Question 146
An organization is in the process of integrating its operational technology and information technology areas. As part of the integration, some of the cultural aspects it would like to see include more efficient use of resources during change windows, better protection of critical infrastructure, and the ability to respond to incidents. The following observations have been identified:
* The ICS supplier has specified that any software installed will result in lack of support.
* There is no documented trust boundary defined between the SCADA and corporate networks.
* Operational technology staff have to manage the SCADA equipment via the engineering workstation.
* There is a lack of understanding of what is within the SCADA network.
Which of the following capabilities would BEST improve the security position?
* The ICS supplier has specified that any software installed will result in lack of support.
* There is no documented trust boundary defined between the SCADA and corporate networks.
* Operational technology staff have to manage the SCADA equipment via the engineering workstation.
* There is a lack of understanding of what is within the SCADA network.
Which of the following capabilities would BEST improve the security position?
Question 147
A security engineer is helping the web developers assess a new corporate web application The application will be Internet facing so the engineer makes the following recommendation:
In an htaccess file or the site config add:
or add to the location block:
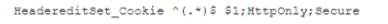
Which of the following is the security engineer trying to accomplish via cookies? (Select TWO)
In an htaccess file or the site config add:
or add to the location block:
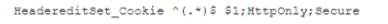
Which of the following is the security engineer trying to accomplish via cookies? (Select TWO)
Question 148
A company contracts a security engineer to perform a penetration test of its client-facing web portal. Which of the following activities would be MOST appropriate?
Question 149
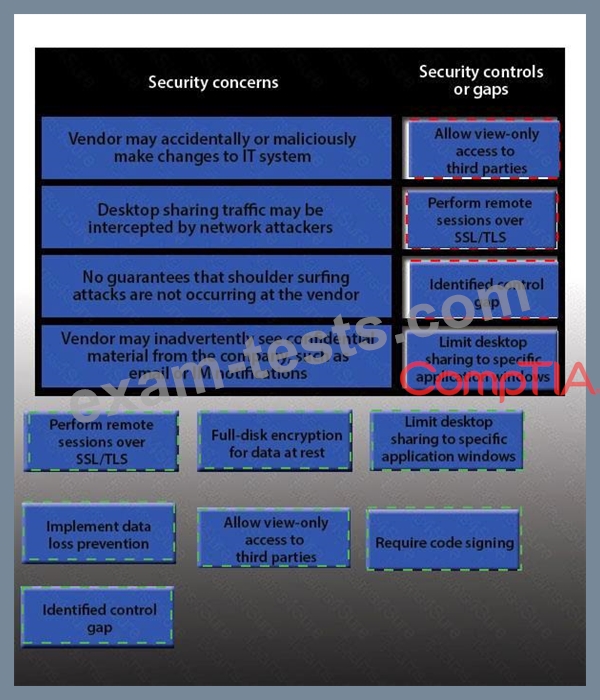
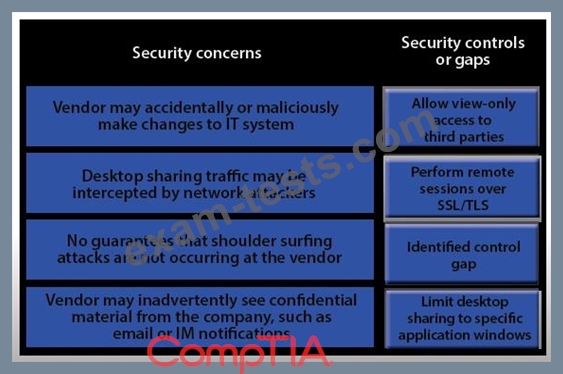
IT staff within a company often conduct remote desktop sharing sessions with vendors to troubleshoot vendor product-related issues. Drag and drop the following security controls to match the associated security concern.
Options may be used once or not at all.
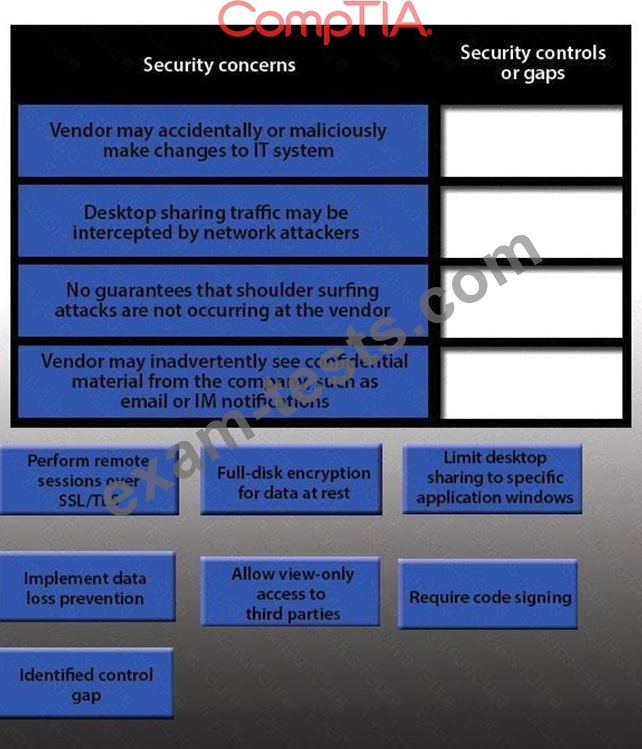
Options may be used once or not at all.

Question 150
A security analyst has requested network engineers integrate sFlow into the SOC's overall monitoring picture.
For this to be a useful addition to the monitoring capabilities, which of the following must be considered by the engineering team?
For this to be a useful addition to the monitoring capabilities, which of the following must be considered by the engineering team?