Question 271
The results of an external penetration test for a software development company show a small number of applications account for the largest number of findings. While analyzing the content and purpose of the applications, the following matrix is created.
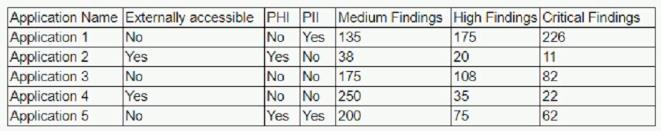
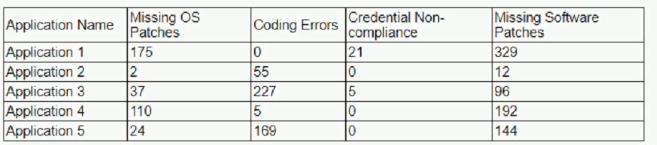
The findings are then categorized according to the following chart:
Which of the following would BEST reduce the amount of immediate risk incurred by the organization from a compliance and legal standpoint? (Select TWO)

The findings are then categorized according to the following chart:

Which of the following would BEST reduce the amount of immediate risk incurred by the organization from a compliance and legal standpoint? (Select TWO)
Question 272
A business is growing and starting to branch out into other locations. In anticipation of opening an office in a different country, the Chief Information Security Officer (CISO) and legal team agree they need to meet the following criteria regarding data to open the new office:
* Store taxation-related documents for five years
* Store customer addresses in an encrypted format
* Destroy customer information after one year
* Keep data only in the customer's home country
Which of the following should the CISO implement to BEST meet these requirements? (Choose three.)
* Store taxation-related documents for five years
* Store customer addresses in an encrypted format
* Destroy customer information after one year
* Keep data only in the customer's home country
Which of the following should the CISO implement to BEST meet these requirements? (Choose three.)
Question 273
A deployment manager is working with a software development group to assess the security of a new version of the organization's internally developed ERP tool. The organization prefers to not perform assessment activities following deployment, instead focusing on assessing security throughout the life cycle. Which of the following methods would BEST assess the security of the product?
Question 274
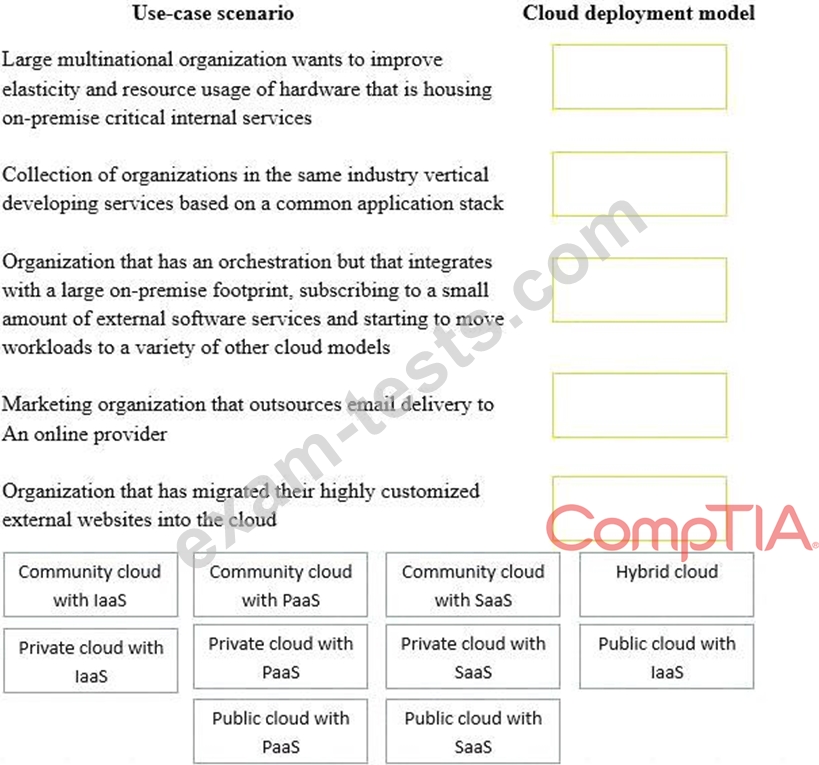
Drag and drop the cloud deployment model to the associated use-case scenario. Options may be used only once or not at all.

Question 275
An organization is considering the use of a thin client architecture as it moves to a cloud-hosted environment. A security analyst is asked to provide thoughts on the security advantages of using thin clients and virtual workstations.
Which of the following are security advantages of the use of this combination of thin clients and virtual workstations?
Which of the following are security advantages of the use of this combination of thin clients and virtual workstations?