Question 166
After the install process, a software application executed an online activation process. After a few months, the system experienced a hardware failure. A backup image of the system was restored on a newer revision of the same brand and model device. After the restore, the specialized application no longer works. Which of the following is the MOST likely cause of the problem?
Question 167
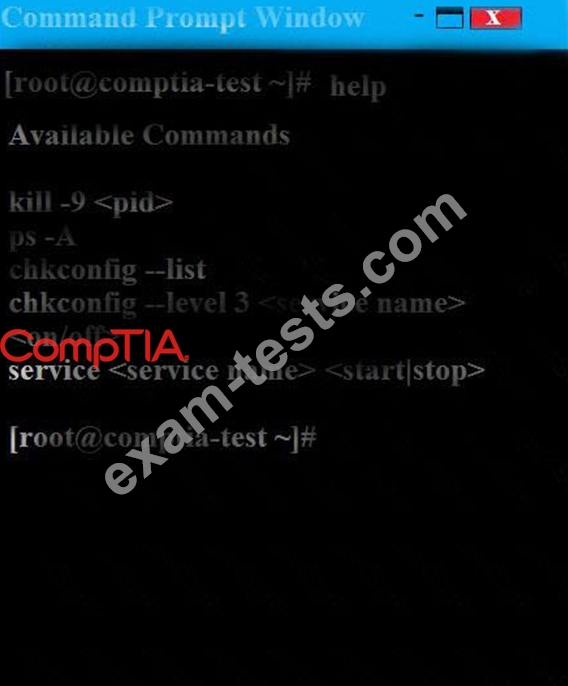
As a security administrator, you are asked to harden a server running Red Hat Enterprise Server 5.5 64-bit.
This server is being used as a DNS and time server. It is not used as a database, web server, or print server.
There are no wireless connections to the server, and it does not need to print.
The command window will be provided along with root access. You are connected via a secure shell with root access.
You may query help for a list of commands.
Instructions:
You need to disable and turn off unrelated services and processes.
It is possible to simulate a crash of your server session. The simulation can be reset, but the server cannot be rebooted. If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.

This server is being used as a DNS and time server. It is not used as a database, web server, or print server.
There are no wireless connections to the server, and it does not need to print.
The command window will be provided along with root access. You are connected via a secure shell with root access.
You may query help for a list of commands.
Instructions:
You need to disable and turn off unrelated services and processes.
It is possible to simulate a crash of your server session. The simulation can be reset, but the server cannot be rebooted. If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.


Question 168
A security analyst has been assigned incident response duties and must instigate the response on a Windows device that appears to be compromised. Which of the following commands should be executed on the client FIRST?
A)
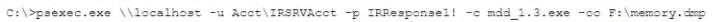
B)
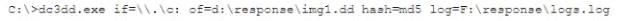
C)

D)
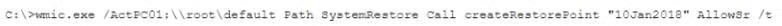
A)
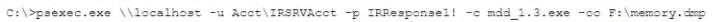
B)
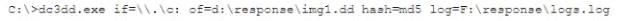
C)

D)
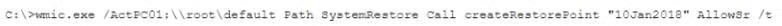
Question 169
A company's user community is being adversely affected by various types of emails whose authenticity cannot be trusted. The Chief Information Security Officer (CISO) must address the problem.
Which of the following solutions would BEST support trustworthy communication solutions?
Which of the following solutions would BEST support trustworthy communication solutions?
Question 170
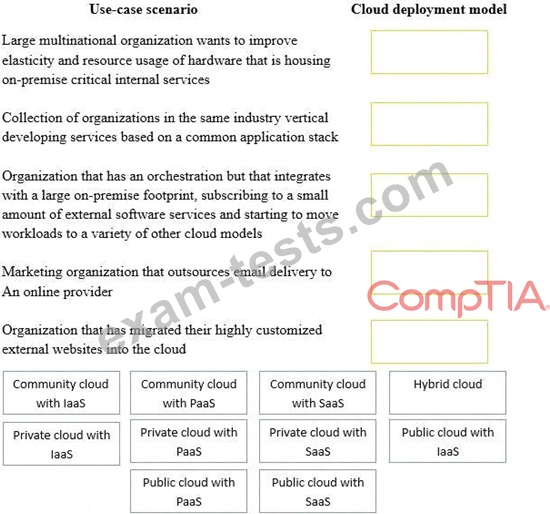
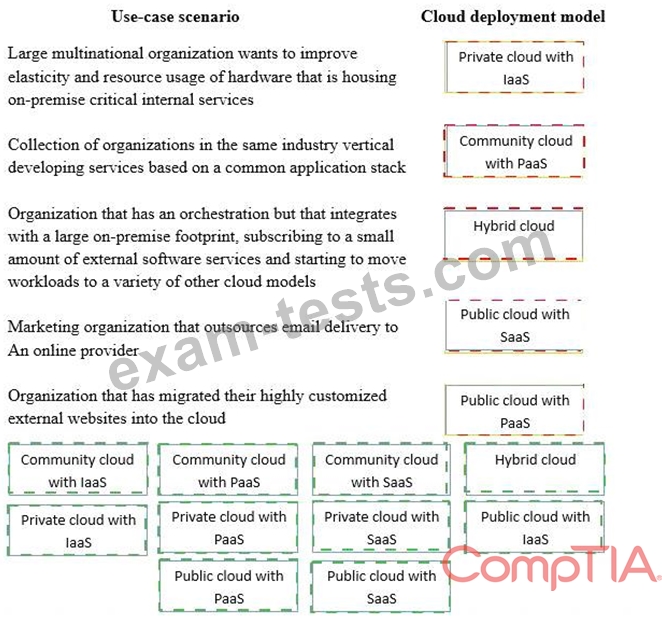
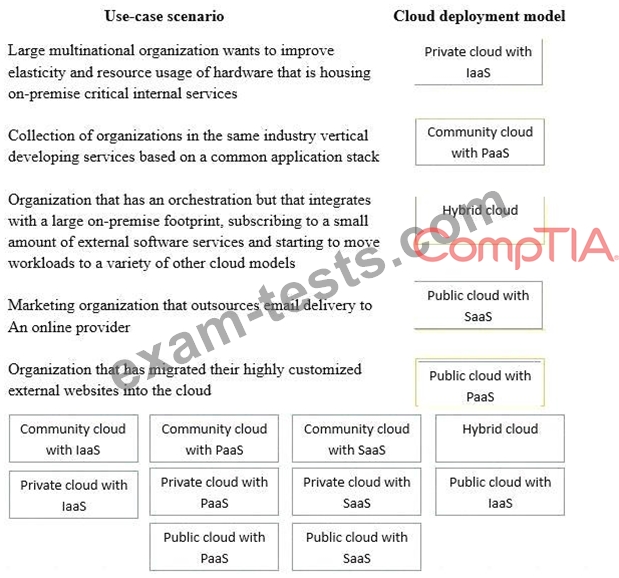
Drag and drop the cloud deployment model to the associated use-case scenario. Options may be used only once or not at all.