newest CAS-003 Exam PDF Dumps shared by BraindumpsPass.com for Helping Passing CAS-003 Exam! BraindumpsPass.com now offer the updated CAS-003 exam dumps, the BraindumpsPass.com CAS-003 exam questions have been updated and answers have been corrected get the latest BraindumpsPass.com CAS-003 pdf dumps with Exam Engine here: